Getting Serious with Active Directory and Entra ID in the Second Half of 2023
Brace yourselves! In the coming months, Microsoft is planning another round of Windows server...

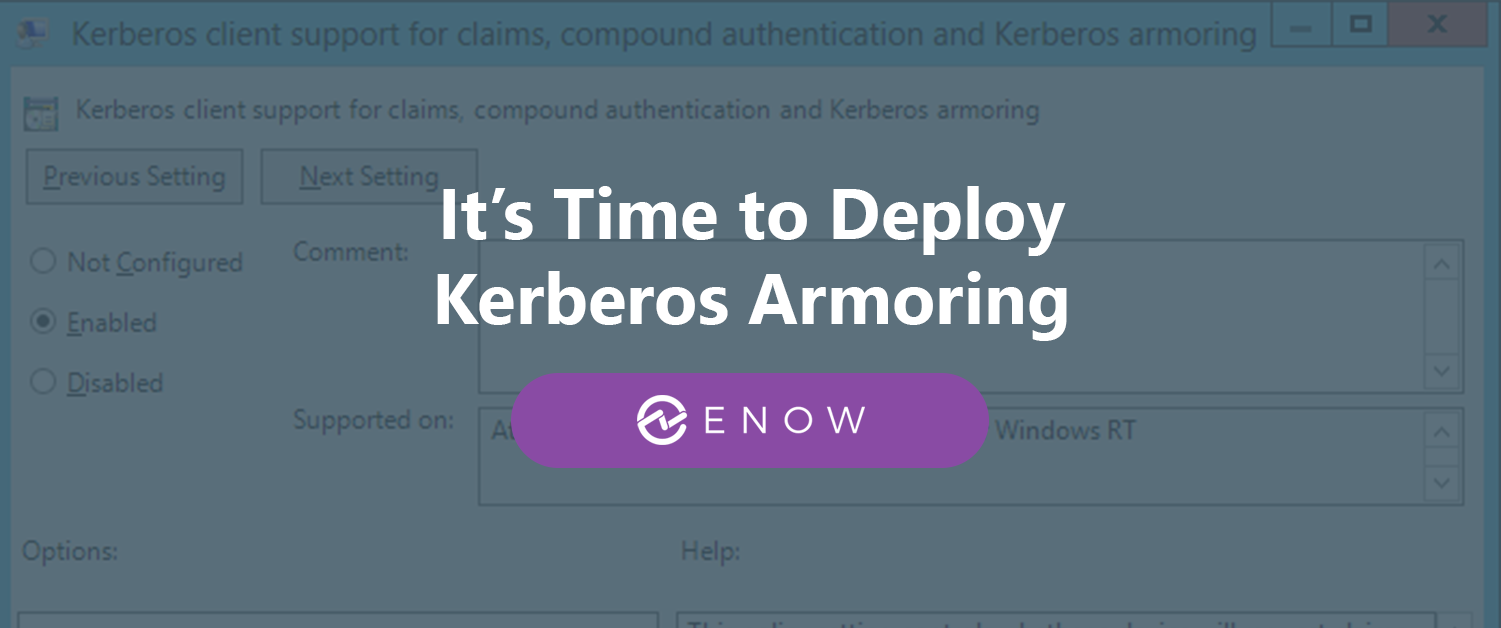
It doesn’t matter whether you refer to it as Kerberos Armoring, Flexible Authentication Secure Tunneling (FAST), RFC4581, RFC6113, or Kerberos pre-authentication… it is time to deploy it in your Active Directory environments.
Note:
EAP-FAST is the authentication method described in RFC4581. Kerberos Armoring is Microsoft’s implementation of this standard.
Kerberos Armoring is a security feature in Active Directory Domain Services that was introduced with Windows Server 2012. This new feature solves common security problems with Kerberos and also makes sure clients do not fall back to less secure legacy protocols or weaker cryptographic methods.
Kerberos Armoring is part of the framework for Kerberos Pre-authentication. According to the RFC, it provides a protected channel between the client and the Key Distribution Center (KDC). In Active Directory speak, a KDC is a domain controller. When enabled, it can deliver key material used to strengthen the reply key within the protected channel.
With Kerberos Armoring in place, it is relatively straightforward to chain multiple authentication mechanisms, utilize a different key management system, or support a new key agreement algorithm. With Kerberos Armoring enabled and required, brute forcing the reply key is no longer possible and the highest possible cryptographic protocols and cipher strengths are guaranteed to be used by Windows-based clients in their pre-authentication traffic with Windows Server 2012-based Domain Controllers (and up).
In the September 2022 cumulative updates for all supported Windows Server versions, two vulnerabilities were addressed in Windows Kerberos, that could lead to successful Adversary in the Middle (AitM) attacks and subsequent SYSTEM privileges, when Kerberos Armoring is not enabled:
For CVE-2022-33679, specifically, for a user object to be vulnerable its Do not require Kerberos preauthentication option needs to be enabled and must have been configured with a RC4 key.
