How Microsoft Improved Its Identity Products & Services - August 2022
Microsoft’s identity portfolio is huge and includes products and services like Active Directory, AD...


Microsoft’s identity portfolio consists of many products, like Active Directory, AD FS, Azure AD Connect, Defender for Identity, Microsoft Identity Manager and Azure AD. Many organizations utilize these products and services in a Hybrid Identity setup. While it looks like Azure AD sees 3 changes per day on average, Microsoft’s on-premises products also see changes. More than 3, actually, this month:
Windows 11 2022 Update
Last month, Microsoft introduced an entirely new Operating System version. The new “Windows 11 2022 Update” was previously known as Windows 11 22H2 and enforces new security features to Windows 11 to make it even more tamperproof. DNS Hardening, Credential Theft Protection, Attack Surface Reduction and Account Lockout settings are examples of the new functionality that has been introduced. The Windows 11 22H2 Security Baseline provides information how to implement them all.
On Tuesday, September 13, 2022, Microsoft issued updates to address 63 vulnerabilities in its products. Microsoft refers to these updates at the ‘9B’ updates. With these updates, Microsoft addressed two noteworthy vulnerabilities in Kerberos.
CVE-2022-33647 and CVE-2022-33678 describe Elevation of Privilege (EoP) vulnerabilities in the Windows implementation of Kerberos. Through an Adversary in the Middle (AitM) attack, an attacker can downgrade the encryption to RC4-md4. As these encryption algorithms have severe vulnerabilities, the attacker could crack the user’s cypher key and compromise the Kerberos session to elevate privileges toward SYSTEM privileges.
Specifically for the latter vulnerability, the user account must have the Do not require Kerberos preauthentication option enabled and must have a configured RC4 key. This option is not enabled by default it can be enabled manually on Active Directory objects:
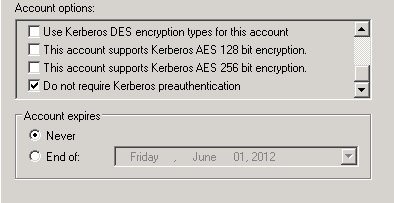
During Patch Tuesday, Microsoft also addressed these two Identity-related vulnerabilities. Organizations who already had the 10-year-old Kerberos Armoring functionality enabled weren’t vulnerable. A lot of Active Directory admins still manage Active Directory like it’s 2003, but Active Directory has had its share of security improvements in the past two decades. These two vulnerabilities show it’s smart to implement them.
A new Group Policy is introduced in Preview last month, when using Windows 10, Windows 11, Windows Server 2019 and/or Windows Server 2022. This new Group Policy setting enables or disables Microsoft HTML Application (MSHTA) files. As this type of files can be abused by attackers, it’s a useful introduction. We can expect this Group Policy setting to roll out on the aforementioned systems with the October Patch Tuesday updates.
Unfortunately, the September 13, 2022, updates introduced an issue with Group Policy. If, in a Group Policy Preference targeted at the User Configuration, a file is (over)written, the Group Policy service would merely write an empty file. The solutions for this issue range from unchecking the Run in logged-on user’s security context (user policy option) option, changing the Action from Replace to Update, and deleting the trailing \ when wildcards are used in file names.
With its September 13, 2022, and September 20, 2022, Preview updates, Microsoft addressed a couple of functional issues in Active Directory. These updates for Window Server 2019 and Windows Server 2022 address unexpected restarts on read-only Domain Controllers.
In the Windows Server 2022 Preview update for September 2022, Windows Hello for Business received an upgrade, because Microsoft introduced the WebAuthN Redirection feature. This feature lets people authenticate without a password within Remote Desktop Protocol (RDP) sessions. This way, it allows for using Windows Hello for Business sign-in methods, including Windows Hello for Business security keys, such as FIDO2 keys, when signing in from Windows 10 21H2+ or Windows 11-based devices. This feature is also expected to roll out with the October Patch Tuesday updates, but you can test it now in Preview on select systems.
The 2.191 release of Defender for Identity that Microsoft released on September 19, 2022, improve on the actions that trigger Honeytoken alerts. Now, any LDAP or SAMR query against any configured Honeytoken account triggers an alert. Also, changes to attributes and group memberships for configured Honeytoken accounts now result in triggered alerts.
In addition to alerts, Defender for Identity also provides information on typical misconfigurations. A new unsecure domain configuration was added to this list in the 2.190 release of Defender for Identity on September 11, 2022. The LDAP signing configuration is now examined. If it doesn’t require signing, it will be flagged. LDAP signing may require reconfiguration of current LDAP non-S traffic, but luckily Defender for Identity already reports these as unsecure, too.
When Active Directory admins with E5 licenses have not yet made work of eliminating LDAP non-S from their environments, their Identity Secure Score just dropped a couple of more points. Gotta catch ‘em all!
As Microsoft introduced their Multi-Factor Authentication Server Migration Utility with Azure MFA Server 8.1.1.1 last month, nothing is keeping organizations from moving to Azure MFA. On September 30, 2022, Microsoft announced the end of the line for this product. Beginning September 30, 2024, Azure MFA Server authentication requests will no longer be serviced.
If you have one or more Azure MFA Server installations running, it’s time to begin the migration as there is only 2 years of functionality left in this product.
Some Microsoft products and services are reaching the end of the line. Microsoft Identity Manager is not one of them, as this product just got an extended lease on life all the way through to January 9, 2029. That means, Microsoft intends to provide slightly over 13 years of support on their product to synchronize identities between multiple sources and providers.
This month really touched core Identity systems on-premises. AD FS servers and AD CS-based Certification Authorities (CAs) remained unscathed in terms of vulnerabilities. I hope this means that many admins will have time to actually patch their Internet-connected Exchange Server installations…
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Sander's qualities extend beyond the typical triple-A stories in the area of Identity and Access Management. Of course, authentication, authorization and auditing are necessities but my out of the box solutions get the most out of software, hardware and the cloud. Rapid technological advancements have resulted in cutting-edge solutions around Active Directory, Azure Active Directory and Identity Management. Keeping up with these is just a small challenge, compared to my true goal: helping people use the technology on a daily basis. In a way that ICT is not a mere hurdle, but an infinite enabler. His work as a consultant, blogger and trainer are all means to achieve this goal. His multiple Microsoft Most Valuable Professional (MVP) status, Veeam Vanguard status and extensive certification aids him. Through direct communications with the product teams in Redmond, he remains up to date, exchanges feedback and accelerates support. Sander is also a Virtual Product Owner for AppGov and ENow.


Microsoft’s identity portfolio is huge and includes products and services like Active Directory, AD...


Active Directory, AD CS, Azure AD Connect, and Azure MFA Server are all Microsoft on-premises...