Changes in Exchange Online PowerShell
Microsoft recently released a blogpost about deprecating Remote PowerShell in Exchange Online. It’s...


October 13, 2020, is an important date for Microsoft for a variety of reasons. On this date, Microsoft will stop support for their 2010 suite of products like Exchange 2010, SharePoint 2010, Office 2010, etc. In addition, Microsoft will stop basic authentication in Office 365 as outlined in their post Upcoming changes to Exchange Web Services (EWS) API for Office 365 and their follow-up post Basic Auth and Exchange Online – February 2020 Update.
But what does that mean? If you have the latest version of Microsoft software and everything configured according to Microsoft best practices you should be good. However, most customers don’t have this and may run into issues. Luckily, these problems can be avoided. Let’s have a look.
When using Basic Authentication, the username and password are sent in clear text across the wire. The connection is secured by SSL so traffic is unreadable. Every time a resource is accessed, the username and password are sent across the wire, over and over again. Basic authentication is vulnerable to brute force or password spray attacks. When users are using weak passwords (admit it, they do) it is just a matter of time before their account is compromised.
In Office 2013, Microsoft introduced a new way of authentication called Modern Authentication, which is token-based. A client reaches a logon page (from Azure AD) and enters his/her credentials. Azure AD creates a token and the client uses this token to access other resources in the Microsoft cloud. This can include Exchange Online, SharePoint Online, OneDrive for Business, Azure resources, etc.
So how do you know if your (Outlook) client is using Basic Authentication or Modern Authentication? The authentication popup when Outlook 2016 shows when using Basic Authentication looks like this:
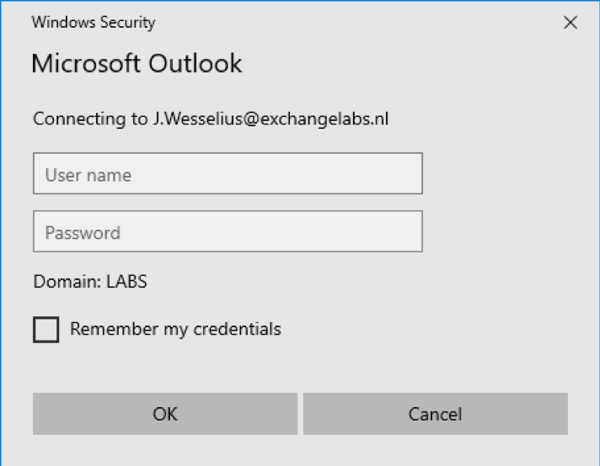
The same Outlook 2016 clients shows the following popup when using Modern Authentication:
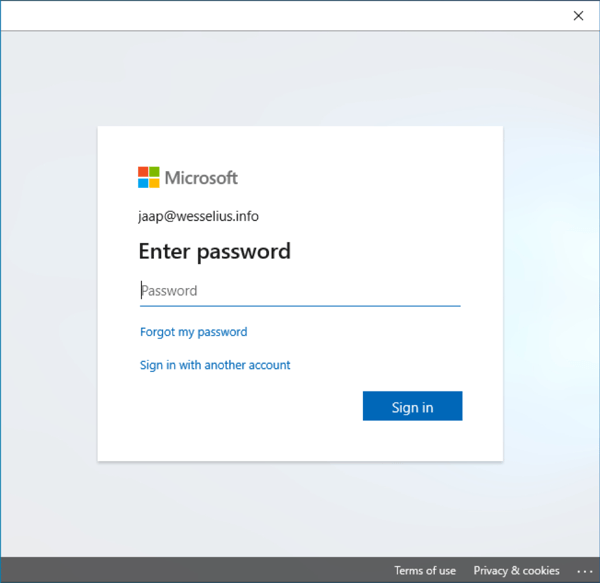
As mentioned previously, Outlook 2013 and higher support Modern Authentication. However, if you are using Outlook 2010 in combination with Exchange Online, you will run into issues since Outlook 2010 does not support Modern Authentication. And in this scenario does not support means does not connect. End of story for Outlook 2010 (I know, Outlook 2010 is an old product and out of support by then, but this is still used frequently).
But it’s not just Outlook, it’s Exchange Web Services (EWS), ActiveSync, Remote PowerShell, POP, and IMAP. ActiveSync is used by native mail clients in iOS and Android devices. For iOS, you’re good if you are using iOS 11 or higher, for Android I’m not sure since there are so many versions available. Think about applications that use EWS to access a mailbox, these might be impacted as well if the application does not support Modern Authentication.
