The security perimeter has changed dramatically over the last 5 years. The landscape has gone from a tightly controlled on-premise environment to data, identities, and devices being spread across on-premise and several cloud systems. How can you protect your data and identities while using a spectrum of on-premise and cloud applications and devices? How do you monitor and identify threats? How can you quickly identify the pre and post-breach of systems across on-premise and the cloud?
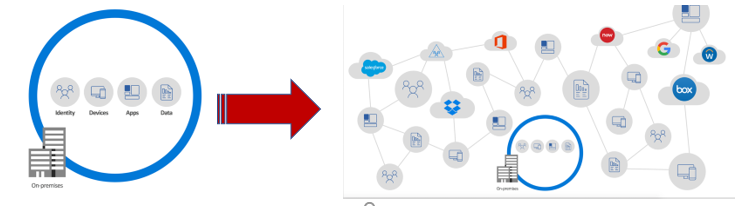
The good news is there is a suite of tools exist that can help you across this chaotic landscape. This suite of tools includes Azure Active Directory Premium as your central identity management for over two thousand across multiple cloud platforms from Google, Salesforce, Box, Microsoft, and many more. This suite helps protect the front door across divergent platforms by using tools such as Multifactor Authentication, Conditional Access Controls, and Privileged Identity Management. This suite of tools can help protect your data anywhere using Azure Information Protection to encrypt and label data in the cloud and on-premises. This suite can be used to harden devices and applications using InTune. This suite can help detect and remediate attacks using Advance Threat Analytics and Cloud App Security, shortening the amount of time it takes to identify a security event and act. This suite of tools is Microsoft Enterprise Mobility + Security.
Microsoft Enterprise Mobility + Security Breakdown
Identity and Access Management
Simplified access management and security
Centrally manage single sign-on across devices, your datacenter, and the cloud.
Multi-Factor Authentication
Strengthen sign-in authentication with verification options, including phone calls, text messages, or mobile app notifications, and use security monitoring to identify inconsistencies.
Conditional Access
Define policies that provide contextual controls at the user, location, device, and app levels to allow, block, or challenge user access.
Risk-Based Conditional Access
Protect apps and critical data in real time using machine learning and the Microsoft Intelligent Security Graph to block access when risk is detected.
Advanced Security Reporting
Monitor suspicious activity with reporting, auditing, and alerts, and mitigate potential security issues using focused recommendations.
Privileged Identity Management
Provide timely, on-demand administrative access to online services with access-related reporting and alerts.
Windows Server Client Access License (CAL)*
Provide each user access to server functions from multiple devices for a single fee.
Managed Mobile Productivity
Mobile Device Management
Enroll corporate and personal devices to provision settings, enforce compliance, and protect your corporate data.
Mobile Application Management
Publish, configure, and update mobile apps on enrolled and unenrolled devices, and secure or remove app-associated corporate data.
Advanced Microsoft Office 365 data protection
Extend management and security capabilities across users, devices, apps, and data, while preserving a rich, productive end-user experience.
Integrated PC Management
Centralize management of PCs, laptops, and mobile devices from a single administrative console, and produce detailed hardware and software configuration reporting.
Integrated on-premises management
Extend your on-premises management to the cloud from a single console with Microsoft System Center Configuration Manager and Microsoft System Center Endpoint Protection integration for enhanced PC, Mac, Unix/Linux server, and mobile device administration.
Information Protection
Persistent Data Protection
Encrypt sensitive data and define usage rights for persistent protection regardless of where data is stored or shared.
Intelligent Data Classification and Labeling
Configure policies to automatically classify and label data based on sensitivity and then apply persistent protection.
Document Tracking and Revocation
Monitor activities on shared data and revoke access in case of unexpected events.
Encryption key management per regulatory needs
Choose default key management options or deploy and manage your own keys to comply with regulations.
Identity-Driven Security
Microsoft Advanced Threat Analytics
Detect abnormal behavior in on-premises systems and identify advanced targeted attacks and insider threats before they cause damage.
Microsoft Cloud App Security
Gain visibility, control, and protection for your cloud-based apps, while identifying threats, abnormal usage, and other cloud security issues.
Azure Advanced Threat Protection
Detect and investigate advanced attacks and suspicious behaviors on-premises and in the cloud.
