Active Directory Monitoring: Network AD Crashes
When a network issue leaves your domain controller stranded on an “island”
Your users know...


Years back, Active Directory (AD) was all the rage. I recall its release with Microsoft Windows Server 2000 and entire books were written on the subject, everything from design to deployment to continued maintenance. Over time, AD has lost its novelty as the shiny new toy, but it hasn’t lost its value as the foundation piece to all other aspects of your network and on-premises servers, like Exchange. That has held true even with its cloud-based cousin Azure AD. Nothing takes out the entire Microsoft 365 suite like an Azure AD outage because identity management and a host of other server necessities are tied back to it.
Source: Techgenix
Reputationally, AD is believed to just “work.” Historically, that’s not the whole story. Ask anyone that has chased after the needle in a haystack when an application is throwing errors due to an underlying AD issue that wasn’t immediately visible. It manifests with support tickets that revolve around the symptom (for example, “I can’t use application X”), but nothing points directly to it being a domain controller issue, a replication issue, an LDAP Kerberos issue, and so on. Tracking down the cause of the problem is near impossible and might take days or weeks. Providing visibility into these gaps is where ENow shines and makes the complex simple.
The first time I reviewed ENow (years ago), it solved a common problem of the day: Exchange monitoring. Today, ENow has expanded the scope to solve multiple problems that range in complexity, both on-premises and cloud-based. But they’ve maintained key pieces that benefit IT admins with a unified OneLook Dashboard that provides at-a-glance visibility into the current state of their Active Directory. Problems are literally called out with big blinking red lights with a breadcrumb trail that you can drill down on to locate the root cause of the alert.
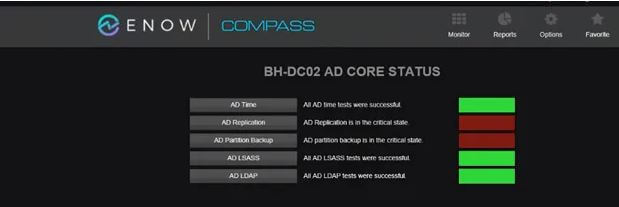
At times it’s not immediately evident that AD is the root of a problem. For example, you’re having an issue with Exchange Server, and you might think it’s a network issue or storage issue, but the connection between Exchange and AD functionality is so strong that it could very well be an AD issue. Distribution lists aren’t expanding, queues are building up… is it because the performance of domain controllers (DC) are choked out? How would you know if you didn’t have something monitoring the DCs? With AD issues, it’s often the last place you check for the problem because, again, reputationally AD is believed to just “work.” Underlying AD issues can choke the performance of AD in your environment, so added visibility from a monitoring solution is key to finding a resolution faster.
In 2020 a common AD issue that came up was in relation to the number of DCs in the subnet designed to handle incoming VPN connections. Imagine a setup that was prepared to handle a maximum number of connections at 10% of the company workforce concurrently. Suddenly, on a daily basis, it’s being asked to authenticate identity management for 90% to 100% of the company working from home and connecting through the VPN. Having more transparency into the overall scenario through monitoring and reporting would help you see the problem quickly and act to increase the number of DCs in that subnet.
