Microsoft 365 Security Assessment Part 2
Last week I shared part one of my Microsoft 365 Security Assessment where we took a deep dive into...


As a Microsoft 365 certified Security Administrator, and Microsoft certified Azure Security Engineer I have recently done a number of Microsoft 365 security assessments. Some of them have been post-breach assessments. A lot of companies had to enable remote workers in a hurry at the start of the COVID-19 pandemic, and as a result have realized security configuration and protection is more critical than ever.
After the start of the pandemic, Microsoft released some guidance for enabling remote work securely – “Work remotely, stay secure—guidance for CISOs”
That blog post lists a bunch of products that Microsoft offers to help, but they are not listed in a step by step guide as to what to tackle first and how to move on to the next. What people are looking for is a partner that can give them recommendations or a list of configuration steps to secure their environments.
So, in this post, I aim to provide an actionable checklist for Microsoft 365 customers based on the experiences I’ve had doing security assessments.
With that, let’s get started on securing your environment:
Start with Azure Active Directory (Azure AD)
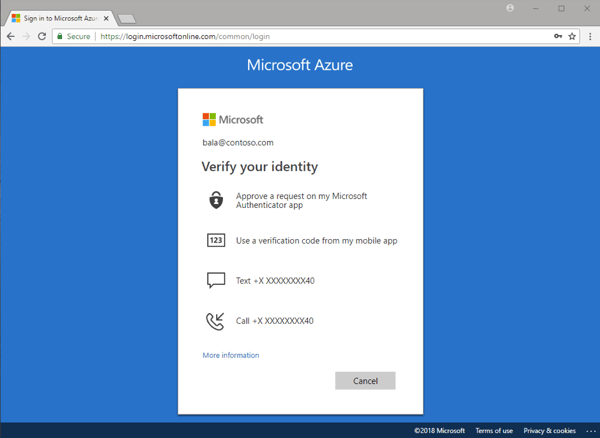 Figure 1: Multiple verification options
Figure 1: Multiple verification options
Multi-factor authentication is a process where a user is prompted during the sign-in process for an additional form of identification, such as to enter a code on their cell phone or to provide a fingerprint scan. An example is shown in Figure 1: Multiple verification options
Passwords are an insecure vector, vulnerable to attack. If the password is weak or has been exposed elsewhere, is it really the user signing in with the username and password, or is it an attacker? Azure Multi-Factor Authentication works by requiring two or more of the following authentication methods:
Everyone should register multiple verification methods, so that you can require MFA anytime a sign-in is deemed risky, either because you decide or the machine learning intelligence that Microsoft has decided it’s risky.
How-to-guide: Plan Azure MFA deployment
Self Service Password Reset (SSPR) is a feature available in AAD Premium P1 and above. It allows users to reset their passwords when they have forgotten the current password. The service is secure in that users must provide verification methods to prove they are who they say they are before they are able to reset their passwords.
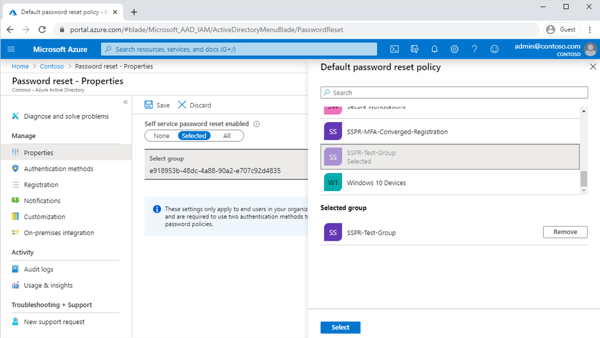 Figure 2: Self Service Password Reset (SSPR)
Figure 2: Self Service Password Reset (SSPR)
Tutorial: Enable Self Service Password Reset
When you enable this combined registration experience (shown in Figure 3: Combined security registration experience), users need only select their registration information once to enable both MFA and SSPR features.
