Hybrid Headaches: The Confusing Case of Cross-Forest Delegation
If you've ever participated in an Exchange Online migration at almost any level, it's likely you've...


One situation I see often with customers is the desire to control and monitor file downloads from the cloud. For most organizations in most industries, it’s important to control your organization's data, and that data is often contained in files. The proprietary nature of information in files makes them very valuable to many organizations, and thusly important to control.
In this blog post, I’m going to start looking at the features that Microsoft Defender for Cloud Apps has available to help your organization better control and monitor file downloads.
Microsoft Defender for Cloud Apps (DCA) makes monitoring and applying some control over mass downloads very easy to start.
The DCA portal can be accessed at portal.cloudappsecurity.com.
To quickly get started with monitoring mass downloads by a single user, Microsoft has provided a simple to use template:
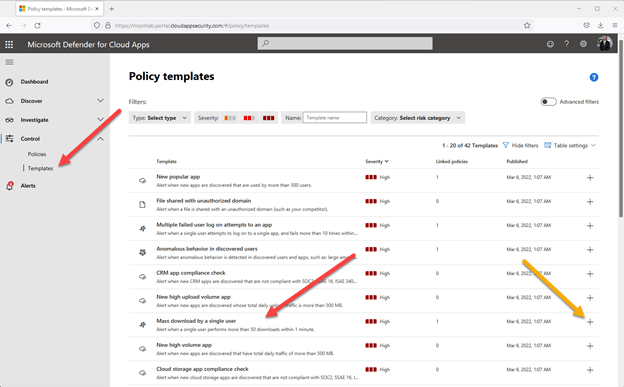
Figure 1 – DCA portal for templates
In the figure above, you can see I have navigated to Control > Templates and located the default template called “Mass download by a single user.” The green arrow points to the “+” button to use this template.
Using the “+” button will launch a wizard to create a new activity policy based on the template:
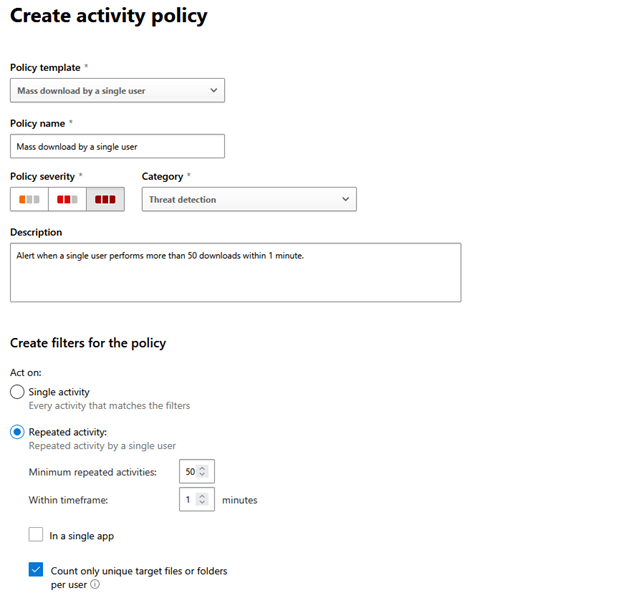
Figure 2 – New activity policy from template
At the top it shows the template used to create this policy, and below that you’ll see “Policy name”. You can name the policy whatever works for your organization, and the description should be used to ensure everyone knows your intention with this policy. In addition to including a good description of the intended purpose for this policy, I recommend adding information about who created this policy and when it was created.
The policy severity and category boxes don’t have a technical impact at this point but can be important to the function of DCA with other tools. More on that later, but for now select options that make sense for your organization.
The “Create filters for the policy” section is where we start our configuration. For this policy we want to keep the “Repeated activity” radio button, but your organization may want to change the thresholds. I have the “Minimum repeated activities:” and “Within timeframe:” set to 10 in 1 minutes in my tenant, but that is mostly for testing purposes. The two check boxes below that are self-explanatory.
The next section of the template is the activity filter:
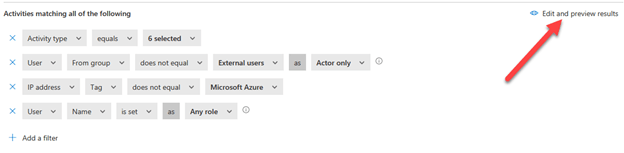
Figure 3 – Policy filters
The filters in this template are pre-built for you as shown above, and most often a good starting point:
The arrow in figure 3 points to the “Edit and preview results” wizard. Clicking there will open a new window that shows you which logged actions would be included in this filter as shown below:
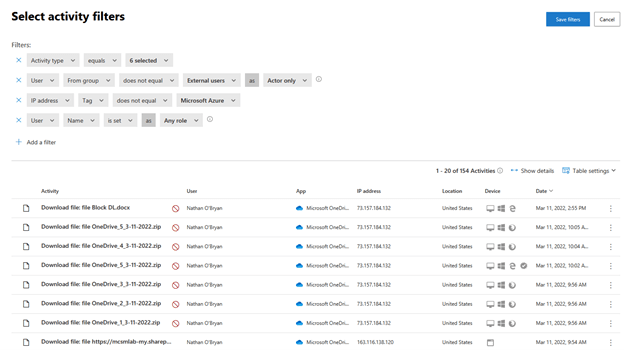
Figure 4 – Filter results
The filter shows which activities this policy would affect. The red circle with the line through shows if that activity was successful.
The next section is for alerts:
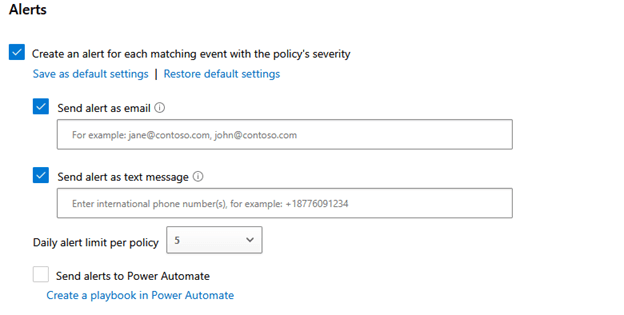
Figure 5 – Alerts
The alerting has 3 options: email, text message, and Power Automate. In my testing I have found that none of these options are anything close to “real time.” These alerts can take from minutes to hours to show up, so don’t rely on DCA for real-time alerting. I have not yet tried to do anything with the alerts to Power Automate, but I suspect there are cool uses for that feature.
The final section of the policy is for Governance actions:

Figure 6 – Governance actions
This section of the policy can allow you to take real actions beyond just monitoring activity. You can use this policy to prevent users from mass downloading files depending on what you configure here. The “All apps” section applies to all apps that DCA knows about, and the Office 365 section applies to only Office 365 apps:
The three check boxes under “Office 365” take the same actions as the same buttons in the “All apps” section, but they only apply to Office 365 applications.
As I have configured this policy, all it does is provide a notification of mass file downloads by a single user. In my testing, those notifications can take several hours to show up.
My recommendation for an administrator whose organization is interested in implementing download controls within an M 365 tenant would be to start here. Setup a policy like this to see how mass downloads are occurring in your tenant, then decide about how to limit those downloads.
Once you have setup a notify policy like this and let it run for a while, you’ll have a good idea of how often users are downloading large numbers of files and your management can make some decisions about how much of a risk this is, and how your organization wants to limit those mass downloads.
In future blog posts, I’ll dive into preventing users from downloading large numbers of files at once.
On-premises components, such as AD FS, PTA, and Exchange Hybrid are critical for Office 365 end user experience. In addition, something as trivial as expiring Exchange or AD FS certificates can certainly lead to unexpected outages. By proactively monitoring hybrid components, ENow gives you early warnings where hybrid components are reaching a critical state, or even for an upcoming expiring certificate. Knowing immediately when a problem happens, where the fault lies, and why the issue has occurred, ensures that any outages are detected and solved as quickly as possible.
Access your free 14-day trial of ENow’s Exchange Hybrid and Office 365 Monitoring and Reporting today!

Nathan is a five time former Microsoft MVP and he specializes in Exchange, Microsoft 365, Active Directory, and cloud identity and security.

If you've ever participated in an Exchange Online migration at almost any level, it's likely you've...


I expect we all know there are limits to what you can and cannot do with your Exchange Online...