Basic Authentication and Exchange Online – September 2021 Update
Last week Microsoft announced that, effective October 1, 2022, they will beginto permanently...


Microsoft’s end goal is turning off Basic Auth for all customers.
Microsoft announced that effective October 1, 2022, they will begin disabling Basic authentication in all tenants for Outlook, EWS, RPS, POP, IMAP, and EAS protocols in Exchange Online.
TL;DR:
Microsoft is removing the ability to use Basic authentication in Exchange Online for Exchange ActiveSync (EAS), POP, IMAP, Remote PowerShell, Exchange Web Services (EWS), Offline Address Book (OAB), Outlook for Windows, and Mac.
Microsoft is also disabling SMTP AUTH in all tenants in which it is not being used. SMTP AUTH supports Modern authentication (Modern Auth).
*Microsoft is not turning off SMTP AUTH. If SMTP AUTH is enabled in the tenant, it’s because Microsoft sees usage and so won’t touch it. Due to the security risks associated with it however, I recommend admins disable it at the tenant level and re-enable it only for those user accounts that still need it. For details on how to do this, see Enable or Disable SMTP AUTH in Exchange Online.
Legacy Authentication, or Basic Authentication, is where an application (or user) sends just a username and password pair to the server or service to which it (the client) is attempting to connect. Setting up an authentication request is very simple, and if the transmission on the wire is not encrypted through TLS or similar, then it is as simple for attackers to capture user credentials (Your Pa$$word doesn't matter - Microsoft Tech Community). This increases the risk of credential re-use against other endpoints or services. Multi-factor authentication can’t be used with legacy authentication and therefore doesn’t add any protection from these attacks. Legacy Authentication is directly related to the protocol in use when connecting to the server or service as well as the older client applications used. Typically, these protocols and applications are connecting to Exchange Online in Office 365 or SharePoint Online in Office 365. Microsoft have extensive telemetry on the risks associated with Legacy Authentication:
In contrast, Modern Authentication (OAuth 2.0 token-based authorization) has many benefits and improvements that help mitigate the issues in legacy authentication. Modern Auth supports additional security checks like Multi-Factor Authentication or device authentication. So, moving away from Legacy Authentication improves the security posture of your cloud environment.
ENABLE MODERN AUTH IN YOUR MICROSOFT TENANT.
If your Office 365 tenant was created before August 2017, by default Modern authentication was disabled for Exchange Online and Skype for Business (By default, Modern authentication is enabled for SharePoint online and you do not have to configure anything in SharePoint online to enable Modern authentication). Exchange Admins need to manually enable Modern authentication in the tenant.
This is done by navigating to the Modern authentication option under services in Org settings (part of Settings) in the Microsoft Admin Center. This link should take you right there. https://admin.microsoft.com/#/Settings/Services/:/Settings/L1/ModernAuthentication. Make sure the setting “Turn on modern authentication for Outlook 2013 for Windows and later (recommended)” is checked.
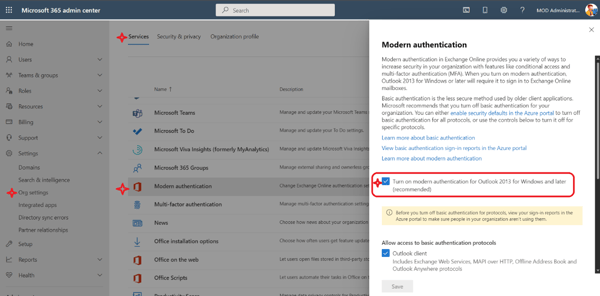
If this setting option is not available for you, chances are you have an older tenant, Modern auth is disabled by default in tenants that were created before August 2017, so you need to Enable Modern authentication using Exchange Online PowerShell, specifically, the command below:
Set-OrganizationConfig -OAuth2ClientProfileEnabled $true
There are two important things to remember about Modern authentication:
There are common client apps that connect to Exchange online and depending on the way they connect to Exchange online could still be using Basic authentication. There are mobile clients that run on Android and iOS, and then there are desktop clients that run on Windows and Mac. These clients may need to be upgraded, configured or re-coded in order to use Modern authentication. Let’s take a look at some of the common clients.
Office clients
Both Outlook for Windows and Outlook for Mac are potentially impacted by Microsoft turning off Basic Authentication in Exchange Online so any clients still using Basic Authentication need to be switched to Modern Authentication before October 2022.