You can monitor Basic Authentications using the sign-in option (scroll down to monitoring) in the Azure AD Portal. This returns all logins (successful and failed) of all clients in Azure AD, and for a large organization this means a lot data.
Needless to say, this is way too much information. Use the Add Filters button to narrow down the information, in this blogpost to show only information regarding Basic Authentication.
Click Add Filter, select Client App and Click Apply. Click on “Client App: None Selected” and select all options except Browser and Mobile Apps and Desktop Clients as shown in the following screenshot:
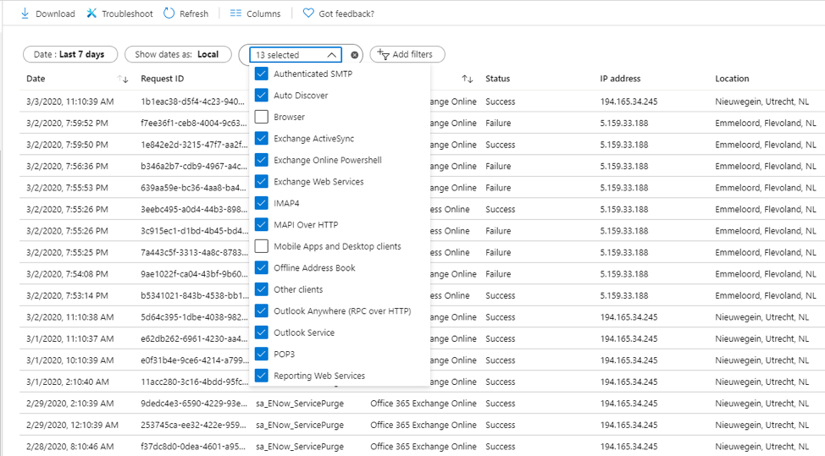
This will show all basic authentication logins in your tenant. You can click on a row to see specific details like date/time, user information, application information, and the user agent string. This reveals which client application is used. In the example below, you can see it was an Outlook 2010 Professional client that was accessing Exchange Online.
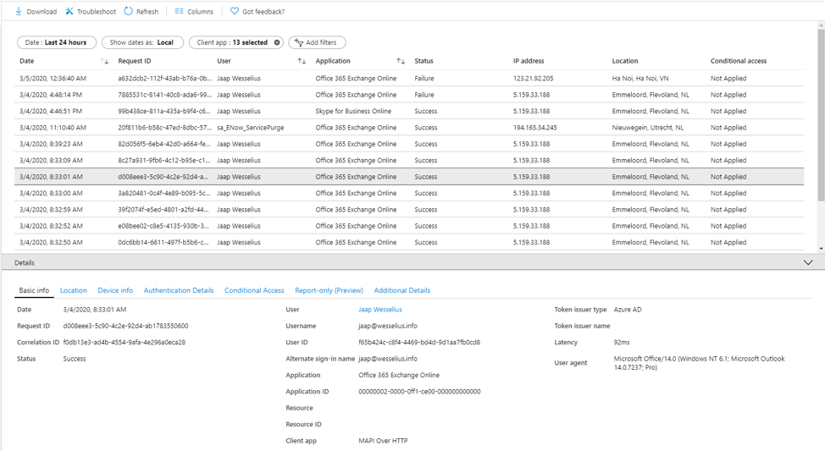
As a side note, if you add a filter on Status and select Failed, you will see all attempts using Basic Authentication that failed. This includes all password spray attacks, originating from various locations worldwide as can be seen in the following screenshot:
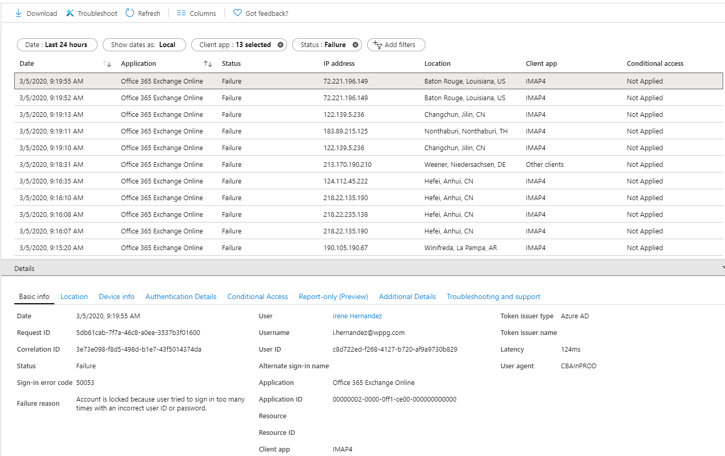
We have Office in seven different countries, and only one location is listed in the screenshot above. Most likely a user that mistyped his password.
