Modern Authentication Updates in Exchange Online

Nathan O'Bryan MCSM

The great thing about Office 365 is that it is a constantly updated service. For your subscription, your organization is constantly getting new features and functionality that can greatly improve the overall Office 365 experience. Of course, the downside of that is that IT pros working in Office 365 need to keep up to date on these changes..
In this blog post, I am going to explain what Modern Authentication is, what the alternative is, why you want it, and how you can implement it in your Exchange Online deployment.
What is “Modern Authentication”?
Before we get into talking about the recent updates, we should take a minute and make sure we are all on the same page about what Modern Authentication is.
According to Microsoft:
"Modern authentication in Office 365 leverage Active Directory Authentication Library (ADAL)-based sign-in to Office client apps. Modern Authentication allows administrators to enable features such as Multi-Factor Authentication (MFA), SAML-based third-party Identity Providers with Office client applications, smart card and certificate-based authentication, and it removes the need for Outlook to use the basic authentication protocol."
To put it another way, Modern Authentication is an updated set of authentication protocols that allow more security and better end-user experience for Azure and Office 365 log-ins. Modern Authentication applies to more than just Exchange Online, but for this post I’m only focusing on ExO.
The “old way” is Basic Authentication. Basic Authentication is just sending a username and password (always encrypted) to the service. Basic Authentication does not support Multi-Factor Authentication (MFA), or SAML-based 3rd party services. Since over 99% of the user accounts that have been breached in Office 365 did not have MFA turned on, I’m to the point where I think it’s just plain irresponsible to have an Office 365 account that does not have MFA turned on.
In the old days, turning on MFA for Office 365 accounts meant having to deal with app passwords. App passwords were just another password you had to enter, which is not MFA. Basic Authentication just did not allow for a complete MFA experience, thus the need for Modern Authentication.
Do I have Modern (or Basic) Authentication in my Office 365 tenant?
The place to start on your journey to Modern Authentication is to ensure that you do, in fact, have Modern Authentication turned on for you tenant. Depending on when your Office 365 tenant was created, you may or may not have Modern Authentication turned on.
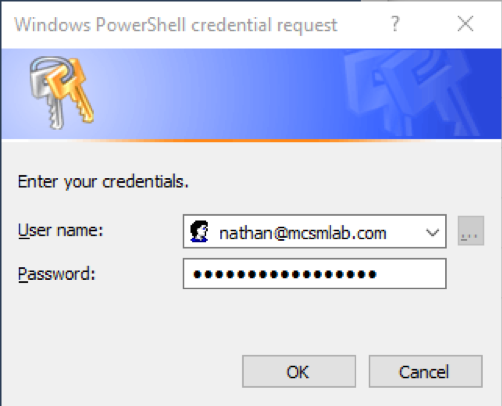
Any connection you make to Office 365 that has a log-in box as shown below is using Basic Authentication.
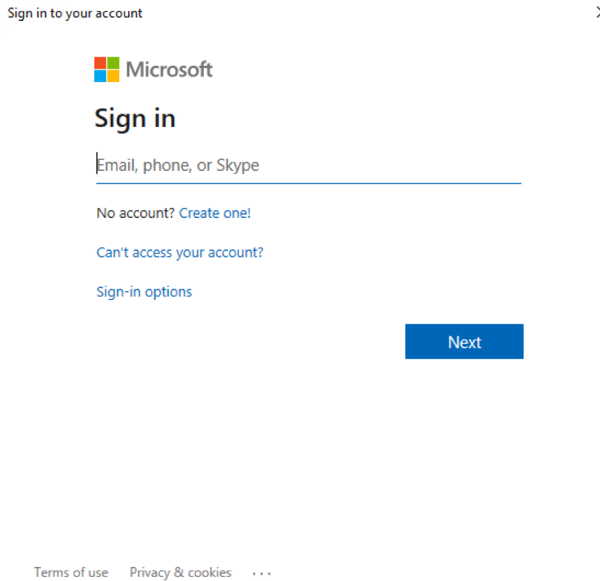
The Modern Authentication login screen looks like this.
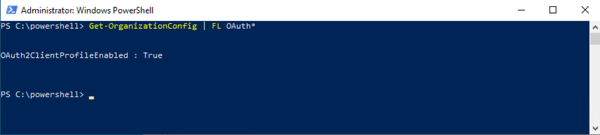
While the login screen you get can give you a good indication of if that session is using Modern or Basic Authentication, there is a better way. To verify that Modern Authentication in Exchange Online is on for your tenant, connect to PowerShell for your tenant and run the command as shown below.
Once you have verified that Modern Authentication is turned on for your Office 365 tenant, the next step is to ensure that Basic Authentication is turned off. Let’s have a look…
How do I disable Basic Authentication for Exchange Online?
There are 12 difference protocols and services within Exchange Online that can use Basic Authentication. Those protocols and services are listed in the table below.
|
Protocol or service |
Description |
|
Exchange Active Sync (EAS) |
Used by some email clients on mobile devices. |
|
Autodiscover |
Used by Outlook and EAS clients to find and connect to mailboxes in Exchange Online |