You need to make sure the Outlook clients support Modern authentication and are configured to use Modern authentication, because some, although support it, have been setup and configured to use Basic authentication. The details are available in this blog post, but here’s the summary:
Be sure the tenant is enabled for Modern authentication first to ensure these clients don’t stop working when Microsoft switch off Basic Auth.
Apple Mail Client
Before Apple added support for Modern authentication to their iOS and Mac native mail clients, the connectivity to Exchange Online was made using Basic authentication. Even after Apple introduced Modern authentication, if you upgraded to a newer device, you might still be using Basic auth. This is because when you restore a backup from an old device to a new device or use the built-in migration process to move your data and settings to a new device, your Mail settings will still be configured to use Basic auth.
The way to make sure the Apple Clients are using Modern auth is to delete the mail profile and create a new one on the device. The other option is to use the Microsoft Outlook Mobile client which uses a Microsoft Sync protocol which supports Modern auth.
In an iOS 15.6 update and macOS Monterey 12.0 or greater, Apple have added support for a Modern authentication flow called Resource Owner Password Credentials (ROPC). This allows an application to sign in the user by directly handling their password. After a device is updated, the Mail app will use the credentials it already has stored in a new flow to authenticate, receive OAuth access and refresh tokens in return, remove the stored Basic auth credentials from the device, and then reconfigure the settings on the account to use OAuth (Modern auth). From then on, the account uses Modern auth to authenticate to Exchange Online, and the user doesn’t even have to know this happened.*
*Conditional Access policies that require user interaction, such as MFA verification, will not be silent because it will not be able to automatically and silently migrate to Modern auth. But assuming they can complete this process, the account will switch to using Modern auth. The Apple mail client needs to also be granted consent to access resources on behalf of the users. See how to grant consent as an admin.
Other mobile clients
ActiveSync on Mobile phones supports Modern Auth on most modern mobile devices, there may be a handful of users using legacy auth and they simply need to recreate their mail profile or update their device. Again another option is to force the user to use Outlook for iOS and Android (office.com) which uses a different sync method, other than ActiveSync.
Microsoft Teams Room Devices
Modern authentication is supported on Microsoft Teams Rooms version 4.4.25.0 and later.
For Microsoft Teams Rooms to use Modern authentication with Exchange, enable the client-side setting for Modern authentication on Microsoft Teams Rooms. You can do this in the device settings or in the XML config file.
Microsoft Teams Rooms resource accounts should not be configured to use MFA, smart card authentication, or client certificate-based authentication.
Other third-party devices or apps
I’ve seen things like backup software, Mimecast sync servers and Crestron devices using Basic authentication to connect to Exchange Online and all of them by now have Modern authentication configuration options, the point is to involve the 3rd party vendor (if you haven’t already) to get the client app configured correctly before 1 October 2022. I have seen documentation for most popular applications containing instructions for making those configurations on their respective support websites.
Custom Line of Business apps
If you have custom applications that you have developed yourself, you need to update your code to use OAuth 2.0 instead of Basic Authentication or migrate to Graph API.
If the developers of a custom app are no longer available (a bit of a risk), you might consider switching to a SaaS app that supports Modern authentication.
PowerShell (Admins)
Admins who still use the old remote PowerShell connection method or the older Exchange Online Remote PowerShell Module (V1), will need to use the new EXO V2 module.
Exchange Online V2 PowerShell module (EXO V2) uses Modern authentication and works with multifactor authentication (MFA) for connecting to all Exchange-related PowerShell environments in Microsoft 365.
For those Exchange related PowerShell scripts, use the App-only authentication with certificate-based authentication. This allows admins to run scripts without creating service accounts or storing credentials locally.
In order to understand the impact to your tenant when Microsoft switch Basic Auth off for everyone, you need to know what client applications are using Basic auth. Once you have an idea of what clients you are dealing with, you can use the information above to address those particular clients now and not after the 1st of October 2022 when they stop working.
The best way to analyse usage is through the Azure AD Sign-In report. Depending on your Azure AD SKU, the Azure AD Sign-in logs either have a history of 7 days or 1 month. Ideally, you want to analyse a month’s worth of data, if possible, but you can still do some analysis on a week’s worth. One of the properties now included in the logs is the user agent (UA) string. The UA string identifies the agent or application making a request to a server. Typically, it’s used by web servers to identify what browser you are using so the content can be adapted to suite the browser. (This is how you get prompted to use Google Chrome when you browse a Google site using anything other than a Chrome browser). Anyway, the point is, we can use this information to identify the client app and device that is using Basic authentication.
