The New OneDrive Admin Center
I once read an interview with a NASCAR driver who said, "When there is a wreck on the track ahead...


Times have changed, specifically for the worse when it comes to how easy it is to attack your data in the cloud. That is not necessarily due to the advent of cloud technologies themselves, but rather because automation is free and cheap. Think PowerShell, Python, etc., and that cloud represents a much larger attack surface than a traditional data center approach. It's time to reconsider backup in light of ransomware.
Get off my lawn, kids!
When I was much younger, we, as an industry, built datacenters with limited ways of accessing our servers and services. We lived safely, knowing that if something significant was under attack, we could stride purposefully through our access-controlled doors, reach into our airconditioned racks, and pull out the power or network or both. That’s much more difficult to do to a cloud service if it’s under attack since it is also not hosted in your own data center.
Whose fault is it anyway
Responsibility and cloud may be a tricky concept; after all, I may have uploaded my data to Office 365 or another cloud, and I expect that the safety of the data is Microsoft’s. Microsoft’s view is that the responsibility for Data, Endpoints, Account, and Access management is always yours. See Figure 1 below for a graphical view of the responsibilities always retained by customers.
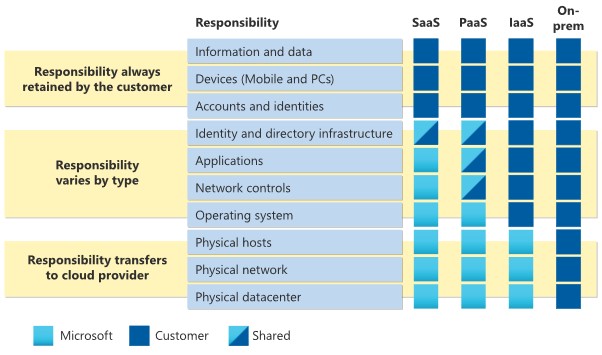 Figure 1 - Allocation of responsibility
Figure 1 - Allocation of responsibility
Microsoft acknowledges and provides guidance for ransomware defense and guidelines on how to recover. It may shock you that part of the recovery guidance is: Step1 – Verify your backups, since Microsoft also publicly writes that OneDrive is a backup for your files. That sounds like a contradiction since it may imply that you may need to backup. However, we also read that OneDrive is supposed to be a backup. OneDrive could be a backup, but only if it fits your definition of being a backup. That sounds like I’m waffling, so lets take a step back and define what a backup is.
I like to ask my customers to give me their definitions and requirements for backup. Why do I ask my customers? Backup may be part of Disaster Recovery Planning – a business function.
Often this definition reads something like: “A backup is a copy of my data, stored separately from its source and in another location, which I can restore to the original location in case of data loss or a total disaster. My backups should be able to restore from a nominated point in time or other specific criteria. I should be able to restore any of the data based on time boundaries, including the last seven days, weekly, monthly, and yearly backups. I may want to restore either a specific item, a container (mailbox, OneDrive, SharePoint, etc) or a configuration item such as permissions.”
OneDrive offers the ability to restore a file to a previous version, undelete a file or folder from the recycle bin, etc. It does not fit the rest of the classical definition of a backup, and neither does the built-in capability of Exchange, SharePoint, or other Office 365 Services. If you’re a tiny organization and Office 365 versioning and recovery capabilities fit your definition of backup, then stop reading. You are done, and you get to have a few minutes back from your day.
Ransom and backup
A backup is only a backup if you can restore it. Let us assume a scenario where attackers have compromised your Office 365 tenant and are holding you to ransom. Since the activity is criminal and you are being extorted for money, one of the attack vectors may be that they have changed your versioning to 1, waited 14 days, and then encrypted your files. That may sound far-fetched, but it is not. We may also want to assume that your tenant is compromised by a responsible adult with your best interests at heart, as opposed to teenagers targeting organizations for data exfiltration and destruction.
A backup is only a backup if you can restore it. That includes being able to log into your backup platform. Consider that during a tenant compromise, your tenant's Azure Active Directory no longer belongs to you. Consider that you may no longer be able to log into your backup platform if you have chosen to use Azure Active Directory integrated identities as the only way to authenticate. If your backup platform is inaccessible or, even worse, if it’s encrypted or data has been exfiltrated, then it no longer fits the definition of a backup.
The friction for malicious actors is low. Malware may be purchased for little money, or malware may be developed by nation states with large budgets. Malware, of course, is not the only threat in our malicious actor's ransomware arsenal, and backup shouldn’t be your only defense. Backup may be your last line of defense, though, and if it is, then we should know what a backup should look like. Here are the minimum factors I look for in a backup solution:

Nicolas is the founder, as well an architect, author and speaker focused on Office 365 and Azure at NBConsult. Nicolas is a Microsoft Certified Master for Exchange and Office 365, Microsoft MVP (Most Valuable Professional) for Microsoft Office Apps and Services since March 2007. Nicolas has co-authored “Microsoft Exchange Server 2013: Design, Deploy and Deliver an Enterprise Messaging Solution”, published by Sybex.


I once read an interview with a NASCAR driver who said, "When there is a wreck on the track ahead...


One common request when performing an eDiscovery or using the Search-Mailbox cmdlet has long been...