Note. To make an analysis of the results easier you can export this information to a CSV of JSON file and import it into Microsoft Excel.
Now you are able to create a list of all clients that are using Basic Authentication to access the Microsoft cloud. The next step is to resolve the issues.
The obvious step is to upgrade any Office 2010 client that’s accessing Office 365 to Office 2013 or higher (I would recommend upgrading to Office 2016 or higher, or use Office 365 ProPlus). If you cannot upgrade the client software for whatever reason you have to off-board the mailbox (and other services when used) back to Exchange on-premises. But beware, when you have a hybrid environment where users are spread across Exchange on-premises and Exchange Online, a user that have a mailbox on-premises and using Office 2010 cannot request free/busy information of mailboxes that are in Office 365 after Basic Authentication is disabled.
Other (mobile) clients need to be upgraded as well, and so are applications that access mailboxes in Office 365 using EWS. And this can be challenging for applications and (PowerShell) scripts that are written in-house.
You can disable Basic Authentication yourself in your Office 365 tenant. It might be a bit blunt since it will impact your entire organization. The good thing is you can roll it back when too many issues occur, I’m afraid that won’t happen when Microsoft makes the switch.
A better solution is to create an authentication policy that disables Basic Authentication for users that have this policy applied. Create a new authentication policy in Exchange Online using the following command in the Exchange Online Management Shell:
[PS] C:\> New-AuthenticationPolicy -Name "Block Basic Authentication"
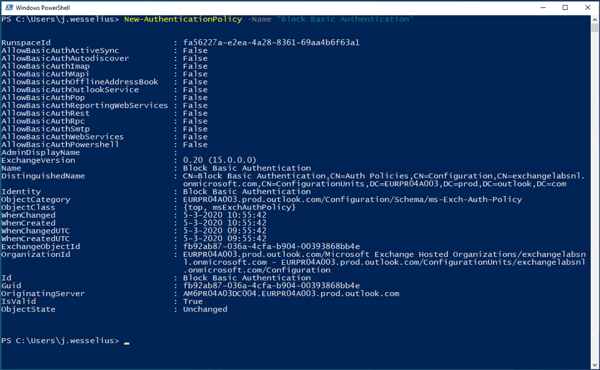
This will create a new authentication policy and all Basic Authentication options are set to FALSE by default. Of course, it is possible to enable certain settings using the Set-AuthenticationPolicy command.
To add a user to this new policy you can use the following command in the (same) Exchange Online Management Shell:
[PS] C:\> Set-User -Identity j.wesselius@exchangelabs.nl -AuthenticationPolicy "Block Basic Authentication"
The policy will be applied typically within 24 hours, but if you want to have it applied almost immediately (or realistically within 30 minutes) you can use the following additional command:
[PS] C:\> Set-User -Identity j.wesselius@exchangelabs.nl -STSRefreshTokensValidFrom $([System.DateTime]::UtcNow)
This way you can start testing the implications of disabling Basic Authentication. Best is to start this as soon as possible so that you have plenty of time to mitigate any issues as a result of disabling Basic Authentication.
In October 2020, Microsoft will stop support for their entire 2010 suite of products and at the same time disable support for Basic Authentication in the Microsoft cloud. This seems simple, but the longer you think about it, the more issues arise. Various clients will stop working and it’s up to you to figure out where this will impact your environment.
You should test all possible scenario’s with mailboxes online, mailboxes on-premises, various Outlook clients, mobile clients, cross-premises connectivity etc. Create a test matrix with all possible scenarios and start testing as soon as possible. Now you should have plenty of time, before you know the summer is over and you’re running out of time, with unpredictable results.
On-premises components, such as AD FS, PTA, and Exchange Hybrid are critical for Office 365 end user experience. In addition, something as trivial as expiring Exchange or AD FS certificates can certainly lead to unexpected outages. By proactively monitoring hybrid components, ENow gives you early warnings where hybrid components are reaching a critical state, or even for an upcoming expiring certificate. Knowing immediately when a problem happens, where the fault lies, and why the issue has occurred, ensures that any outages are detected and solved as quickly as possible.
Access your free 14-day trial of ENow’s Exchange Hybrid and Office 365 Monitoring and Reporting today!

Jaap is a Microsoft MVP for Office Apps and Services. Jaap is an independent consultant, primarily focusing on Exchange server, Skype for Business and Office 365.


Microsoft recently released a blogpost about deprecating Remote PowerShell in Exchange Online. It’s...


Last week Microsoft announced that, effective October 1, 2022, they will beginto permanently...