The other great feature of the Azure AD Sign-in logs is the “Client App” filter feature, which now lists all the Basic or Legacy Authentication clients (protocols) under the heading “Legacy Authentication Clients” and it is the list of 13 Basic Auth protocols used to connect to Exchange Online.
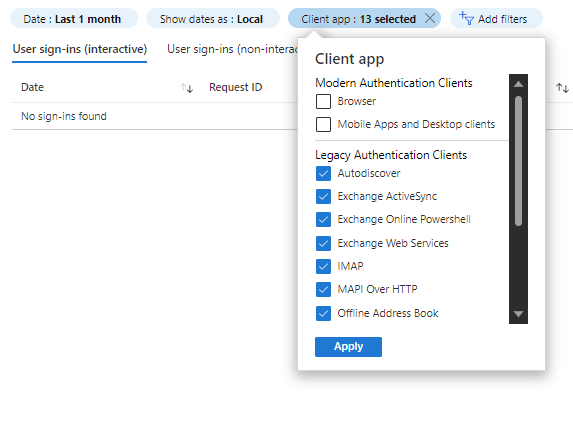
The information in the Azure AD Sign-in logs will give you user, application (cloud service), client app (protocol), device and user agent (program/hardware).
An example of some of the user agents identified in some of my recent Basic authentication hunting:
Apple-iPhone10C6/1808.107
Apple-iPhone10C6/1808.17
Apple-iPhone12C1/1808.107
LG-M700/1.81.11
Apple-iPad8C3/1703.54
Apple-iPhone11C8/1807.82
Apple-iPhone12C3/1807.82
Apple-iPad6C4/1901.404
Apple-iPad6C4/1807.82
Apple-iPhone12C1/1808.17
Apple-iPhone12C1/1807.82
Apple-iPad2C7/1307.37
Apple-iPhone11C8/1901.404
Apple-iPhone12C3/1808.17
Apple-iPhone13C3/1808.17
Mozilla/4.0 (compatible; MSIE 6.0; MS Web Services Client Protocol 4.0.30319.42000)
Crestron Fusion 9.4 (ExchangeServicesClient/15.00.0913.015)
MicrosoftTeamsRoom/4.12.126.0
ExchangeServicesClient/15.00.0913.015
MicrosoftTeamsRoom/4.11.17.0
Android-SAMSUNG-SM-G996B/101.12
Apple-iPhone13C2/1905.258
Apple-iPhone10C1/1905.258
python-requests/2.25.1
Apple-iPhone12C1/1905.258
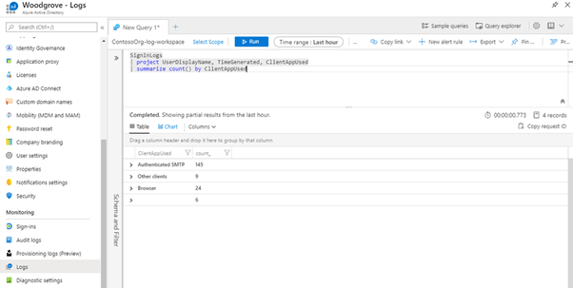
When you aggregate all the information in the sign-in logs, you have a good way of understanding the usage of Basic Authentication in your environment. If you are streaming the sign-in logs to Azure Monitor (Log Analytics) you can use the “Sign-ins using Legacy Auth” workbook and using Kusto Query Language (KQL) you can write your own powerful queries to dive deeper into the data. Below is an example query:
An even simpler way to analyze these logs is to download them to CSV or JSON file and then import them into Excel. Pro tip: only the JSON download contains the User Agent detail along with the rest of the detail. The CSV on the other hand, has location information that the JSON file doesn’t, so I tend to download both formats, import and perform a VLOOKUP to get ALL the data I need. Then you can get some pretty cool graphs going:
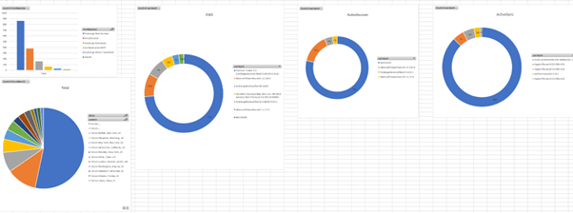
Microsoft are doing their best to inform admins of tenants of the upcoming change, as well as monthly Basic Authentication Usage reports via multiple Message Center posts.
