Microsoft 365 Security Assessment Part 2
Last week I shared part one of my Microsoft 365 Security Assessment where we took a deep dive into...

Last year I wrote "Microsoft 365 Security Assessment" Part 1 and Part 2, where I provided a list of actions one should perform or check in one’s Microsoft 365 environment as a security assessment.
Over the past year, significant changes have been seen in the threat landscape, threats impacting organizations of any size. With hybrid work, the attack surface has grown. Today I write this as a recap on my posts from last year (2020) but also to tell you about some of the enhancements Microsoft has made to it’s cyber-security features and products.
Since identity is at the foundation of a large percentage of security assurances, I always start with Azure Active Directory, or AAD, because that’s Microsoft’s cloud-hosted identity and access provider to most things in the Microsoft cloud, be it Microsoft 365, Azure or even Dynamics 365. I have seen some great new features and security related functionality rollout over the past year that I think needs discussing simply to bring awareness to them.
If you have not enabled MFA for all your users yet, stop reading this, go and enable it and come back. I’ll wait. . . . . . Really, it’s the single most effective way to “reduce” 99.9% of cyberthreats.
Enabled for all users now? . . . . . Good! Now that you’ve done that, there’s some bad news. The cyber criminals are getting smart to the MFA thing and there is such a thing as "not all MFA is equal" when it comes to security. You can read more about how MFA has failed in the real world in “All your creds are belong to us!” But there are some enhancements to combat the failures and so it’s not all doom and gloom.
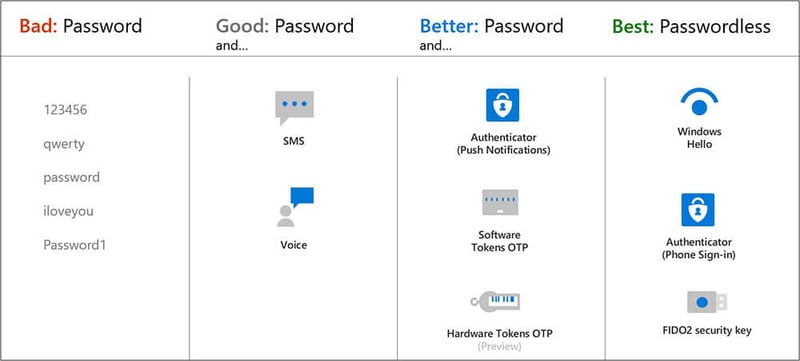
Like a latch on a public toilet stall, a username and just a password do not secure an account from compromise. MFA requires a username, password and one of the five other verification methods in the middle two columns (see Figure 1 above). SMS, Voice call, Authenticator push notification, software One Time Pins (OTP) and hardware tokens. The final column on the right shows passwordless authentication mechanisms which are ultimately our end goal.
SMS and Voice calls are on what is called “jackable” channels, which means the communication channel used for SMS and voice can be taken over or intercepted and replayed using a machine-in-the-middle. So, Microsoft has recently released a feature that will “nudge” your users who are already using MFA to use the Microsoft Authenticator if they are using less secure authentication methods such as SMS and Voice. This feature, codenamed “Nudge”, is simply referred to as “Registration campaign” and can be set in Azure AD > Security > Authentication Methods – Registration campaign. The idea of it being a campaign is that you run it for a period of time until you have the majority of your users using the Authenticator app, then you switch it off again so as not to bother those users who simply can’t use the authenticator app.
