Deploying Windows Hello for Office 365
Having grown up with personal computers in the 70s and 80s my introduction to computer science was a simple two-line program.
20 END
ENow Software's Microsoft Exchange Online blog built by Microsoft MVPs for IT/Sys Admins.
Posts about:


Having grown up with personal computers in the 70s and 80s my introduction to computer science was a simple two-line program.

Over the last several years Microsoft has made tremendous headway in showcasing the value proposition of the Office 365 platform and suite of collaboration tools. In fact, the argument can be made that the Office 365 suite of tools has helped fuel the team-based way of working.
The security perimeter has changed dramatically over the last 5 years. The landscape has gone from a tightly controlled on-premise environment to data, identities, and devices being spread across on-premise and several cloud systems. How can you protect your data and identities while using a spectrum of on-premise and cloud applications and devices? How do you monitor and identify threats? How can you quickly identify the pre and post-breach of systems across on-premise and the cloud?

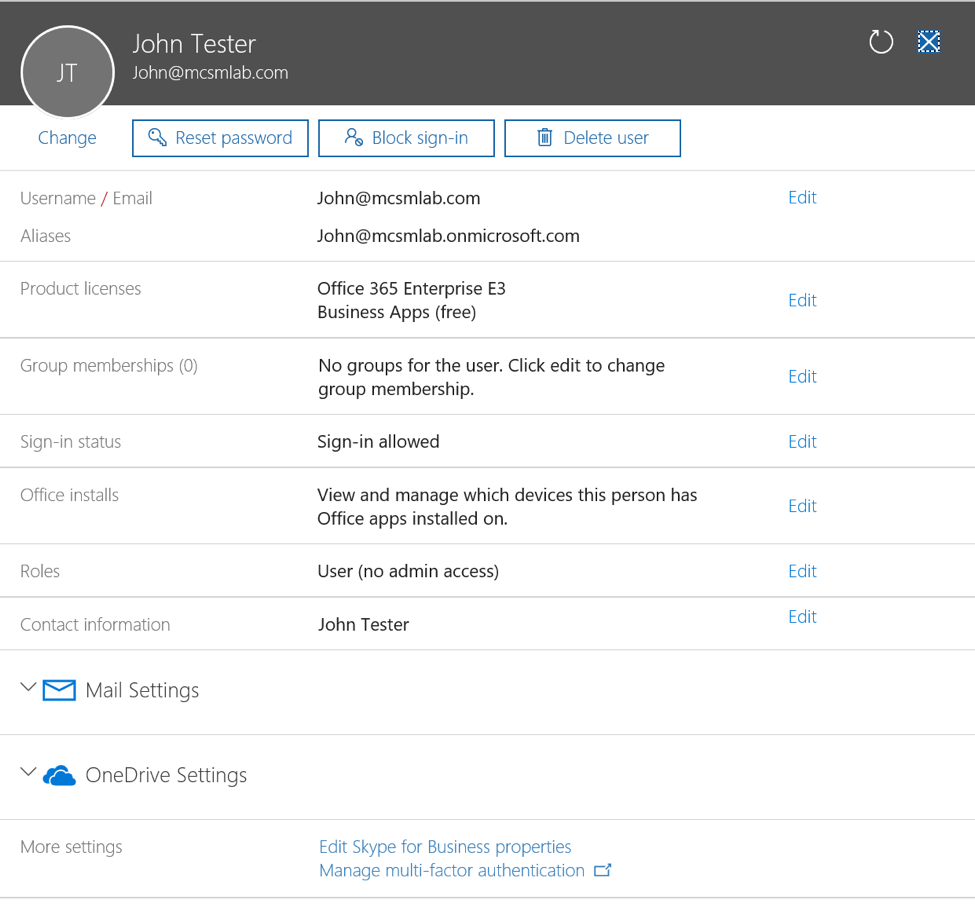
One of the best things about Office 365 is that we can always count on new features and functionality to be available. Microsoft is constantly working to improve the services already live in Office 365, as well as working to create new services. Some of the new services added do have an additional licensing fee attached, but Microsoft also adds a considerable number of features to the license SKUs already in-place.