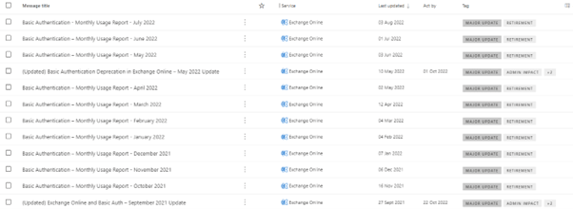
Here’s an example of the kind of information you can expect to see:
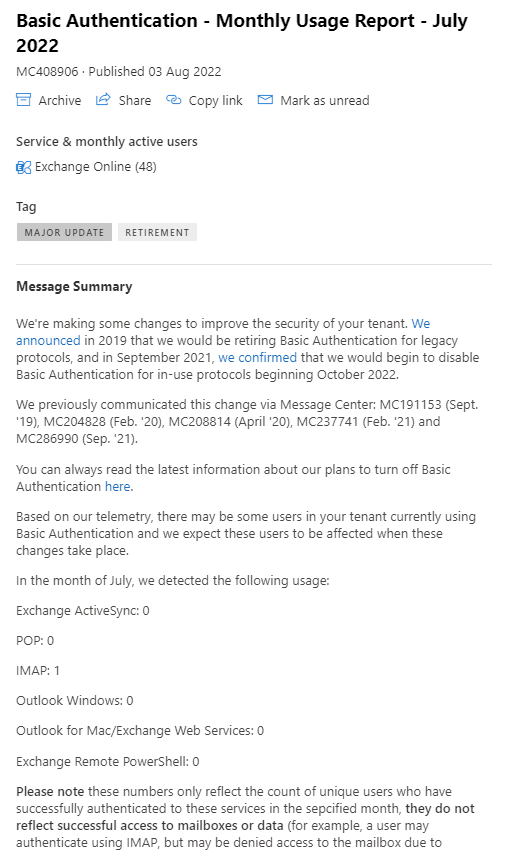
Microsoft have proactively already started disabling Basic authentication protocols in Exchange online tenants where there is no usage. Microsoft randomly select customers with no usage in any, or all affected protocols, notify them via a Message Center post informing them that in 30 days they’re going to turn off Basic Auth. 30 days later, turn it off and send another Message Center post to confirm it was done.
Microsoft are confident they are securing tenants that are not using Basic authentication presently, but they are also testing the waters with some tenants that have low usage, because they can’t tell if the usage is legitimate or an account that has been compromised. So, since early 2022, they (Microsoft) have been selectively choosing tenants and disabling Basic Auth for all affected protocols except SMTP authentication for a period of 48 hours to see if anyone notices or cares. After this time, Basic Auth for these protocols are being re-enabled, if the admin hasn’t already re-enabled using PowerShell or the “Self-service re-enablement” feature. Essentially, an intelligent diagnostic help feature in the Microsoft Admin Center. The Basic auth self-service re-enablement is activated by typing in the phrase: “Diag: Enable Basic Auth in EXO”. This will launch the diagnostic tool shown below:
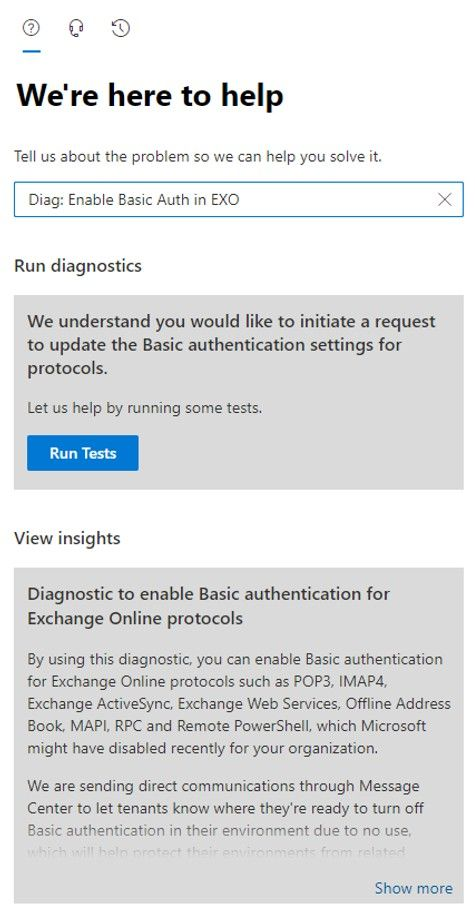
Assuming Microsoft had disabled Basic auth, you’ll get shown a list of protocols which are disabled.
