EMS Security Overview
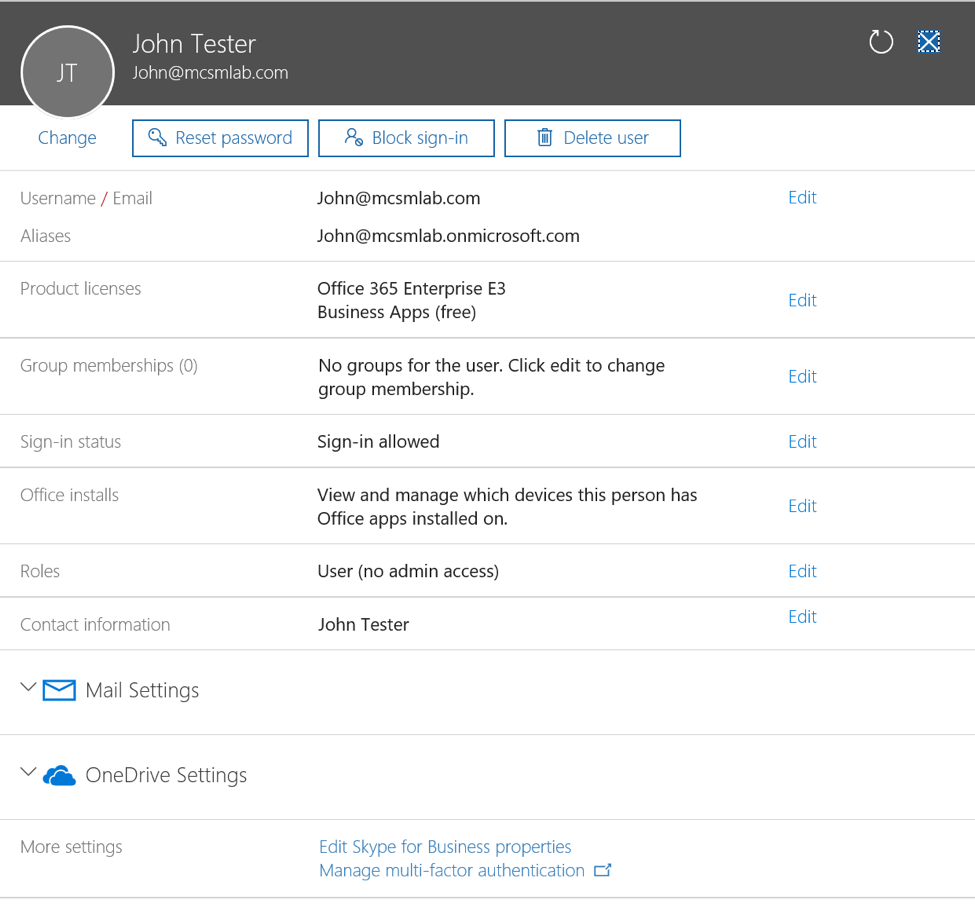
The security perimeter has changed dramatically over the last 5 years. The landscape has gone from a tightly controlled on-premise environment to data, identities, and devices being spread across on-premise and several cloud systems. How can you protect your data and identities while using a spectrum of on-premise and cloud applications and devices? How do you monitor and identify threats? How can you quickly identify the pre and post-breach of systems across on-premise and the cloud?