Both vulnerabilities are addressed with the September 2022 cumulative updates, but these vulnerabilities tell a cautionary tale to all Active Directory admins, that their Active Directory is (and remains) exposed to many flaws in both the Kerberos protocol and Microsoft’s implementation of Windows Kerberos. Kerberos was never envisioned to be used the way we use it today.
To be able to use Kerberos Armoring, the following requirements need to be met:
Enabling Kerberos Armoring consists of changes to all the domain members and changes on the domain controllers. The best way to do so in my opinion is using Group Policy.
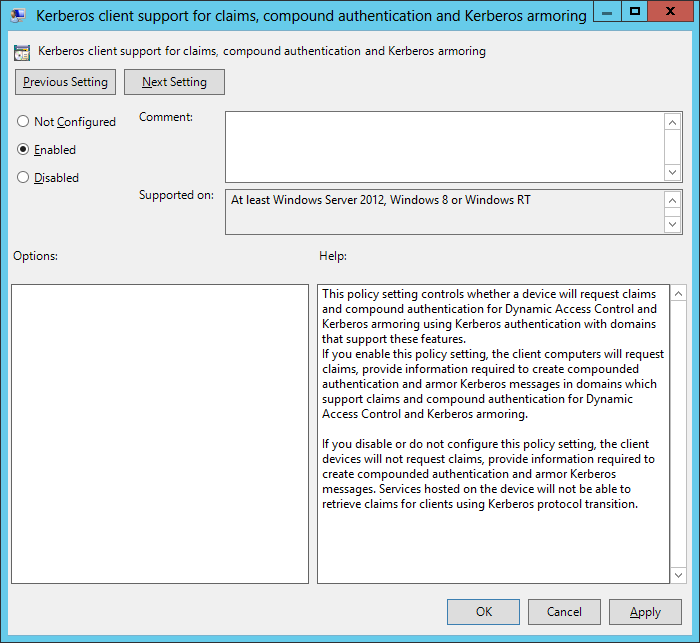
ENABLING KERBEROS ARMORING ON DOMAIN MEMBERS
To enable Kerberos Armoring on all domain members, perform these steps:
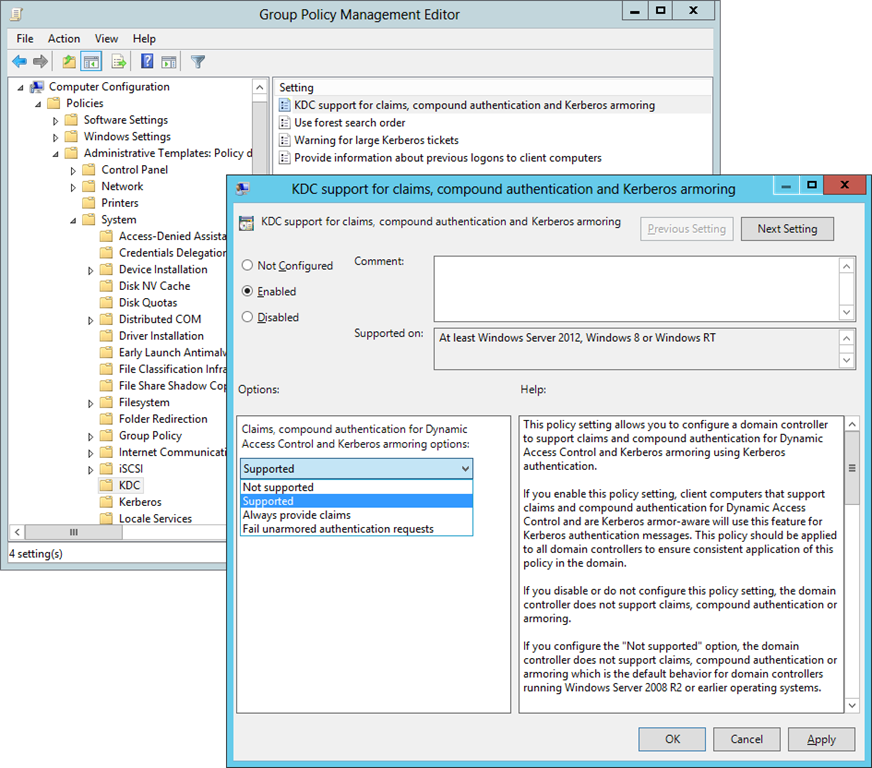
REQUIRING KERBEROS ARMORING FROM THE DOMAIN CONTROLLERS
To require Kerberos Armoring from the Domain Controllers, perform these steps:
Kerberos v5 originates in 1993 and was envisioned as a protocol for safe networks. Any admin who has ever experienced a ransomware attack can tell you that there is no such thing as a safe network. Now is the time for Active Directory admins to effectuate this sentiment and harden domain controllers.
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Sander's qualities extend beyond the typical triple-A stories in the area of Identity and Access Management. Of course, authentication, authorization and auditing are necessities but my out of the box solutions get the most out of software, hardware and the cloud. Rapid technological advancements have resulted in cutting-edge solutions around Active Directory, Azure Active Directory and Identity Management. Keeping up with these is just a small challenge, compared to my true goal: helping people use the technology on a daily basis. In a way that ICT is not a mere hurdle, but an infinite enabler. His work as a consultant, blogger and trainer are all means to achieve this goal. His multiple Microsoft Most Valuable Professional (MVP) status, Veeam Vanguard status and extensive certification aids him. Through direct communications with the product teams in Redmond, he remains up to date, exchanges feedback and accelerates support. Sander is also a Virtual Product Owner for AppGov and ENow.


Brace yourselves! In the coming months, Microsoft is planning another round of Windows server...


Compromised Domain Controllers are every Active Directory admin’s nightmare. However, Domain...