This link will take you to the diagnostic tool for Basic auth directly. https://aka.ms/PillarEXOBasicAuth
For the Exchange Admins that want to check without running the self-service diagnostic tool, simply run the EXO PowerShell cmdlet Get-OrganizationConfig | Select BasicAuthBlockedApps
This will return a bitmask value, where anything other than 0 or Null means one or all of the protocols have been disabled by Microsoft. You cannot edit the value, but these are what the values mean, and in my case the value was set to 255 which meant all the protocols were disabled
This parameter is how the diagnostic tool knows what has been disabled. After requesting the re-enablement of the protocol (POP3 in my case) I saw the value change to 251.
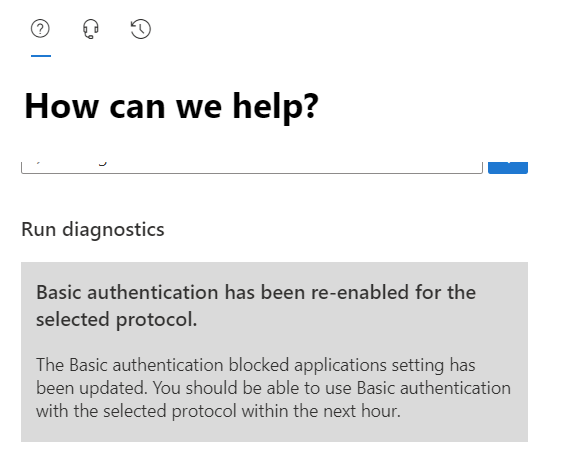
“There is no way to request an exception after October.”
Microsoft will not accept re-enablement requests after October 2022. So, I suspect the self-service re-enablement tool will disappear after October 2022.
A warning here, if you re-enable a Basic authentication protocol in the next month and a half, it will only be enabled for that time. Microsoft will turn it off regardless and you won’t be able to turn it back on. It’s insecure, so you have to deal with it NOW!
If Microsoft have not disabled Basic Auth for any protocols in your tenant, and you run the diagnostic before September 1, 2022, you can opt out of the proactive disablement. This is only a temporary opt out, however. See quote below:
“Microsoft are not providing the ability to use Basic Auth after October 2022. You should ensure your dependency on Basic Auth in Exchange Online has been removed by that time. Basic authentication (outside of SMTP) will be turned off for everyone in October 2022, including tenants who have previously opted out using our self-service tool.” (Basic Authentication and Exchange Online – September 2021 Update, n.d.)
There are a couple of ways you can block Basic/Legacy Authentication now if you wish to improve the security or simply test what will break over the next couple of weeks.
The best way is by using an Exchange Online Authentication Policy. Essentially that is what the “Modern Authentication” setting in the Microsoft Admin Center is using in the background. It’s the best because it gives you granularity to disable per protocol and it will block basic authentication pre-auth (see my blog post: Still using Legacy Authentication??? – MattChatt for details on pre-authentication). There is great documentation on how to use Exchange Authentication Policies on Authentication Policy Procedures in Exchange Online (microsoft.com).
The next is to either enable Security Defaults if you do not have Azure AD Premium or create a Conditional Access policy if you do have Azure AD Premium. Conditional Access policies Can be scoped to users, groups, apps, etc and can be run in Report-only mode. See Switch on “Security Defaults” to secure your Azure AD tenant – MattChatt and Conditional Access: Block Legacy Authentication (microsoft.com).
Now that you understand the risks associated with Basic Authentication and that Microsoft are effectively enforcing security in October 2022, here is a checklist of the things you need to do now:
On-premises components, such as AD FS, PTA, and Exchange Hybrid are critical for Office 365 end user experience. In addition, something as trivial as expiring Exchange or AD FS certificates can certainly lead to unexpected outages. By proactively monitoring hybrid components, ENow gives you early warnings where hybrid components are reaching a critical state, or even for an upcoming expiring certificate. Knowing immediately when a problem happens, where the fault lies, and why the issue has occurred, ensures that any outages are detected and solved as quickly as possible.
Access your free 14-day trial of ENow’s Exchange Hybrid and Office 365 Monitoring and Reporting today!

Microsoft Security MVP | Principal Architect @NBConsult | Speaker | Blogger. I am an Identity and Access Solutions Architect for NBConsult, a leading IT service provider in South Africa. I have 20+ years of experience in Microsoft enterprise technologies. I am passionate about Identity Governance and how it can help organizations achieve better security, compliance and productivity. I write blogs where I share my insights and tips on Application Governance.


Last week Microsoft announced that, effective October 1, 2022, they will beginto permanently...


October 13, 2020, is an important date for Microsoft for a variety of reasons. On this date,...