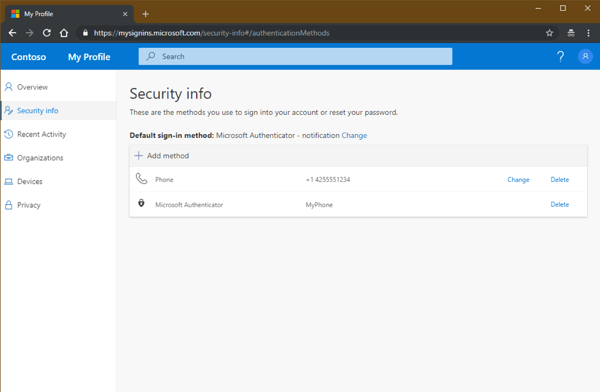 Figure 3: Combined security registration experience
Figure 3: Combined security registration experience
Enable the combined security information registration
Password hash synchronization is an extension to the directory synchronization feature implemented by Azure AD Connect sync.
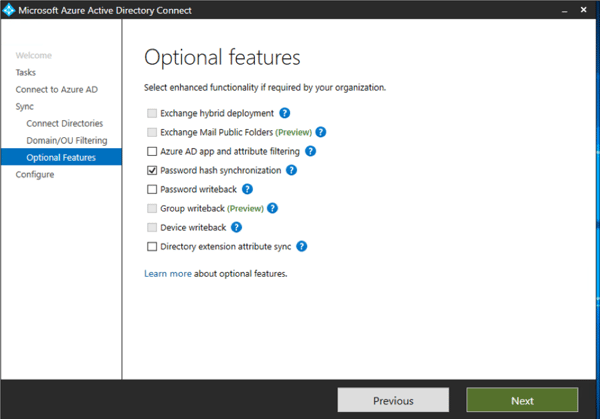 Figure 4: AAD Connect Optional features
Figure 4: AAD Connect Optional features
You can enable this optional feature in the Azure AD Connect wizard shown in Figure 4: AAD Connect Optional features. This will allow users to sign in to Azure AD services like Microsoft 365 by using the same password they use to sign in to your on-premises Active Directory instance. In Figure 5: Signing-in to SaaS apps using password from on-premises you can see how this makes things simpler for the user.
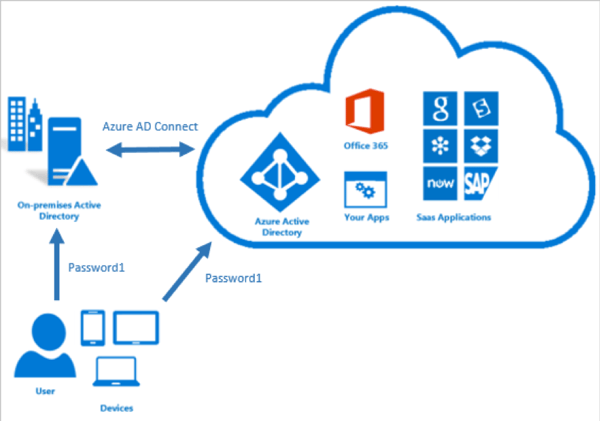 Figure 5: Signing-in to SaaS apps using password from on-premises
Figure 5: Signing-in to SaaS apps using password from on-premises
Password Hash Sync also gives you the ability to leverage password protection functionality, such as breach replay protection and leaked credential reports.
Tutorial: Enable Password Hash Sync (PHS)
Azure AD Password Protection detects, and blocks known weak passwords and their variants, and can also block additional weak terms that are specific to your company using custom banned passwords as shown in Figure 6: Custom banned passwords.
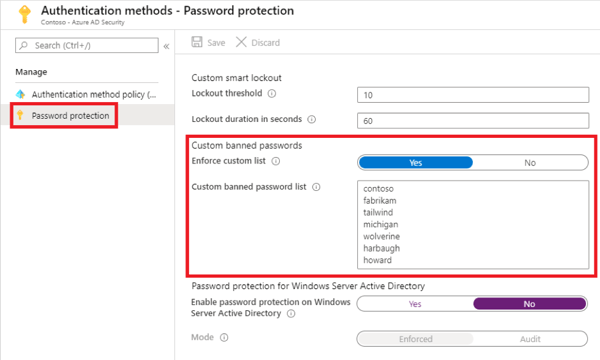 Figure 6: Custom banned passwords
Figure 6: Custom banned passwords
With Azure AD Password Protection, default global banned password lists are automatically applied to all users in an Azure AD tenant. You can define entries in a custom banned password list. When users change or reset their passwords, these banned password lists are checked to enforce the use of strong passwords as shown in Figure 7: Password blocked by banned password list.