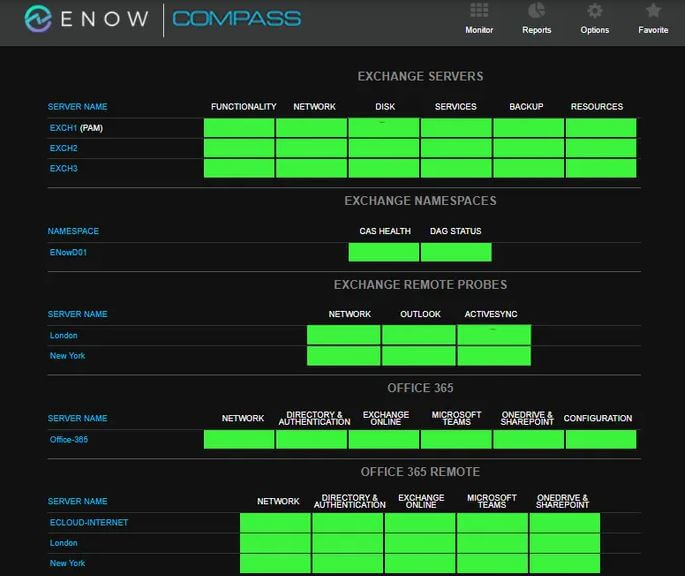
Key components being monitored include the following categories and subcategories:
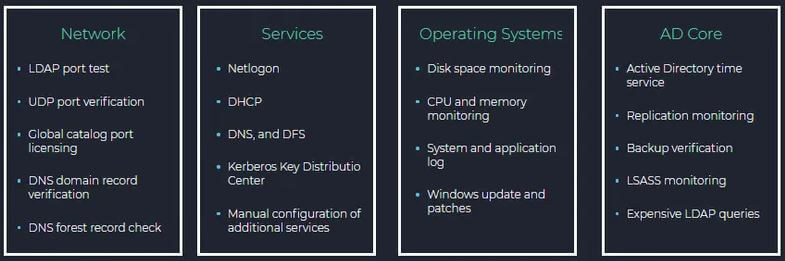
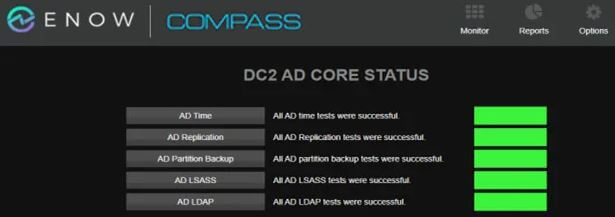
Reviewing these categories should help you to see the value of having a service that is monitoring them within your network. Some of them are obvious, but let’s consider a few. For example, under AD Core, the AD time service monitoring. Accurate time sync is essential for Active Directory because time synchronization issues lead to Kerberos authentication failures. The AD servers have to be within five minutes of each other. If servers are out of sync, clients may not be able to authenticate, and DCs might not be able to replicate. You can see how it would be good to know if a server is out of sync as soon as possible.
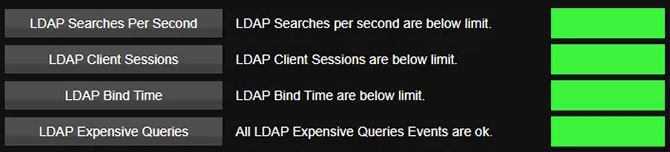
Expensive LDAP queries, that is, inefficient and long-running LDAP queries, can be another issue worth detection and intervention. An LDAP query can be run from a variety of tools (PowerShell, ldapsearch, VB Scripts), and typically standard queries are not a cause for concern. However, there are times when an LDAP query might be taking too long or utilizing too many resources and, again, that’s where having a tool that can discover these and surface them for IT can help to improve the overall performance of your AD environment.
Another LDAP-related security issue occurs when DCs let LDAP clients communicate without proper channel binding and signing. This vulnerability opens the door for MiTM (man in the middle) attacks. Knowing which DCs are allowing insecure LDAP connections is the key to ensuring those servers are up to date and configured properly.
Administrators quickly find that identifying what DCs are servicing LDAP binds in clear text is the easy part of the insecure LDAP situation. Currently, Microsoft does not provide an easy native method to see what specific users, devices, or applications are requesting insecure LDAP binds. The impact to the administrator is that he or she does not know what users, devices, or applications will stop working when configuring DCs to not service insecure LDAP binds.
ENow’s solution helps administrators out of this precarious situation by pinpointing DCs that are not rejecting insecure LDAP connections along with a detailed report listing each client IP address and username that are requesting insecure LDAP methods. This easy button provides the automated blueprint for the administrator to know what devices are using insecure LDAP within the organization and, most importantly, who. This approach allows the administrator the ability to go straight to the source and harden devices within the organization.
Note: Microsoft provides guidance for LDAP Channel Binding and LDAP Signing here.
Active Directory can suffer from replication issues due to DNS problems, network issues (firewall settings), time sync, or a bevy of other things that can cause replication to fail. Here is where you need to be able to see the failure and then drill down to find out the root cause. ENow’s monitoring solution can help you to do just that.
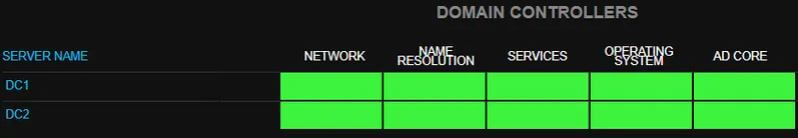
Those are just a few of the many important categories/scenarios being monitored that are essential to maintaining a healthy AD environment.