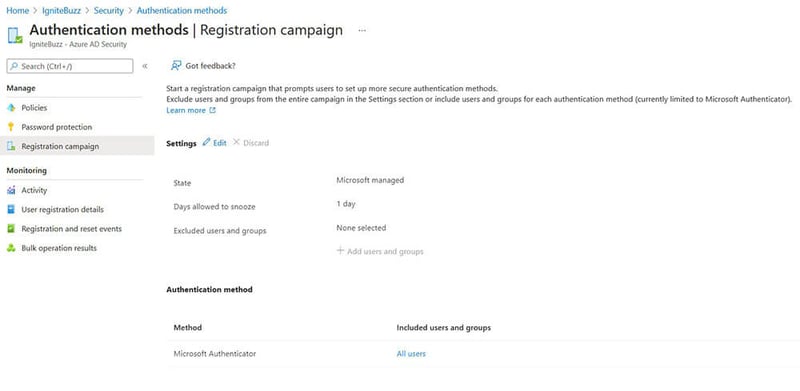
The users targeted by your campaign will authenticate as normal, provide MFA as normal but before being granted access will be prompted to “better guard your account with the Microsoft Authenticator app”. This is shown in the user experience picture below. It drives the user to register and use push notifications in the app rather than SMS or phone calls to their number.

The “not now” link allows the user to snooze this nudge for how ever many days the admin has set in the registration campaign.
This feature will not prompt users that already have the Authenticator app registered. It will also not remove the SMS and Voice options for users that get nudged into using Authenticator app.
The Microsoft documentation for the Registration Campaign can be found at How to run a registration campaign to set up Microsoft Authenticator - Microsoft Authenticator app.
By the way, the Microsoft Authenticator app recently got some new features too, allowing users to manage their enterprise accounts.
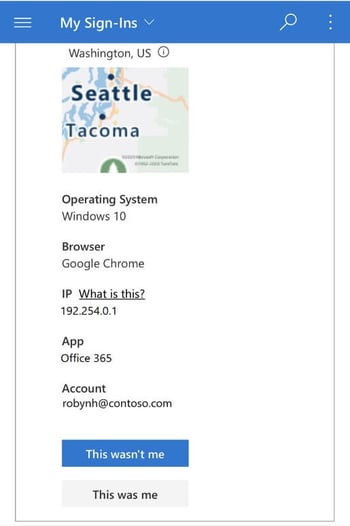
Users can change their password, change the authentication method, and even see recent sign-in activity and report something that looks suspicious, such as “This wasn’t me”. All from within the Authenticator App.
Still on the MFA topic, we’ve also seen “MFA fatigue” where users are being prompted for MFA too much. This introduces a risk that users just tap approve on their mobile app without knowing the context of the authentication attempt. This is what the criminals and bad actors call “grief”, spamming the user with many MFA requests in the hopes that the user will eventually approve one. From a security point of view, the way to mitigate this is to try to get the user to pause and cognitively engage with the authenticator app. So, Microsoft very recently introduced some preview features which I think will help in that regard.
The first is called “Number matching” which is where, when MFA is required, the user is presented with a number on the screen (not the mobile screen) which they then need to type into a field on the authenticator app. The prompt on the authenticator app is worded “Enter the number shown to sign in”. This contrasts with the current MFA push notification which prompts the user to verify or deny the request.
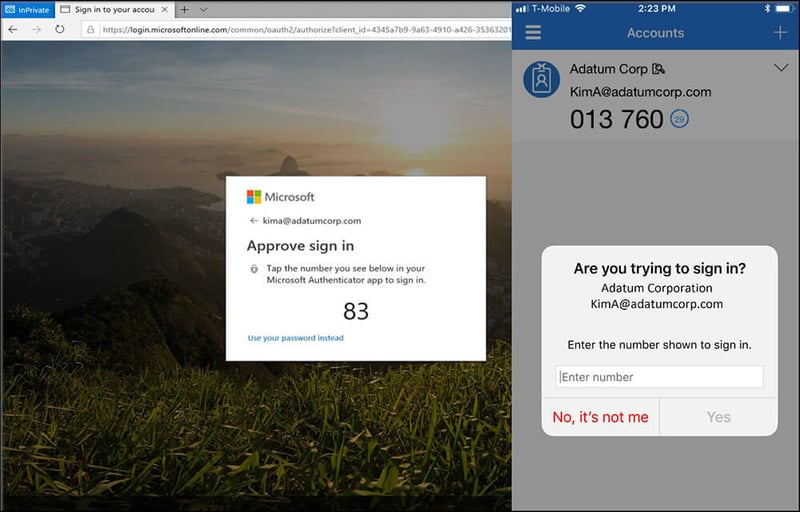
The second, is called "additional context", which is said to improve the security of user sign-in by adding the location of the application based on IP address of the sign-in. Additional context can, of course, be combined with number matching for even more enhancement.
