The Exchange Team provides you the Exchange Role Requirements Calculator now for a long time. This tool is still maintained and the preferred one for correct sizing. You can find information on how to use it on this EHLO blog post.
Although the calculator takes several scenarios into account, it cannot cover everything. One of these is LDAP Policies, which have existed since Windows 2000. These policies are your friends as they help to safeguard your Active Directory Domain Controllers. When Exchange 2010 throttling policies were introduced, they had the same purpose: manage the performance and heath of your Exchange servers. If you are not familiar with this, I recommend reading this (old) Docs article as the new one doesn’t contain sufficient details.
Why should I care?
There is a recommendation about the ratio of CPU cores of Active Directory global catalog cores for every mailbox server core of 1:8, but nothing related to LDAP client connections.
When you look at LDAP policies, you will see there is a property MaxConnections with a value of 5000. This limit is for per Domain Controller for ALL clients. You might think this is quite a high number, but here is an example of a DAG with preferred architecture:
- 1 DAG with 4 servers
- 72 databases
- Each database has 4 copies (3 high available and 1 lagged)
- Evenly distributed across all servers
In a normal situation, where every server is in a healthy state, each server holds 18 activate and 54 passive databases.
Since Exchange 2010 every database has its own Microsoft.Exchange.Store.Worker process, which is an improvement in terms of availability and performance, but this process also establish a connection to a domain controller. And this is not the only process, which is doing this. Every Exchange related process (e.g.: MSExchangeHMWorker, MSExchangeFrontendTransport) will do and some of them even more than one like w3wp.exe. You can check easily check the number of connections your Exchange server has established to a domain controller with PowerShell:
Open an elevated PowerShell and run the following commands:
- $DCConnections=Get-NetTCPConnection -RemoteAddress 10.21.0.118
- $DCConnections | group OwningProcess | sort count | select count,@{l="Process";e={(Get-Process -Id $_.Name).ProcessName}},@{l="ProcessID";e={$_.Name}} | ft -a
- $DCConnections | group OwningProcess | measure -Sum -Property count
In this example you see that the IIS worker for Exchange Active Sync established 4 connections to one of the domain controllers.
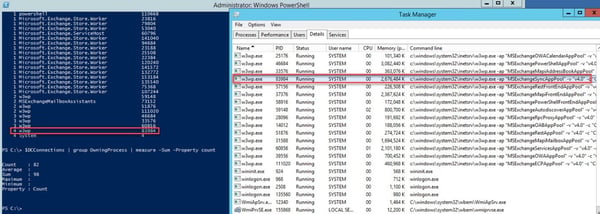
This server established in total 98 connections to one domain controller and Exchange will do the same to any other domain controller. Now you have to do the math and keep in mind that Exchange might not be the only client. Here an example:
Assuming you have 4 DC with 40 CPU cores in an AD-Site:
4*40 = 160 CPU cores (AD) è 160*8 = 1280 CPU cores (Exchange)
Furthermore, you have in this AD site 40 Exchange servers with each 24 CPU cores, which gives you a total of 960 CPU cores. From ratio perspective you are below the required ratio, but from LDAP connection perspective you have already approx. 3920 per domain controller, which is 78,4% of the allowed.
What happens when the connection limit is reached?
By design a domain controller is looking into idle connections and will drop them as needed. Idle connection doesn’t seem to sound too bad, right? From Exchange perspective it is as Exchange has a pool with active domain controllers and checks them periodically. If a domain controller is not responsive, it will be removed from the pool and re-added after successful check. It can be that after a successful check, the domain controller terminated the connection. When this happens, Exchange assumes that the server is healthy and will send requests to. These requests will fail, and as unforeseeable things can happen e.g.: unexpected prompts for credentials, database failovers, server performance decreasing. This is what I have seen in an environment running into this issue.
What is the fix?
Even though the KB article is old it’s still valid: How to view and set LDAP policy in Active Directory by using Ntdsutil.exe
The good thing about this is that you can configure the policy either per domain controller or per AD site. Thus, it gives you the ability for carefully testing, which should be always done.
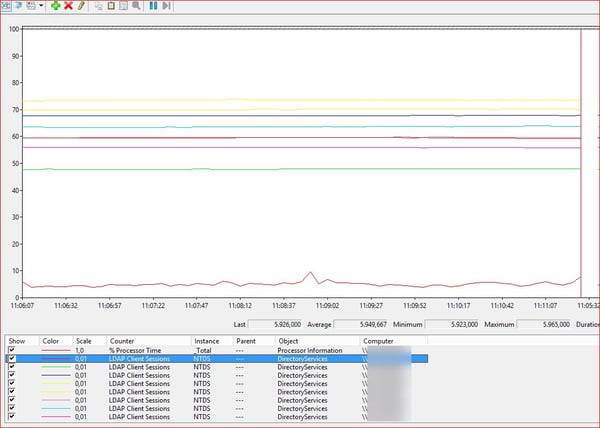
After you applied the new policy you can verify that the increase was successfully implemented:
There are several servers above the 5000 LDAP Client Sessions limit.
Conclusion
This scenario cannot be found in any environment. It also doesn’t apply only to large environment as it’s depending on many aspects like ratio, installed application and number of clients. But something you should check and monitor. The impact for the domain controller should be marginal on newer hardware. In this environment the value for MaxConnections was increased to 15.000 without any negative impact.
Monitor Exchange with ENow
Watch all aspects of your Exchange environment from a single pane of glass: client access, mailbox, and Edge servers; DAGs and databases; network, DNS, and Active Directory connectivity; Outlook, ActiveSync, and EWS client access.