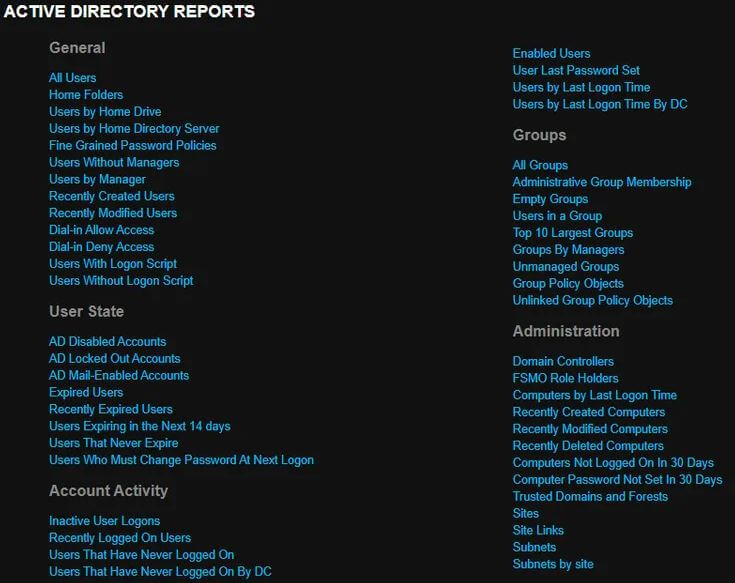
The platform also includes a wealth of information within the reporting library that administrators require to manage AD, such as AD Locked Out Accounts and Users by Last Logon Time by DC.
Any single technology can be monitored using a siloed solution. Monitoring AD in a vacuum environment is nice, but monitoring AD combined with a host of other solutions (on-prem and cloud) all at the same time allows you to see the bigger picture. It has to start with the DCs at the bottom, the foundation. And build up from there. That’s where the magic lies within the ENow solution suite. An oft misquoted line from Henry David Thoreau is “it’s OK to build your castles in the sky so long as you keep your feet on the ground.” His original line was more eloquent but carries the same meaning: “If you have built castles in the air, your work need not be lost; that is where they should be. Now put the foundations under them.” — Henry David Thoreau.
The point is this … if Active Directory underpins the entire catalog of Microsoft servers (on-prem or cloud) as the foundation point, then it stands to reason that you want to keep eyes on those AD servers, their underlying protocols (LDAP), various services (DNS, etc.), the OS of those servers (patches and updates) and key AD elements (time, replication).
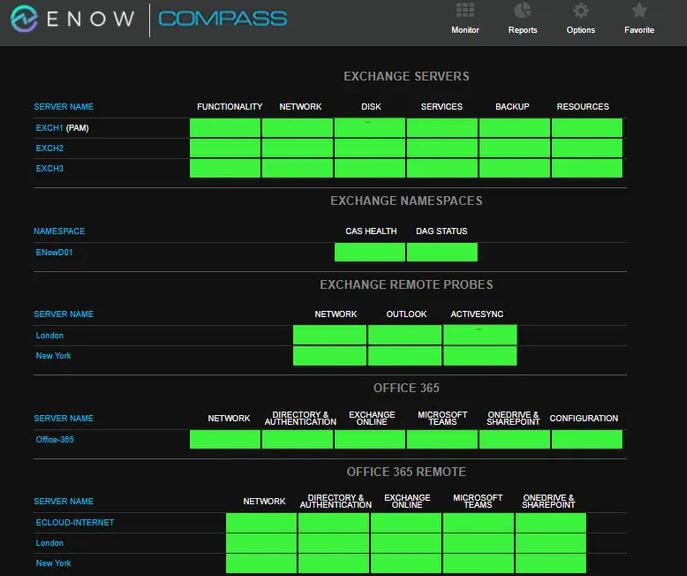
Having a solution like ENow’s AD Monitoring and Reporting will not only keep your AD environment humming smoothly, but it connects with the full suite of additional monitoring tools for Exchange, Office 365, and more. Full insight through one pane of glass is not only helpful for IT admins looking to do their jobs but also for IT decision-makers (such as the CIO or CTO) because it ensures improved organizational continuity.
When reviewing products, TechGenix has a scoring system between zero and five stars, with five stars being a perfect score. I give ENow’s Active Directory Monitoring and Reporting a score of 4.5, which is a gold star award.
 Rating 4.5/5
Rating 4.5/5
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

AmyKelly Petruzzella is a marketing executive who focuses on Microsoft Exchange, Office 365, and Active Directory trends, challenges, and business outcomes for enterprises. Over the years, AmyKelly regularly engages with Gartner industry analysts, and she has been recognized several times for Top 50 Microsoft Marketing Excellence. She is a frequent speaker and blogger and an industry veteran who advocates for women in technology.


Your users know...


The rising need for flexibility and ease of integration with other systems, either on-premises...