Basic Authentication Update - February 2022
The last couple of years we have seen several security breaches in IT, leading to serious impact...


Almost a year ago, in March 2020, I wrote an article called Microsoft stops basic authentication, now what on this site about Microsoft’s plan to decommission Basic Authentication in Office 365. The Covid-19 pandemic took over the world and a lot of projects were postponed. This was also the case of the Basic Authentication project at Microsoft, but the decommissioning is still planned although there are some serious changes in Microsoft’s planning. Time for an update.
Just a quick reminder, when using basic authentication, the user credentials are sent across the wire every time a resource is accessed. These credentials are sent using clear text, so they are easy to intercept. Now every website is using SSL to encrypt the connection between the client and the server so it’s not that easy to intercept. More important, it is very easy for a malicious user to start a brute force attack on the server and try every username/password combination that’s available. Usernames can be easily guessed in Office 365 and when using simple passwords, the results are clear: compromised accounts.
Modern authentication introduced with Office 2013 are based on tokens. When a user tries to access a cloud resource, the user first has to logon to either Azure AD or the internal Active Directory using ADFS to get an authentication token. Using this token, the user can access various cloud services. If you are interested in the details of this mechanism, please check my Basic Authentication in Office 365 blogpost. Furthermore, Office 365 Multi-Factor Authentication (MFA) only works with modern authentication and not with basic authentication. In shore, modern authentication is much safer than basic authentication, offers more functionality and is the way forward in Office 365.
Modern Authentication is used in all services in Office 365, so HTTPS (OWA, Outlook and Exchange Web Services), POP3 and IMAP4 and Authenticated SMTP.
To improve security in Office 365, Microsoft will decommission basic authentication and will only offer modern authentication. In contrast to earlier plans, Microsoft will not disable basic authentication for existing tenants if basic authentication is currently used for specific services/protocols. Microsoft will disable basic authentication when it is not used in your tenant. It will not just happen, but when Microsoft is ready to do this in your tenant you will receive a 30 days’ notice in your message center.
Other services/protocol will follow, but not on a short term and Microsoft will announce this a long time in advance.
Instead of waiting for Microsoft to disable basic authentication I strongly recommend doing the research in your environment and disable basic authentication where it is not needed. For example, I have been working with a customer that suffered from compromised accounts several times. Compromising attempts were made from all over the world as can be seen when monitoring logins from the Azure AD portal. After researching these events it turned out all (simple!) passwords were found using brute force attacks on IMAP4. IMAP4 was used at this specific customer, but only by a few users with specific needs, and they were all using modern clients that were able to support modern authentication.
In the Microsoft Online Portal https://admin.microsoft.com under Settings | Org Settings | Modern Authentication (as shown in the next screenshot) it is possible to disable basic authentication for specific protocols, so after disabling this for IMAP4 and POP3 a common attack vector was removed, and the number of failed attempts decreased drastically.
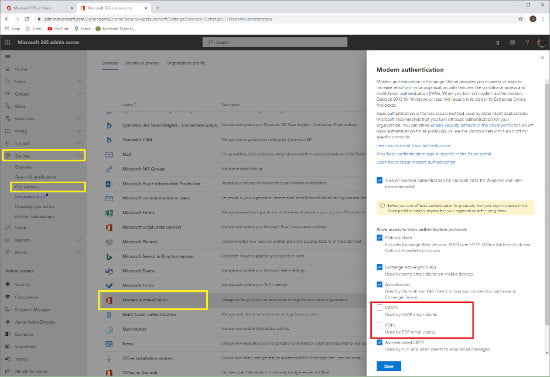
However, if you have a relatively new tenant in Office 365 a feature called Security Defaults is enabled. When you navigate to Modern Authentication in the Office 365 Portal you will get the following message:
“Your organization has security defaults enabled, which means modern authentication to Exchange Online is required, and basic authentication connections are blocked. You must turn off security defaults in the Azure portal before you can change any settings here.”
This is shown in the following screenshot:
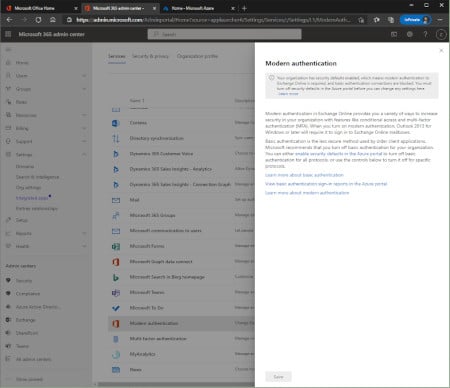
Security Defaults is a feature in Microsoft Azure that sets a number of security settings. Settings that are not enabled in ‘old’ tenants but according to Microsoft must be enabled for improved security. These settings include for example Multi-Factor Authentication for users and admins, but also blocking legacy authentication protocols. More information regarding this can be found on the Microsoft site What are security defaults?
So, in short, Microsoft will postpone disabling of blocking basic authentication for active tenants until further notice but will continue to block this for tenants that do not use basic authentication. For new tenants, basic authentication is already disabled by Azure Security defaults.
But this must not be a valid reason for you to stop your own projects. Please continue (or start) decommissioning basic authentication for your own environment to improve security.
On-premises components, such as AD FS, PTA, and Exchange Hybrid are critical for Office 365 end user experience. In addition, something as trivial as expiring Exchange or AD FS certificates can certainly lead to unexpected outages. By proactively monitoring hybrid components, ENow gives you early warnings where hybrid components are reaching a critical state, or even for an upcoming expiring certificate. Knowing immediately when a problem happens, where the fault lies, and why the issue has occurred, ensures that any outages are detected and solved as quickly as possible.
Access your free 14-day trial of ENow’s Exchange Hybrid and Office 365 Monitoring and Reporting today!

Jaap is a Microsoft MVP for Office Apps and Services. Jaap is an independent consultant, primarily focusing on Exchange server, Skype for Business and Office 365.


The last couple of years we have seen several security breaches in IT, leading to serious impact...


One of the most important aspects of moving to a cloud solution like Office 365 is to provide a way...