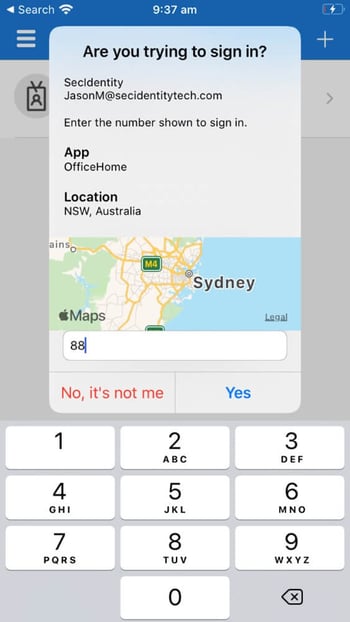
These new features also apply to users resetting their password using Self Service Password Reset (SSPR) – a feature I recommended last year.
Some of the new features I mentioned above require the combined registration experience be enabled for the targeted users. Last year I recommended enabling the combined registration experience for all users.
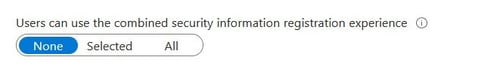
This is still a recommendation because it provides a single registration flow for both SSPR and MFA registration and it defaults the user towards using the Microsoft Authenticator app over SMS and voice methods. As of August 2020, new tenants will have the combined registration enabled by default for all users.
In August 2021, Microsoft released a new major version of AAD Connect, which is a new version of the same software but is built using the latest foundational components. This new major version is V2.0.
The foundational components referred to are:
My recommendation here is to upgrade your existing AAD Connect soon because all AAD Connect v1.x versions will be retired on 31st August 2022. Azure AD Connect v2.0 is not available for auto upgrade. You can perform either an in-place upgrade or a swing migration. Because v2.0 requires a minimum of Server 2016, if your existing AAD Connect server/s is 2012/2012 R2 then you will have to do a swing migration to a new server OS. Maybe you should consider this a good time to deploy an Azure server?
Conditional Access is part of Azure AD Premium, the paid-for version of Azure AD, and is the policy engine for identity in a Zero Trust deployment.
Conditional access brings signals together, makes decisions, and enforces organizational policies. This security policy enforcement engine analyzes real-time signals to make security enforcement decisions at critical checkpoints.
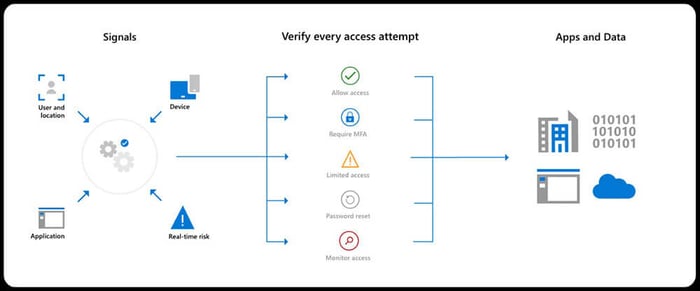
There are some great security enhancements in Conditional Access. If you are not paying for the premium version of AAD, your best bet is to enable Security Defaults.
For those with Conditional Access, there are some improvements in understanding the effectiveness of your policies, some templates to help you deploy some of the common conditional access policies, new device filters so you can target or exclude specific devices, and continuous access evaluation for near real-time enforcement when user conditions change.