|
IMAP4 |
Used by IMAP email clients. |
|
MAPI over HTTP (MAPI/HTTP) |
Used by Outlook 2010 and later. |
|
Offline Address Book (OAB) |
A copy of address list collections that are downloaded and used by Outlook. |
|
Outlook Service |
Used by the Mail and Calendar app for Windows 10. |
|
POP3 |
Used by POP email clients. |
|
Reporting Web Services |
Used to retrieve report data in Exchange Online. |
|
Outlook Anywhere (RPC over HTTP) |
Used by Outlook 2016 and earlier. |
|
Authenticated SMTP |
Used by POP and IMAP clients to send email messages. |
|
Exchange Web Services (EWS) |
A programming interface that is used by Outlook, Outlook for Mac, and third-party apps. |
|
PowerShell |
Used to connect to Exchange Online with remote PowerShell. |
Depending on your organization’s needs, you may still need Basic Authentication for some of these protocols. Making sure Modern Authentication is turned on in your tenant is a great first step, but to ensure the best level of security for your tenant you need to make sure that Basic Authentication is disabled wherever possible.
To block Basic Authentication in Exchange Online, you will need to create an authentication policy. To do so, connect PowerShell to your Exchange Online tenant, and run the cmdlet
New-AuthenticationPolicy -Name "<Descriptive Name>"
Once you create the authentication policy, you can then disable Basic Authentication for each of the services with the Set version of this cmdlet as shown below
Set-AuthenticationPolicy – Name “<Policy Name>” -AllowBasicAuthActiveSync $False
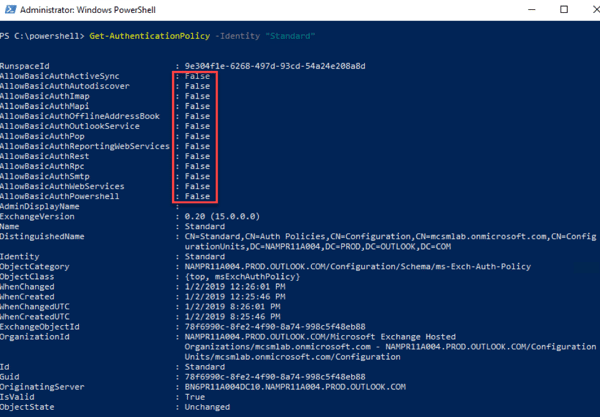
Below you can see a screenshot of the authentication policy for my Exchange Online tenant. This policy has Basic Authentication disabled for all services.
I would recommend against setting a single authentication policy for your entire tenant that will disable Basic Authentication all services. It is best to create a new authentication policy with Basic Authentication disabled, and then slowly roll that policy out across your organization. You may have service accounts that need Basic Authentication to some of these protocols to function. Once you create your locked down authentication policy, you can assign that policy to users with the following PowerShell cmdlet
Set-User -Identity <UserIdentity> -AuthenticationPolicy <PolicyIdentity>
In the below screenshot you can see my account has the authentication policy for above assigned. There might be other accounts in my tenant that have Basic Authentication allowed for various reasons.

What’s New for Modern Authentication in Office 365?
Microsoft has been working to ensure that Modern Authentication works for all the protocols in Exchange Online, but that is an ongoing process. Within the last few weeks, Microsoft has announced that Modern Authentication is working for POP, IMAP, and SMTP.
If you have had to keep Basic Authentication turned on in your tenant for a service account that needs to authenticate to one of these protocols, it’s time to update your authentication policies since Modern Authentication now works.
Monitor AD FS & MFA with ENow
Proactively monitor AD FS from the end-users perspective with ENow's industry leading monitoring platform. ENow monitors all of your AD FS servers and performs synthetic transactions, including performing a Single-Sign-On against Office 365 from inside your organization and outside (remote tests).

Nathan O'Bryan MCSM
Nathan is a five time former Microsoft MVP and he specializes in Exchange, Microsoft 365, Active Directory, and cloud identity and security.
Related Posts

Security Features Guide for Office 365 Administrators

Nathan O'Bryan MCSM
Office 365 is Microsoft's premier cloud service, and the clear leader in the "back office" server...