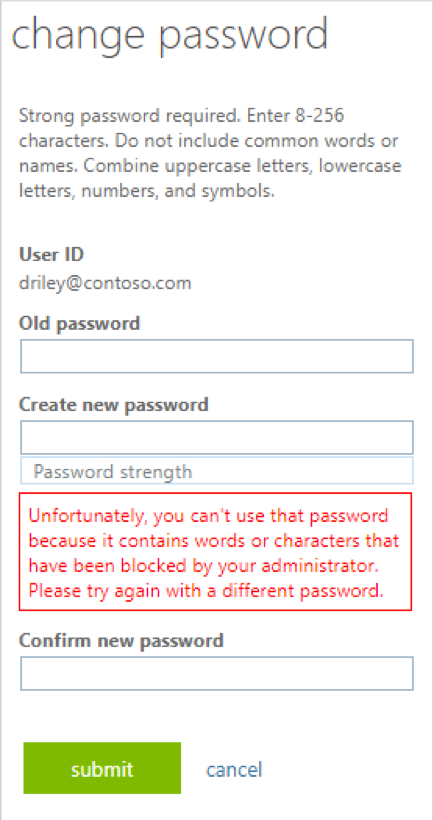 Figure 7: Password blocked by banned password list
Figure 7: Password blocked by banned password list
Tutorial: Configure banned passwords for AAD
Adding custom branding not only personalizes the sign-in pages to match your corporate identity but is also vital in securing your users against phishing and other identity attacks. Users should become accustomed to seeing the custom company branding and sign-in text. When a sign-in request doesn’t present the correct branding and sign-in texts, users should be suspicious of requests for supplying log-in credentials. This type of awareness needs to be communicated to employees.
 Figure 8: Custom image requirements for company branding
Figure 8: Custom image requirements for company branding
Before an application can access your organization's data, a user must grant the application permissions to do so. In Figure 9: User consent for applications options you can see that different permissions allow different levels of access. By default, all users can consent to applications for permissions that don't require administrator consent.
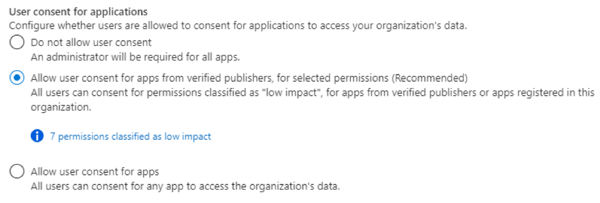 Figure 9: User consent for applications options
Figure 9: User consent for applications options
To reduce the risk of malicious applications attempting to trick users into granting them access to your organization's data, Microsoft recommends that you allow user consent only for applications that have been published by a verified publisher.
In addition, if you restrict users from consenting to apps, users will see a generic error message suggesting they contact the admin. Not all users know who to contact in this instance, so it’s advisable to enable the admin consent workflow feature which is currently in public preview.
The system then sends a notification to the delegated application admin user via email and the end user requesting the app is show a notification as shown in Figure 10: Admin request sent notification
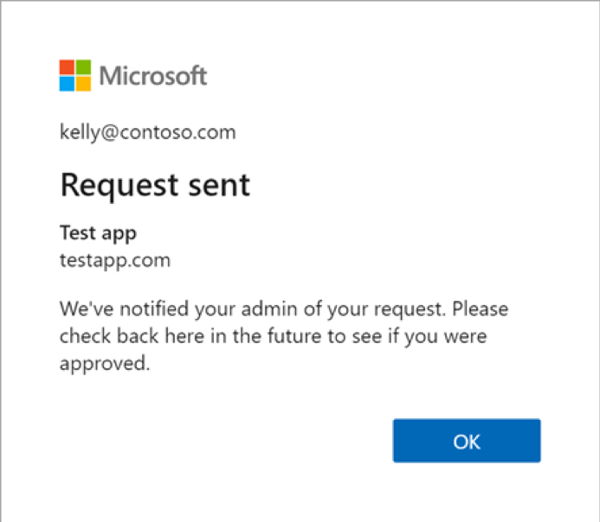 Figure 10: Admin request sent notification
Figure 10: Admin request sent notification
See more information about how the Admin consent workflow notifies an admin that a user has requested an app, in my blog post "App admin consent workflow – What is looks like in action"
Security defaults protect organizations with one master policy. Customers with the free or Office 365 versions of Azure AD are encouraged to use security defaults because they don’t have the granularity of Conditional Access policies. Security defaults essentially enable five policies in the background that protect the tenant:
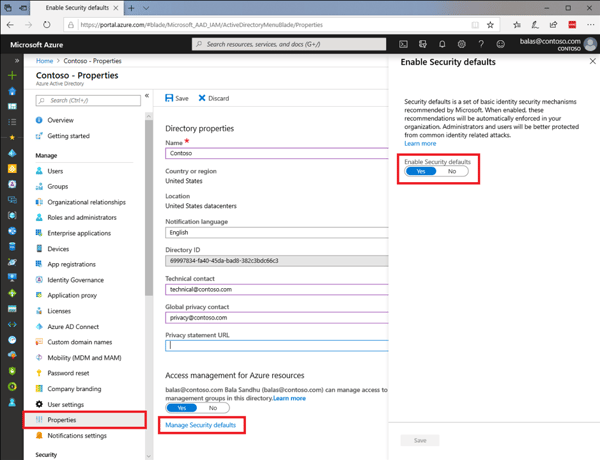 Figure 11: Security defaults master switch
Figure 11: Security defaults master switch
Security defaults gives you a balance of security and productivity without you having to create the security policies yourself.