The overview dashboard gives admins a summary of the policy’s state, (enabled, disabled, report-only) whether or not policies are being evaluated for sign-ins as well as some recommendations.
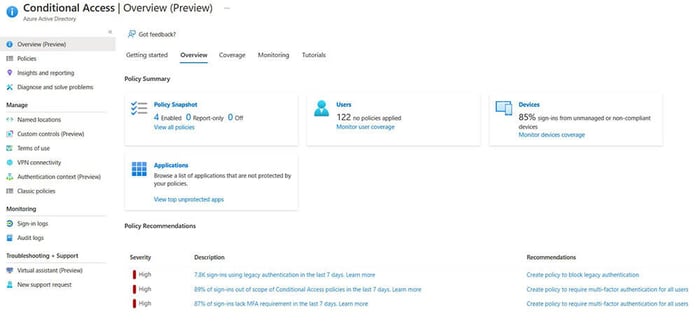
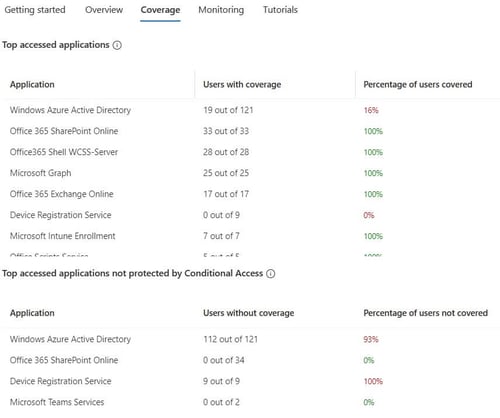
The “coverage” tab shows the top applications in use in the environment and whether or not CA policies are protecting those applications.
The “monitoring” tab provides visual analyses into how your policies are enforcing controls or not. These visuals can highlight a misconfiguration of a policy. There are a few filters and I suspect Microsoft will add more filtering capabilities as this feature matures.
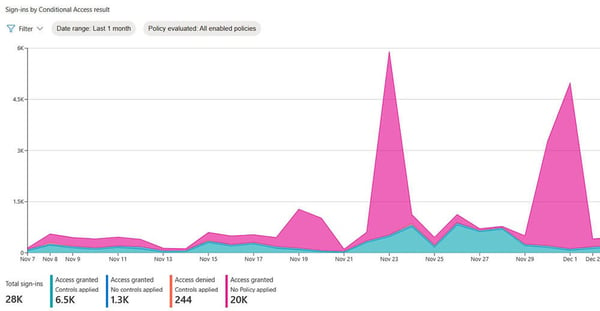
I have seen customers who have a block legacy authentication policy – as recommended last year – but they have misconfigured it or the exception list is too broad which leaves them at risk of password spray and brute force attacks. You can read more about my legacy auth findings in Still using Legacy Authentication???
With policy templates (preview), you can deploy 14 common policies aligned with Microsoft recommendations. The 14 policy templates are split into policies that would be assigned to user identities or devices.
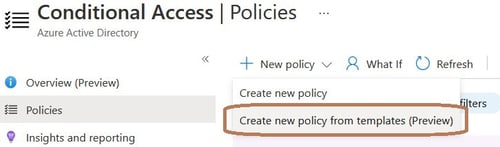
By default, each policy is created in report-only mode so you don’t break things, but show you the correct way to configure the conditions. You can look at the policy summary instead of creating the policy from template if you just wish to see the configuration. Say if you wanted to implement the policy yourself for example:
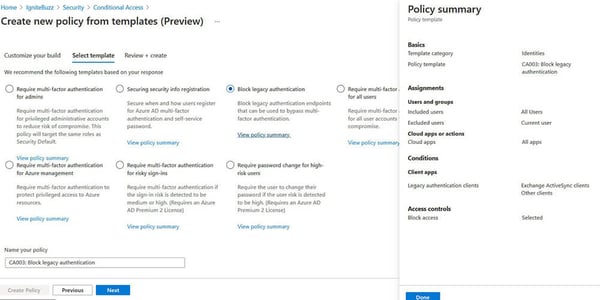
The templates even give you a suggested naming standard for your policies.
If you are implementing many Conditional Access policies, you might be interested in “Microsoft Azure AD Conditional Access principles and guidance”, a document on LinkedIn by Claus Jespersen, Principal Security Consultant at Microsoft.
Using Microsoft Graph and Conditional Access APIs and PowerShell, you can now treat Conditional Access policies like any other piece of code in your environment.
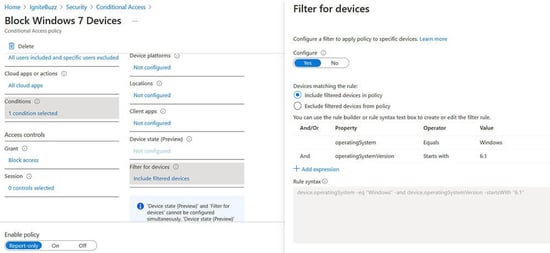
Now you can target specific devices using supported operators and properties for device filters and the other available assignment conditions.
Say for example you wanted to block access to organization resources from devices running an unsupported Operating System version like Windows 7. You would configure the “filter for devices” condition with an expression device.operatingSystem -eq "Windows" -and device.operatingSystemVersion -startsWith "6.1".
Continuous access evaluation is like a "conversation" between the token issuer (Azure AD), and the relying party (enlightened app). This two-way conversation gives us two important capabilities. The relying party can see when properties change, like network location, and tell the token issuer. It also gives the token issuer a way to tell the relying party to stop respecting tokens for a given user because of account compromise, disablement, or other concerns.
There are essentially two implementations of CAE: critical event evaluation and Conditional Access policy evaluation.
Critical event evaluation is available in all tenants and there is no configuration required. The following events are automatically monitored for:
Continuous access evaluation is auto enabled as part of an organization's Conditional Access policies.
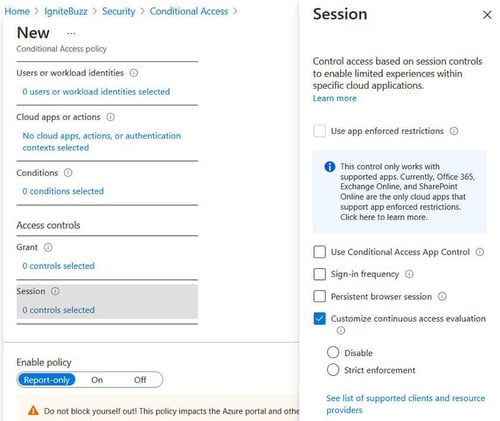
Continuous Access Evaluation (CAE) allows access tokens to be revoked based on critical events and policy evaluation in real time rather than relying on token expiration based on lifetime.
Continuous access evaluation policies can be scoped to all users or specific users and groups.
CAE in Conditional Access policies is configured under “Session control”:
As a result of recent nation-state cyberattacks that compromised the supply chain of SolarWinds [in which criminals were able to gain the ability to create SAML tokens that they then used to access the cloud environment], Microsoft has introduced proactive detections for token theft and anomalous tokens into AAD P2’s risk-based feature Identity Protection which provide real-time intelligent risk assessment:
The SolarWinds attack is now being referred to as NOBELIUM.
Microsoft will soon be adding Linux support to Microsoft Endpoint Manager. This means you will be able to use conditional access policies to ensure these endpoints are compliant for secure access to company resources. See Unified cloud management for Linux | Microsoft Endpoint Manager Blog for more information.
Most organizations believe that having a Conditional Access policy enabled to block legacy authentication is sufficient. The reality however is that organizations are still at risk if those legacy protocols are still enabled.
