Active Directory Monitoring: Backup and Recovery - Options for AD CS
In the previous article we looked at the operations and processes regarding backup and recovery of...


In Part 2 of this series, we'll discuss backup and recovery options for Active Directory Domain Services (AD DS) as a critical component of Active Directory Monitoring. AD DS stores information about the objects on your networks such as user accounts, passwords, user information such as phone numbers, addresses, etc. This information allows users to be authorized on your network to access information. Every organization, large or small, should be backing up this information to restore in the event of any loss of data. This article will cover Windows Backup technologies, tools, and processes for keeping this data intact for restore.
[Applies to Windows Server 2016, Windows Server 2012 R2, Windows Server 2012, Active Directory, Active Directory Monitoring]
A lot of the backup products you see today use the Volume Shadow Copy Service (VSS) infrastructure that is found in Windows Server 2003 R2 and later operating systems. What VSS does is it creates a shadow copy. The backup is performed at the disk-block level on a volume that freezes at a specific point in time. This allows changes to be made to this disk while the backup is occurring however the changes to the disk will not be backed up until the next backup cycle.
When you create a shadow copy, it will tell the operating system to put files, such as the AD DS database files, in a consistent state. VSS will create a shadow copy that freezes the file at a certain point in time and allows the database to have changes written to it. Then as the data changes over time, it will overwrite the previous data.
If you are ever working with some older applications that are not VSS-aware, you can use streaming backups. This means that the application itself is responsible for keeping the data in a consistent state.
Windows Server Backup is an MMC snap-in and is installed as a feature in Server operating systems. Windows Server Backup can be used to back up a full server, only selected volumes, or only specific items like folders or System state. It also allows you to:
- Perform a bare-metal recovery. This allows administrators to restore critical volumes without having to first install an operating system. It will allow you to restore an entire server or computer image to brand new hardware.Azure backup is another option if you would rather backup your servers to the Azure cloud. Azure backup uses a lightweight tool known as the Microsoft Azure Recovery Services (MARS) agent. When this agent is installed, it will help protect your files and folders, as well as any server configuration information in the Windows Server System State.
In order to use this option, you must have an Azure tenant and accounts with the proper permissions to create a Recovery Services vault to store the backups and to deploy and install the agent on your servers. To complete the setup, you must perform the following:
- Create a Recovery Services vaultFor more information on the Azure backup and recovery processes:
Tutorial - Back up Windows Server to Azure - Azure Backup | Microsoft Docs
Tutorial: Recover items to Windows Server - Azure Backup | Microsoft Docs
System Center Data Protection Manager is a Windows server and client enterprise backup and recovery system that allows you to backup and restore:
- Applications such as SQL Server, Exchange, and SharePointData Protection Manager allows administrators to store their backup data to disk or disk pools, Azure for offsite storage to the Microsoft Azure cloud, or tape backup devices.
Note: Tape backups are not recommended, however we are aware that many enterprises still use them for certain business continuity and disaster recovery situations.
In order to back up and restore AD DS, you will need to back up the System state and all critical volumes. Most administrators would recommend full server backups if the backups are not too large in size. Your Active Directory monitoring solution should be looking for two event IDs: Event ID 4 and Event ID 14. Event ID 4 should be monitored because it notifies you when a Windows backup is successful. Whenever a backup is run, successful or failed, event ID 14 is generated. The data for this ID contains the overall status of the backup in the field 'HRESULT'. This will show 0 for a successful Windows backup, and non-zero otherwise.
When it comes to restoring your AD DS data, you are presented with many different options. AD DS databases can become corrupted, damaged, or can just fail without warning. In order to restore the AD DS information, you are going to need to have full access to the files on your domain controller. The restore must be carried out in Directory Services Restore Mode (DSRM). Restart your domain controller and press F8 from the startup menu. Select DSRM from the menu. You will be presented with a sign in screen. You must sign in as Administrator and use the DSRM password that was created when the domain was spun up.
