Mobile Device Management (MDM) In Office 365
The growth of mobile devices, such as smartphones and tablets, changed the world rapidly. Today,...


Acompli was acquired by Microsoft in December 2014. In January 2015, Acompli was re-branded as Outlook mobile – sharing its name with the Microsoft Outlook desktop email client. Within the last year, Outlook mobile has received so many features and is now focused on business and enterprise customers for connecting their email accounts with Outlook mobile.
Note: Outlook mobile is available for iOS and Android devices and free for consumer usage. However, commercial users require an Office 365 subscription that includes the Office Applications: either Business, Business Premium, Enterprise E3, E5, ProPlus, or the corresponding versions of those plans for Government or Education. If you only have an Exchange Online license (without Office) or an Exchange on-premises (Exchange Server) license, you are not licensed to use the app.
Today more and more people are working on their phones, with Outlook mobile being used by more than 100 million users on iOS and Android devices. 93% of mobile workers use a smartphone daily, working on the phone 33% of their work day. This means you have to protect your corporate data and things must be as easy to use on your smartphone as they are on your desktop. This is where Enterprise Mobility + Security comes in the play.
It is important to understand that everything behind the scenes runs in the Azure cloud environment and no credentials were cached. Furthermore, Outlook mobile uses Modern Authentication (OAuth) and no credentials are stored. At sign in, the user authenticates directly with Office 365 and receives an access token to return. The token grants Outlook mobile access to the appropriate mailbox.
Since December 2018, Microsoft started to migrate customers to a native Microsoft sync technology that removes the States Protocol Translator component from the Office 365-based architecture. With the native Microsoft sync technology, Outlook mobile connects directly to Office 365 for data connections ensuring the data is protected by an HTTP TLS-secured connection end-to-end. The native Microsoft sync technology will enable Outlook for iOS and Android to take advantage of native Office 365 features it does not support today, such as S/MIME, Microsoft Information Protection labeling, and shared mailboxes. These and more Office 365 features will roll out soon after the architecture update.
As an Exchange administrator, you can check which data sync protocol Outlook mobile clients are utilizing in the Office 365-based architecture:
Get-MobileDevice | where {$_.DeviceModel -eq "Outlook for iOS and Android"} | Format-List FriendlyName,DeviceID,DeviceOS,ClientType
The ClientType property indicates which data sync protocol is in use. If the value is REST, then the client is utilizing the REST API. If the value is Outlook, then the client is using the native Microsoft sync technology.
The old (REST API connection model):
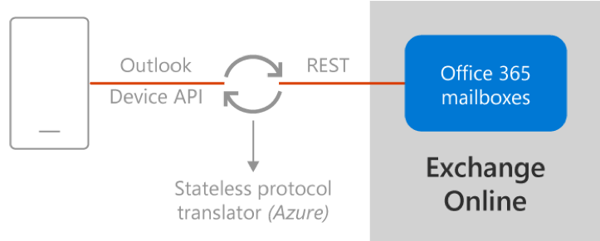
The new (native Microsoft sync model):