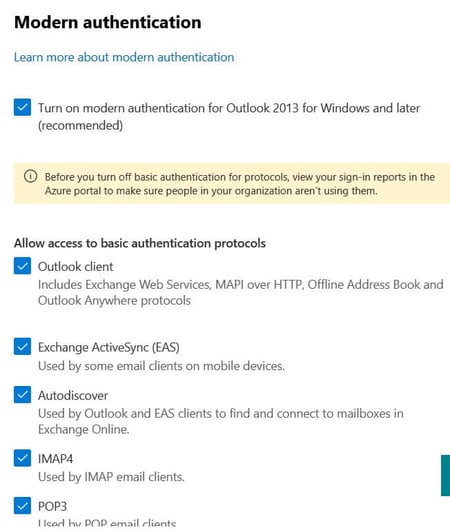
Effective October 1, 2022, Microsoft will begin disabling Legacy authentication for Outlook, EWS, RPS, POP, IMAP, and EAS protocols in Exchange Online - Deprecation of Basic authentication in Exchange Online | Microsoft Docs.
In the meantime, you should make sure modern authentication is enabled and disable basic (legacy) authentication for the Exchange online protocols if they are not legitimately in use. The link to access the configuration shown in the image below is: https://admin.microsoft.com/#/Settings/Services/:/Settings/L1/ModernAuthentication
Secure score is still a great Cloud Security Posture Management (CSPM) tool that gives you visibility about your current security situation and guidance to help you improve your security. Microsoft Secure score is now incorporated into the new Microsoft 365 Defender portal.
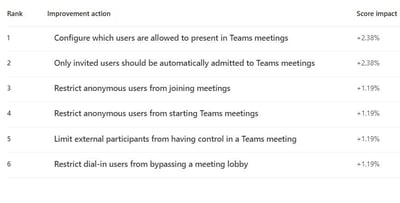
In January 2021, Microsoft introduced the first security recommendation for Microsoft Teams and in July 2021 introduced an additional 5 recommendations related to Teams. These 6 Teams related recommendations are shown in the diagram below:
It is also possible to integrate Defender for Endpoint into Secure Score and therefore you will get device-related recommendations:
Some of the device recommendations that will then surface in Secure Score are:
I have seen a couple of instances where customers have gamed their Secure Score to reflect a great score, but they are still at risk. Secure Score allows an admin to mark the recommendation as “Resolved through third party” and “Resolved through alternate mitigation”
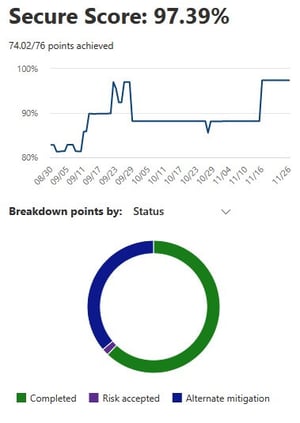
You'll gain the points that the action is worth, so your score better reflects your overall security posture, but if you are not actually implementing another way of mitigating the risk, the Secure Score tool will not check up on you for that recommendation. So, you are still at risk even with a great looking score.
Microsoft has rebranded a lot of security products with the “Defender” brand, in an effort to bring all its security offerings under a simpler naming scheme. While renaming may be cosmetic, functionality is important and there have been some new functionality additions too.
Historically, the Microsoft Defender Security Center (https://securitycenter.windows.com) has been the home for Microsoft Defender for Endpoint. Enterprise security teams have used it to monitor and help responding to alerts of potential advanced persistent threat activity or data breaches.
Defender has a new portal experience. The improved Microsoft 365 Defender portal went generally available in April 2021. This new experience brings together Defender for Endpoint, Defender for Office 365, Defender for Identity, and more into a single portal.
