By now you must have heard that Microsoft is moving away from Basic Authentication and that all client authentications will move to Modern Authentication, and I've blogged about this previously.
Another thing that is happening is Microsoft moving away from TLS 1.0 and 1.1 and only allowing TLS 1.2 connections. This can have an impact on your organization too, so let’s have a look what is going to happen and why.
SSL and TLS
SSL and TLS are acronyms that are used interchangeably. SSL stands for Secure Sockets Layer and TLS stands for Transport Layer Security. Most people think about Internet, browsers and security when talking about SSL and Email when talking about TLS. Understandable, but there is more…
SSL is originally developed in the early nineties to encrypt communication client-server traffic so that this information cannot be sniffed across the wire. The last version of SSL was SSL 3.0, published in 1996.
TLS is the successor of SSL. Version 1.0 was released in 1999, the current most used version is TLS 1.2 which was released in 2008. But developments go on, TLS 1.3 was released only three years ago in 2018.
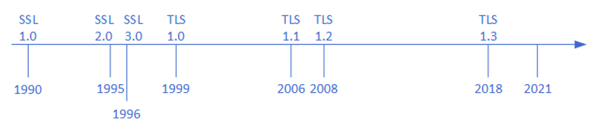
There are a lot of known vulnerabilities in SSL so this must never be used, but also TLS 1.0 and 1.1. have a lot of known vulnerabilities. The general recommendation is to not use these TLS implementations anymore but, stay on TLS 1.2 or higher.
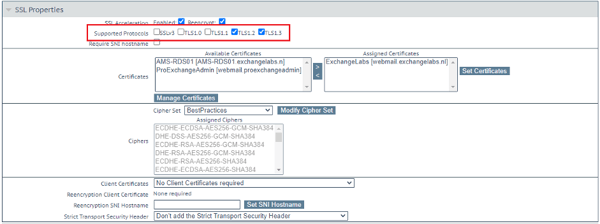
Exchange server 2019 is running TLS 1.2 only out of the box. But also when configuring a load balancer, TLS 1.0 and 1.1 are not enabled by default as shown in the following screenshot of my Kemp load balancer. It's clearly visible that only TLS 1.2 and 1.3 are enabled.
But what will you notice when Microsoft stops support for TLS 1.0 and 1.1?
If you are running recent versions of operating systems and apps, most likely you won't notice anything. But, when running Windows 7 with an older version of Internet Explorer, or Outlook 2010 you will see connection problems. I have also seen issues where PowerShell was not able to download and install modules from the Microsoft site using Install-Module command because of this. And don't forget Exchange 2010 in a hybrid environment, this will result in issues as well. Devices and browsers that are known to be unable to use TLS 1.2 (and thus stop working) are:
- Android 4.3 and older.
- Firefox 5.0 and older.
- Internet Explorer 10 and older on Windows 7.
- Internet Explorer 10 on Windows Phone 8.
- Safari 5.0.4/OSX 10.8.4 and older.
But these are all easy to solve, several blogs are available when you run into issues here.
But the most shocking I heard last week was SMTP relay in Exchange Online. Almost 25% of all SMTP traffic used for relay is not using TLS 1.2 or even worse, not using any encryption. For me this was an eye opener as well, several of my clients are relaying directly in Exchange Online, and sometimes this is a simple Windows server with some application, accessing Exchange Online directly. No question about it, when Microsoft only accepts TLS 1.2 connections this will result in a serious number of issues.
Summary
Besides decommissioning Basic Authentication in Office 365, Microsoft will also decommission older TLS versions and only support TLS 1.2 or higher. This will result in older devices, operating systems, browsers and applications ceasing to work. And don't forget SMTP relay from on-premises to Exchange Online, serious issues arise here when Microsoft stops support for older versions of TLS. Act now, start an inventory of your own environment and make sure you are prepared well.
ENow’s solution is like your own personal outage detector that pertains solely to your environment. ENow’s solution monitors all crucial components including your hybrid servers, the network, and Office 365 from a single pane of glass. Knowing immediately when a problem happens, where the fault lies, and why the issue has occurred, ensures that any outages are detected and solved as quickly as possible.