Conditional Access: CA is nothing more than a policy driven approach that basically takes a bunch of if-then conditions whether to allow or block access and grant different controls.
If the access to the service or application is allowed, you can grant further controls like require MFA or require approved client app. But how does the require approved client app grant control works and how can we leverage that to enforce Outlook mobile as the only mobile messaging client?
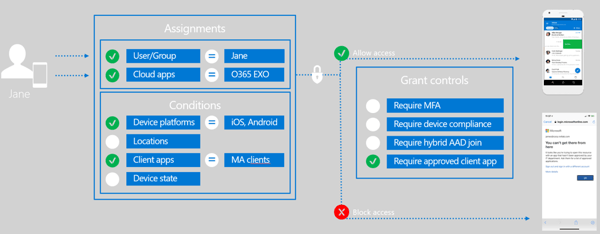
We will have a set of assignments, like in this case we have the user Jane and we have our cloud apps defined. At a minimum to use Outlook mobile we need Exchange Online as our cloud app. But for a real-time collaboration on any device from anywhere we need more than just Exchange Online. We need support for Microsoft Teams, OneDrive for Business, SharePoint Online, Yammer, etc. This condition will only allow Outlook mobile as the modern authentication client for iOS and if Jane tries to use the native Mail app client, access will be blocked.
In a high-level overview, the require Outlook mobile conditional access flow looks as follows:
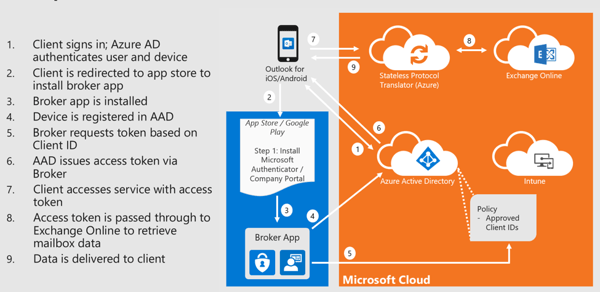
These conditional access policies can also be combined with features of Azure AD Identity Protection to generate sign-in risks and ensure that only users with specific risks (or no risks) are allowed to sign in. Depending on the risk you have defined, users might also be allowed to sign-in with a high risk but requires additional grant controls like require MFA.
For years we have had traditional device management capabilities. Device management means we can fully manage the device and push down compliance policies like the PIN requirement. We can do configuration policies where you push down certificates, VPN configuration, proxy settings, etc. You can push down apps and manage the entire device experience effectively and of course, you can do wipes which wipe the entire device and erase all the data. As we have moved into this more modern transformation of real-time collaboration, we all know mobile devices are now indispensable. Users nowadays want to have personal accounts or personal data on corporate owned devices, and vice versa. But we mostly don’t want to enroll our personal devices into IT because we all might fear that if one mistake might happen and an IT admin may accidentally wipe our device.
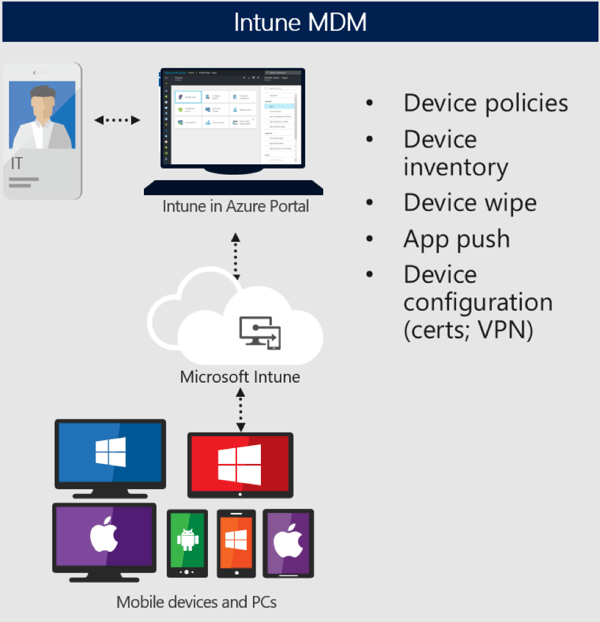
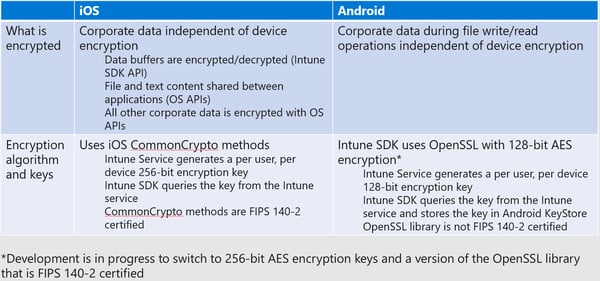
With iOS, it’s a fully managed device experience. With Android they have seen that this blending of work and personal is something of a priority. Starting with Android 5.0, they introduced Android For Work which was rebranded to Android Enterprise. Android Enterprise offers an interesting experience for this BYOD type of deployment model.
Upon enrolling the device, Android creates a work instance within that device. It’s effectively a container for which all corporate data can be placed, and all corporate apps can run out of. Thus, providing a separation between the personal existence and the work existence gives you the insurance that only corporate data can be wiped.
For more information on Intune MDM and app protection, securing data in Office 365, and the roadmap for Outlook Mobile, please see the second part of this blog topic Deploying Outlook Mobile Securely in the Enterprise Part 2.
In a cloud based world, where admins are often left in the dark, ENow turns the light back on! ENow's synthetic transactions test common Office 365 applications (OneDrive, Teams, SharePoint) allowing admins to proactively test and easily verify their end-users experience. Learn more

Dominik is a Microsoft MVP primarily specializing in Microsoft Exchange, Exchange Online and Office 365. Dominik currently works for a German consulting company, AtWork. At atwork, Dominik focuses on designing and building message infrastructures and cloud technologies. Dominik has worked in IT since 2004, primarily with Exchange Server but also has experience with Windows Server, Active Directory, Azure, Office 365, Unified Messaging and various third party products.

The growth of mobile devices, such as smartphones and tablets, changed the world rapidly. Today,...