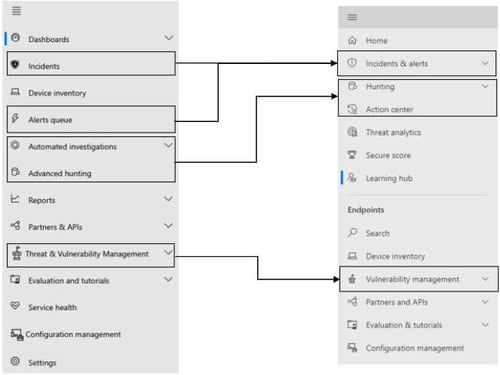
This single portal brings protection, detection, investigation, and response to threats from:
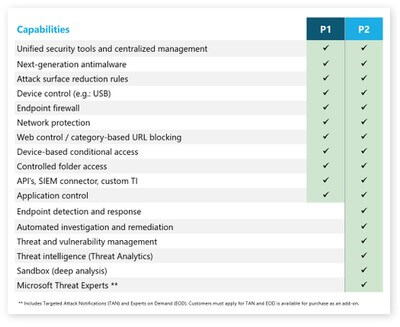
Up until August 2021, Defender for Endpoint was only available as an expensive add-on or included in the full Microsoft 365 E5 license SKU. In August however, Microsoft announced the preview of Defender for Endpoint Plan 1 which is a subset of the capabilities in the full-fat Defender for Endpoint product included in Microsoft 365 E5 (which is now known as Defender for Endpoint Plan 2 . . . . go figure).
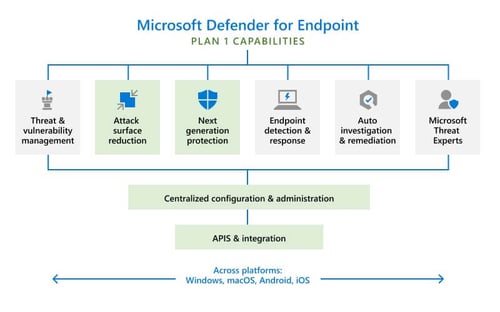
If you are on a Microsoft 365 E3 or A3 (not E5 or A5) you can sign up for the preview program of MDE Plan 1 - https://aka.ms/mdep1trial. Starting next year, Microsoft Defender for Endpoint P1 will be included as part of Microsoft 365 E3/A3 and all existing Microsoft 365 E3/A3 customers will have access to MDE P1. Yay!
MDE P1 became generally available in November 2021 - https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoft-defender-for-endpoint-plan-1-now-generally-available/ba-p/2966231.
If you have 300 users or less, don’t feel left out, because in November 2021, Microsoft announced “Protection for everyone” or Microsoft Defender for Business. Defender for Business will be available both as a standalone solution and as integrated protection included within Microsoft 365 Business Premium. This allows SMBs to leverage next-generation protection, endpoint detection and response, and threat and vulnerability management baked into the Defender suite.
In other Defender news:
Keeping in theme with the Defender rebranding, just to summarize:
If you are using Azure services, the Defender for Cloud has “plans” to add defences for the compute, data, and service layers of your Azure environment:
Oh, and Azure Sentinel is now called Microsoft Sentinel and has a 31 day free trial!
There you have it, what I thought was going to be another checklist, ended up being a catch up on the new features and names for things. Hopefully this gives you some direction as to which products and services to adopt in your tenant.
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Microsoft Security MVP | Principal Architect @NBConsult | Speaker | Blogger. I am an Identity and Access Solutions Architect for NBConsult, a leading IT service provider in South Africa. I have 20+ years of experience in Microsoft enterprise technologies. I am passionate about Identity Governance and how it can help organizations achieve better security, compliance and productivity. I write blogs where I share my insights and tips on Application Governance.


Last week I shared part one of my Microsoft 365 Security Assessment where we took a deep dive into...


As a Microsoft 365 certified Security Administrator, and Microsoft certified Azure Security Engineer