"Will my job as an IT professional still be needed if my employer moves the IT infrastructure to the cloud?"


A few weeks back, Microsoft announced the Public Preview of a new and very interesting feature, named Attack Simulator. The idea behind Attack Simulator is to give you a safe toolset to use in order to probe some aspects of the security of your organization when it comes to email hygiene and password strength, with more to come in the future. In this article, we will do a quick overview of Attack Simulator.


The use of Office 365 services depends on proper DNS name resolution, especially when running a hybrid configuration. Without a non-functional DNS name resolution, the end user will not be able to connect to Office 365 service from within the company network or from the Internet.
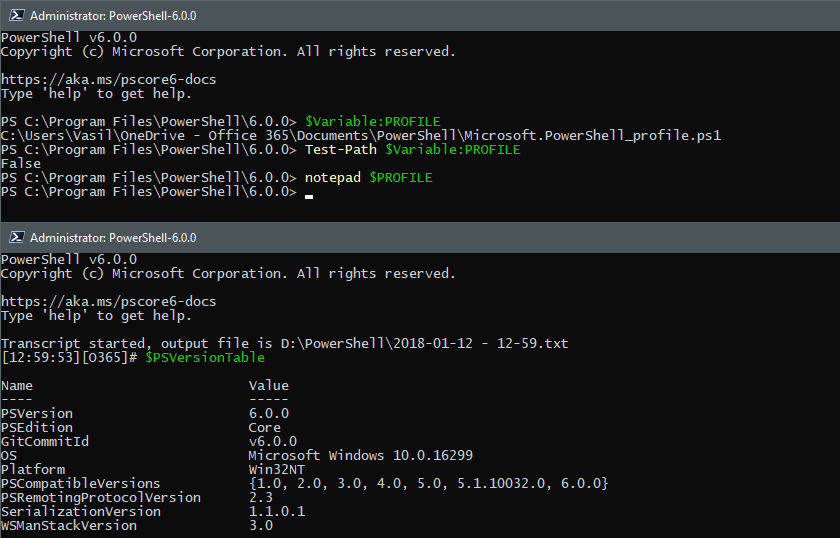

In case you have missed the news, last week a new flavor of PowerShell, namely PowerShell Core was officially released. In this article, we will take a closer look at PowerShell Core in the context of Office 365.
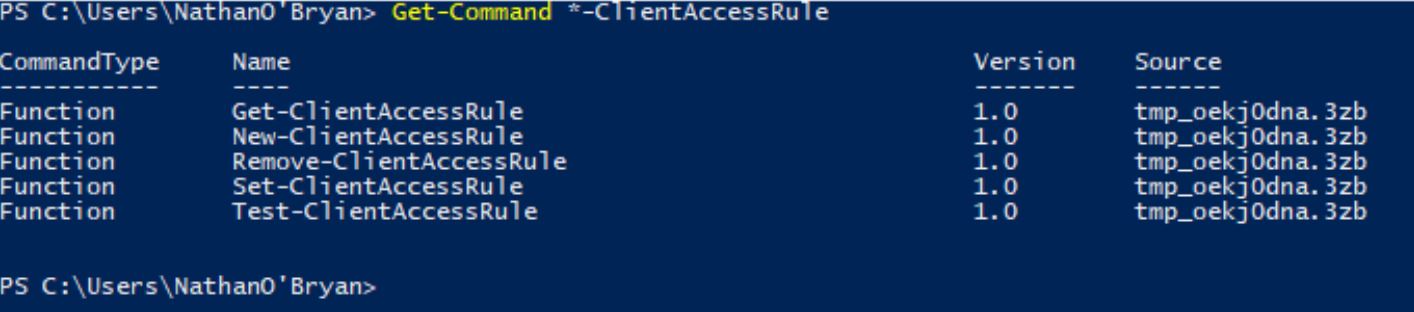

