Planning, Prerequisites, and Deploying Exchange
In this article, we will share the prerequisites and guidelines you must meet to ensure a...


On September 28, Microsoft released their quarterly updates for Exchange Server:
In contrast to earlier Cumulative Updates for Exchange, these updates contain new features and changes. The most interesting features is a new service called the Exchange Emergency Mitigation Service or EEMS. When a new security issue is found, EEMS can download a mitigation almost immediately and apply the mitigation. It does this by contacting a new Microsoft endpoint (https://officeclient.microsoft.com/getexchangemitigations) once an hour. When Microsoft has stored a mitigation on this endpoint, EEMS will download and apply the mitigation on your Exchange server.
The EEMS can apply three types of mitigations:
Another (related) feature is telemetry of EEMS data. EEMS will gather information regarding its configuration on the Exchange servers and automatically upload it to Microsoft for further analysis. Don’t panic directly when you read this because you can disable this automatic uploading during installation. There is a new option when accepting the license agreement. The default is “I accept the license agreement and will share diagnostic data with Microsoft (recommended)”, but the other option is “I accept the license agreement, but I’m not ready to share diagnostic data with Microsoft”. Obviously, if you do not agree with the EEMS telemetry, you should select the second option. This is shown in the following screenshot:
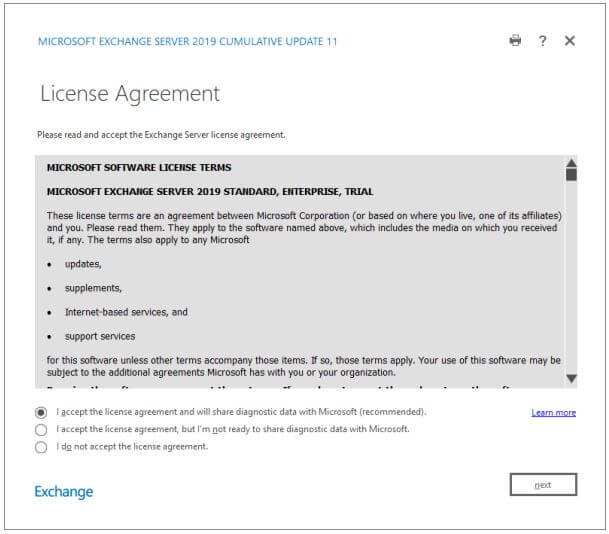
When using the unattended setup, the “/IAcceptExchangeServerLicenseAgreement” has changed to /IAcceptExchangeServerLicenseTerms_DiagnosticDataON and /IAcceptExchangeServerLicenseTerms_DiagnosticDataOFF, depending on whether you allow telemetry or not. This is shown in the following screenshot:
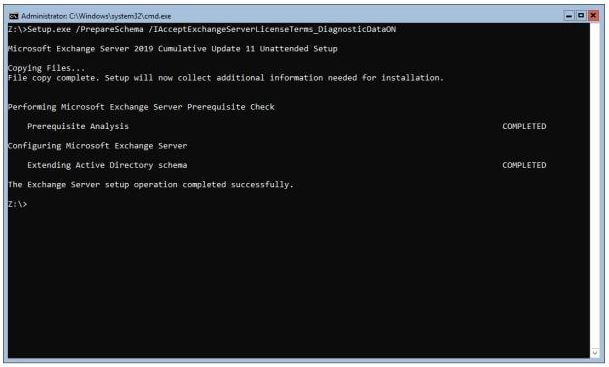
When upgrading from the previous CU of Exchange 2016 or Exchange 2019 there are not schema changes, but when moving from earlier versions there are schema changes, be aware of this. There are always changes in the configuration partition, so you need to prepare Active Directory and prepare the Domain using the /PrepareAD and /PrepareDomain switch. When using the GUI setup version, these are automatically invoked and no need to do this manually.
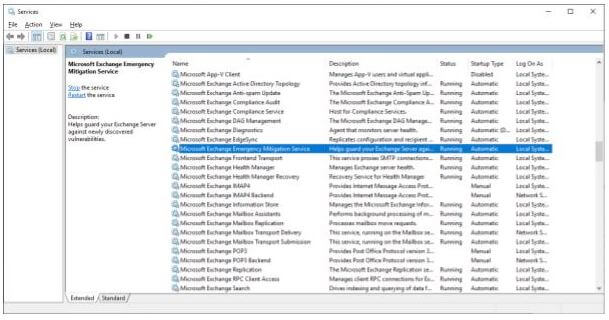
When the latest CU is installed, you will see the EEMS servers running on your Exchange server, as shown in the following screenshot:
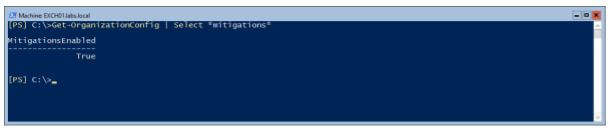
When EEMS is running, you can use the Get-OrganizationConfig | Select *mitigations* command to see if the mitigations are enabled, as shown in the following screenshot:
EEMS can be enabled on an organization level, but also on a server level. This way you can enable EEMS, but disable it on a specific server. The results are shown in the following table:
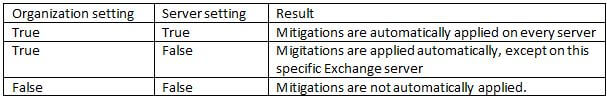
By default, there is only one mitigation configured after installation. This is the EEMS heartbeat probe. You can use the Get-Mitigations.ps1 script (in the $Exscripts directory) to get a list of all available mitigations:
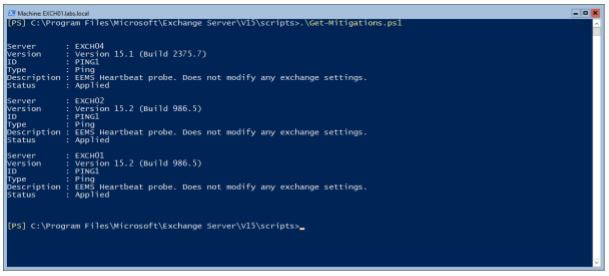
How to monitor what is happening in your Exchange servers? EEMS is logging events in the Application event log. Event ID 1005 is logged when a mitigation is applied. This happens once an hour, after checking the Officeclient endpoint. When filtering the eventlog, you can see this happening:
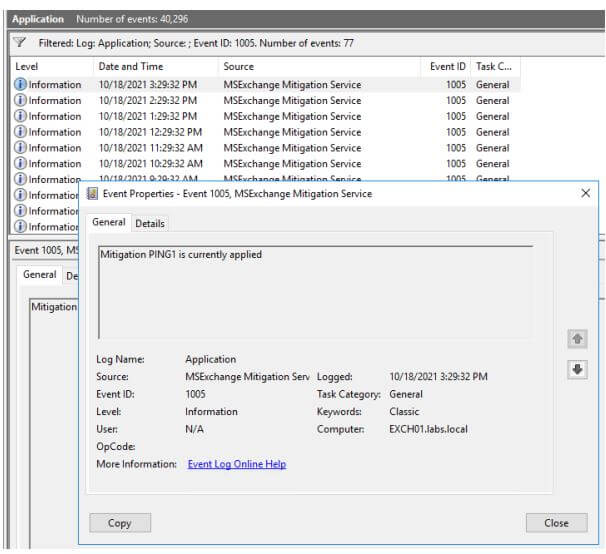
Events will also be logged when EEMS is started (EventID 1001) or stopped (EventID 1002). When an error occurs with EEMS, eventide 1008 is logged. The source of all events is MSExchange Mitigation Service.
Applying a mitigation is an administrative event, so it is also logged in Admin Audit logs. To get an overview of all mitigations that are applied, use the following command:
Search-AdminAuditLog -Cmdlets Set-ExchangeServer -Parameters MitigationsApplied
On October 12, just two weeks after the release of Exchange 2016 CU22 and Exchange 2019 CU11, Microsoft released a new set of Security Updates for Exchange Server. You should apply these Security Updates right after installing the latest CU. Please be aware that Security Updates are CU specific, and that a Security Update is also cumulative. As such, it contains all previous security updates for that specific Cumulative Update version. For more information, check Exchange Security Updates October 2021.
On-premises components, such as AD FS, PTA, and Exchange Hybrid are critical for Office 365 end user experience. In addition, something as trivial as expiring Exchange or AD FS certificates can certainly lead to unexpected outages. By proactively monitoring hybrid components, ENow gives you early warnings where hybrid components are reaching a critical state, or even for an upcoming expiring certificate. Knowing immediately when a problem happens, where the fault lies, and why the issue has occurred, ensures that any outages are detected and solved as quickly as possible.
Access your free 14-day trial of ENow’s Exchange Hybrid and Office 365 Monitoring and Reporting today!

Jaap is a Microsoft MVP for Office Apps and Services. Jaap is an independent consultant, primarily focusing on Exchange server, Skype for Business and Office 365.


In this article, we will share the prerequisites and guidelines you must meet to ensure a...


The current version of Exchange can, and in most cases should, be installed on Windows Server Core....