MFA is a great way to secure your organization, but users often get frustrated with the additional security layer on top of having to remember complex passwords. Passwordless authentication is more convenient because the password is removed and replaced with something you have, plus something you are or something you know.
You may already be using the Microsoft Authenticator App as a convenient multi-factor authentication option in addition to a password. You can also use the Authenticator App as a passwordless option.
 Figure 12: Signing in without a password
Figure 12: Signing in without a password
Users can sign in by getting a notification to their phone, matching a number displayed on the screen (Figure 12: Signing in without a password) to the one on their phone, and then using their biometric (touch or face) or PIN to confirm.
Enable passwordless phone sign-in
Azure AD Identity Protection is a security module of Azure Active Directory that provides a consolidated view into risk detections and potential vulnerabilities affecting an organization’s identities.
Identity Protection uses the learnings Microsoft has acquired from their position in organizations with Azure AD, the consumer space with Microsoft Accounts, and in gaming with Xbox to protect your users. Microsoft analyses 6.5 trillion signals per day to identify and protect customers from threats.
The signals generated by and fed to Identity Protection, can be further fed into tools like Conditional Access to make access decisions.
Conditional Access is the tool used by Azure Active Directory to bring signals together, to make decisions, and enforce organizational policies.
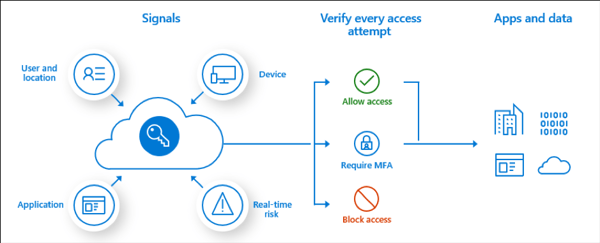 Figure 13: Conditional Access signals and actions
Figure 13: Conditional Access signals and actions
Conditional Access is at the heart of the identity driven control plane. Conditional Access policies at their simplest are if-then statements.
Multiple conditions can be combined to create fine-grained and specific Conditional Access policies.
For example, when accessing a sensitive application, an administrator may factor sign-in risk information from Azure Identity Protection and require more verification from the user.
If a user wants to access a resource, then they must complete an action. Example: A payroll manager wants to access the payroll application and is required to perform multi-factor authentication to access it.
Below are some common Conditional Access policies which many organizations are applying as a standard set of policies.
Check out this blog post by Daniel Chronlund where he lists 13 conditional access policies, he believes will meet the needs of most organizations. Azure AD Conditional Access Policy Design Baseline – Daniel Chronlund Cloud Tech Blog (danielchronlund.com)
When it comes to Microsoft 365 security tips, there’s a lot to cover. This week we walked through some actionable steps to help you manage Azure Active Directory. Keep an eye out for part 2 next week where I’ll dive into some security tips for the Microsoft 365 Admin Center!
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Microsoft Security MVP | Principal Architect @NBConsult | Speaker | Blogger. I am an Identity and Access Solutions Architect for NBConsult, a leading IT service provider in South Africa. I have 20+ years of experience in Microsoft enterprise technologies. I am passionate about Identity Governance and how it can help organizations achieve better security, compliance and productivity. I write blogs where I share my insights and tips on Application Governance.


Last week I shared part one of my Microsoft 365 Security Assessment where we took a deep dive into...