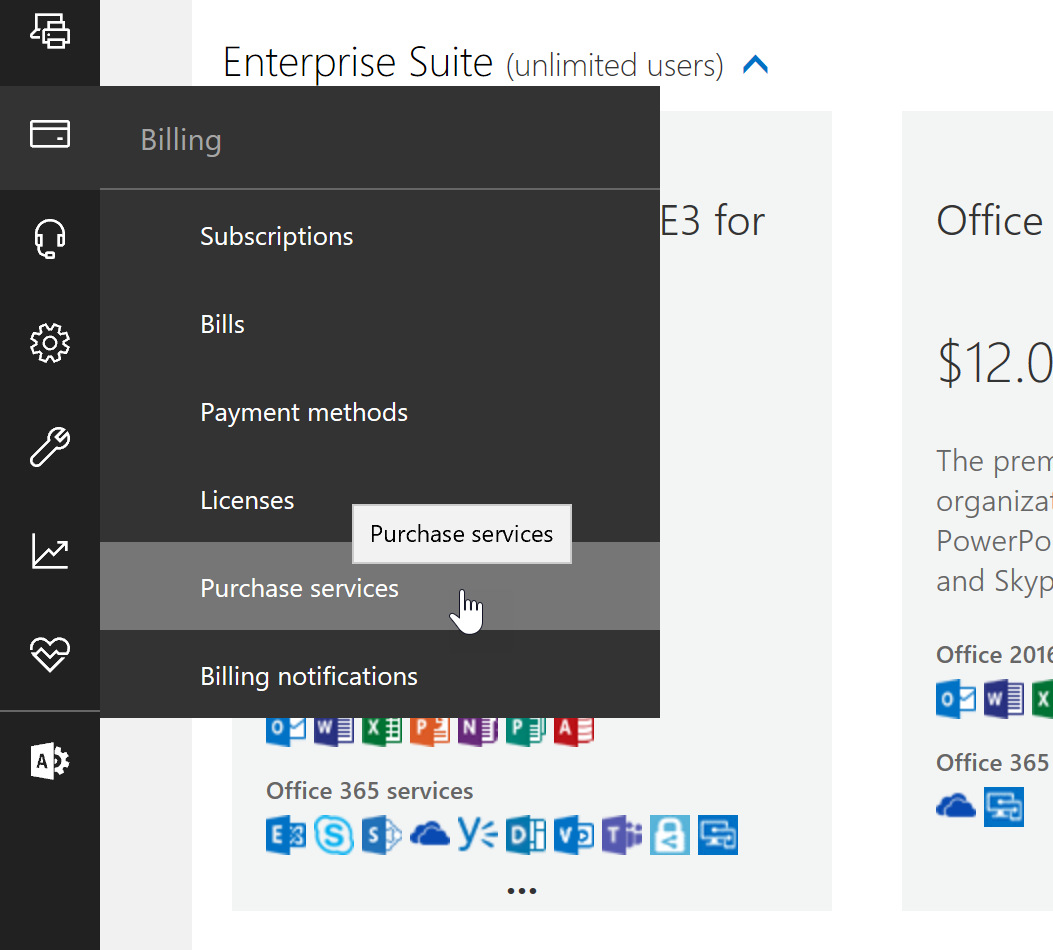
There are many ways you can manage and control the way your end-users connect to Office 365. Intune, and Azure Active Directory Premium are add-on feature sets for your Office 365 subscription that give you advanced controls for managing client access scenarios, but some customers want a lower level of control that they can implement without having to buy add-on licenses.


I have long been interested in encryption. I started off my IT career in the United States Marine Corps where I had a Top-Secret security clearance and frequently worked with classified message traffic. During this time, I learned a lot about the rules of encryption and security. Most of what I learned, however, is that encryption is incredibly hard to do correctly.