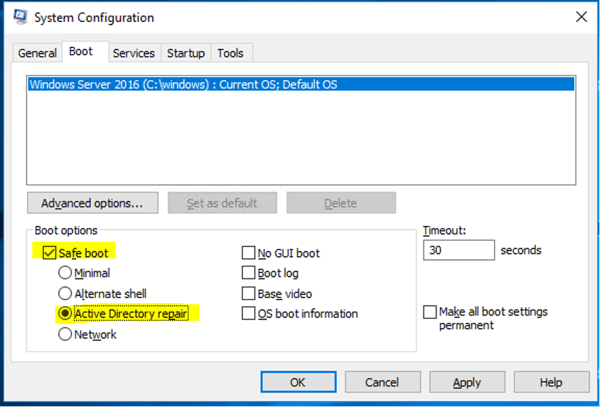
You will now have the ability to restore the directory database with Windows Server Backup. When the restore is complete you will need to restart the domain controller. The DC will then catch up with the rest of the domain controllers using replication from its partners. All changes made in the domain will be updated in the newly restored database. You may know this as a nonauthoritative restore. Administrators like to use this option where a domain controller has been damaged or corrupted, but has not spread to other domain controllers.
But what about when corruption or damage to the AD DS database has spread to other domain controllers and has replicated throughout your topology? This is where you will need to perform an authoritative restore. An authoritative restore is when you must restore a known good copy of the database and replicate it to other domain controllers to overwrite the bad databases. The process is similar to a nonauthoritative restore; however, you need to mark the deleted or corrupted objects that you wish to retain to ensure they are replicated back to all the other domain controllers. This process ensures that the object’s attribute version number is as high as possible to ensure the object is written back to the bad databases, which would have lower version numbers than the restored database and its objects.
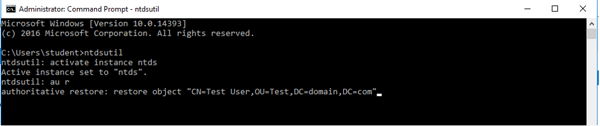
How do you mark objects as authoritative? You must use the NtdsUtil.exe tool at the command prompt. You will need to run the following commands, each on their own line:
Ntds.Util.exe
Activate instance ntds
authoritative restore or au r
restore object "object DN"
The object DN is the distinguished name of an object that you wish to be restored. An example would be restoring a user object that was deleted. The user object with the name “Test User” that was in the Test OU in the domain “domain.com” would look like this:
restore object “CN=Test User,OU=Test,DC=domain,DC=com”
Let’s take this one step further. What if we needed to restore an entire OU or container (this would include all child OUs and child objects as well)? It is almost the same commands as previously shown, but with a small change is the last line. Instead of the word “object” we will use “subtree”:
NtdsUtil.exe
Activate instance ntds
authoritative restore
restore subtree "object DN"
From here you can restart the domain controller. The domain controller will replicate from its partners bringing over any changes made since the database has been offline, but the authoritative changes will be replicated to its replication partners.
The last option to restore the directory service is to restore the entire domain controller. In order to complete this operation, you need to start the Windows Server in Windows RE (Recovery Environment). From there you will need to restore a full server backup of the domain controller. The default setting would be a normal restore with the restored database replicating from its partners. If you need to mark any objects as authoritative you will need to restart the server in the DSRM and mark the appropriate objects. This will need to be done prior to restarting the DC back into normal operation.
You do have the ability to restore the System state to a different location in the event you would like to examine files, and to possible mount the Ntds.dit file. Whatever you do be sure to NOT copy the files from an alternate location to the production location of the files. It is also not possible to do a disjointed restore of AD DS. If you wanted to create a new domain controller, you can use the copied files to support an Install From Media option.
Please continue to the next article: AD Best Practices - Backup and recovery Part 3 - Backup and Recovery Options for AD CS to learn about backing up, restoring, and configuring your Active Directory monitoring solution for Active Directory Certificate Services.
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Jonathan is an Information Technology consultant and instructor that specializes in migrations, security audits, new Microsoft technology implementations, and support contracts for Microsoft technologies. Jonathan also has expertise in Office 365 Services including, but not limited to, Azure Active Directory, Exchange Online, Skype for Business/Teams, SharePoint Online/OneDrive, Microsoft Azure/Office 365 Security and Compliance features including alerts, permissions, information classification, data loss prevention, information governance, threat management, data privacy, and reporting.


In the previous article we looked at the operations and processes regarding backup and recovery of...

This is a 5-part series discussing how to backup and restore objects for Active Directory modules...