January 2023 Exchange Security Updates
On January 10, 2023, Microsoft released new Security Updates for Exchange 2013 CU23, Exchange 2016...


Microsoft has released Security Updates (SUs) for Exchange 2013, Exchange 2016 and Exchange 2019 that address security vulnerabilities rated ‘Critical’ (Elevation of Privileges) and ‘Important’ (Information Disclosure).
In these Security Updates, Microsoft introduced support of Extended Protection. Windows Extended Protection was already available, but it is now supported in Exchange. Extended Protection enhances authentication and prevents so called ‘man in the middle’ attacks. It is possible to enable Extended Protection manually in Exchange, but it is strongly recommended to use the Microsoft PowerShell script to enable Extended Protection.
These Security Updates are available for the latest versions of Exchange server, i.e. Exchange 2013 CU23, Exchange 2016 CU11 en 2022H1 and Exchange 2019 CU11 and 2022H1. Although supported on n-1, I strongly recommended to update your Exchange servers to the latest version, the third block in the following image:
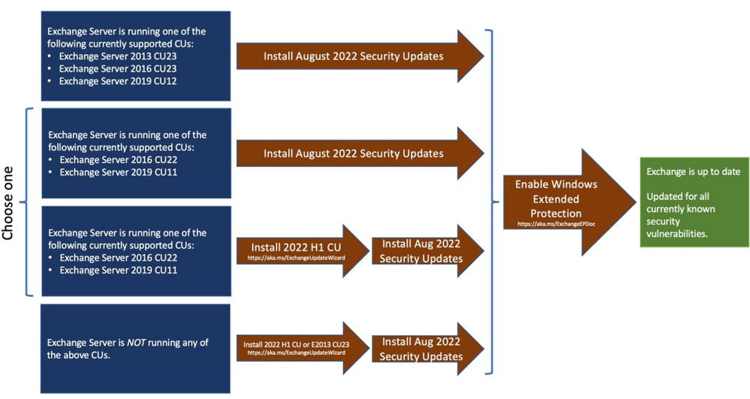
Before you can enable Extended Protection, make sure the following prerequisites are met:
There are also knows issues (Microsoft is working on this):
If you want to enable Extended Protection for all servers in one run, execute the PowerShell script without any options:
[PS] C:\Install> .\ ExchangeExtendedProtectionManagement.ps1
If you want to enable it for just a number of named server, using the following syntax:
[PS] C:\Install> .\ ExchangeExtendedProtectionManagement.ps1 -ExchangeServerNames EXCH01,EXCH02
Or if you want to exclude an Exchange server:
[PS] C:\Install> .\ ExchangeExtendedProtectionManagement.ps1 -SkipExchangeServerNames EXCH10
There’s also a rollback function you can use when you have undesirable results:
[PS] C:\Install> .\ ExchangeExtendedProtectionManagement.ps1 -RollbackType "RestoreIISAppConfig"
Summary
The August 2022 Security Updates for Exchange contain support for Extended Protection. The easiest way to configure this is to use the Microsoft PowerShell script. But be aware that all prerequisites are met before you start enabling Extended Protection. As usual, it is important that you install the updates and configure Extended Protection in your test environment first to see what the implications are, both on the server and the various clients in your organization.
More information regarding the Common Vulnerabilities and Exposures (CVE) and downloads can be found on the following locations:
Exchange Server Support for Windows Extended Protection - https://microsoft.github.io/CSS-Exchange/Security/Extended-Protection/
How do you ensure vital business communication, such as email, stays up and running? How do you demonstrate to senior management that additional resources are needed to meet growing demand or that service levels are being met? ENow makes your job easier by putting everything you need into a single, concise OneLook dashboard, instead of forcing you to use fragmented and complicated tools for monitoring and reporting.
Easy to deploy and intuitive to use, ACCESS YOUR FREE 14-DAY TRIAL and combine all key elements for your Exchange monitoring and reporting to keep your messaging infrastructure up and running like a pro!
PRODUCT HIGHLIGHTS

Jaap is a Microsoft MVP for Office Apps and Services. Jaap is an independent consultant, primarily focusing on Exchange server, Skype for Business and Office 365.


On January 10, 2023, Microsoft released new Security Updates for Exchange 2013 CU23, Exchange 2016...


This week Microsoft released new security updates for the following Exchange versions: