Authentication Planning in the Enterprise
What a great time to be an IT pro. I mean really, who has it better than us? On any given day there...

Ignite is Microsoft’s major conference for new announcements and training aimed at IT professionals. This year Ignite took place in Orlando, Florida the week of September 25th. I wasn’t able to make it to Orlando to be onsite for the conference this year, but it’s not that difficult to follow new announcements from Ignite from anywhere in the world.
In this blog post I’m going to give an overview of some of the announcements from Ignite around identity and authentication management for MS cloud services that caught my attention. I learned a lot by watching recorded sessions, hopefully I can pass some of that on here.
Passwords are terrible. Passwords are forgotten, reused, easily fishable, and hard to remember. There are so many reasons that we should move away from passwords as our primary way of identifying users.
Microsoft tends to agree, and they think it’s time for some innovative solutions. There are some new features of AD FS on Server 2016 that will allow users to authenticate to on-premises, cloud, and third-party applications without needing to use a password.
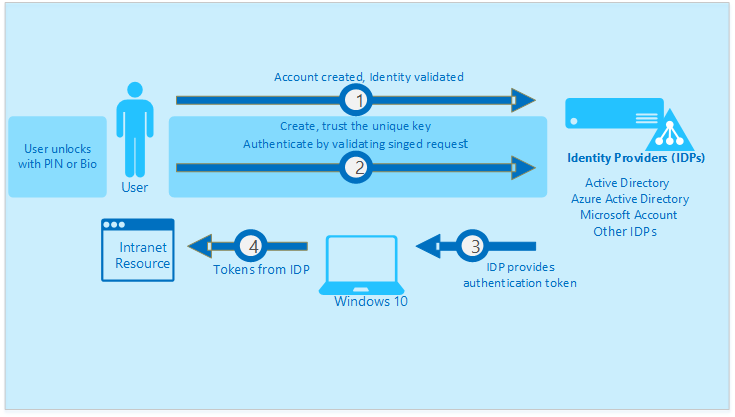
The first feature that caught my eye is Windows Hello for Business. The name is terrible, but I’m pretty sure Microsoft has a federal mandate to name products poorly. Moving past the name, this feature is the same thing as the Windows Hello you have seen on Surface laptops, only it allows you to authenticate via AD FS.
Windows Hello for Business creates a cryptographic key that is used as your “password.” That key is associated with your biometrics and stored in a TPM protected chip on your computer. Your biometric data never leaves your computer. It does require hardware that can properly collect that biometric data. I use Hello with my surface book, but there is other hardware from both Microsoft and other providers that meet the requirements of Windows Hello for Business.
One major problem with WHfB is that you need to have Windows 10. No down level Operating Systems are supported, as well as no mobile devices can use WHfB either.
You can setup your AD FS server to support WHfB for on-premises, cloud, and hybrid applications.
While WHfB does require 2016 AD FS servers, there are configurations that support using both current Windows Server 2016 servers as domain controllers, and older down level versions of server as well. When WHfB is configured in cert trust mode, you can have down level domain controllers in the domain with the AD FS servers. In Key Trust mode you will have to have all Windows Server 2016 domain controllers running Active Directory 2016.
Extranet Lockout is not a new feature for AD FS. It was actually introduced with Server 2012 R2 version of AD FS, but I don’t see it being deployed much. Extranet Lockout prevents user accounts from being locked out inside your network by attacks that originate outside your network. If there is a brute force attack against your user’s passwords, they’ll be locked out from the public side of the AD FS server but their accounts will not be locked out from directly accessing your domain services via a standard internal authentication session to a domain controller.
The new feature to Extranet Lockout I want to talk about is familiar IP. Familiar IP is only available with the version of AD FS that runs on Windows Server 2016. On those AD FS servers, it adds an extra layer of protection to Extranet lockout so that a brute force attack can be locked out only from IP addresses that the users has not authenticated from before. This means you can be working off the company network without a VPN connection, while being protected against brute force attacks. This may sound like a minor feature, but I’ve spent many hours debating the pros and cons of account lockout policies with customers, and this feature makes that discussion much more straightforward.
Seamless SSO is a cool new feature that allows limited Single Sign On for web applications without having to deploy an AD FS server. The name is a not a great descriptor because the “single” part of SSO really isn’t true. It should be called something like “Limited SSO in specific circumstances for the web versions of Microsoft cloud applications”, but I can see where Microsoft Marketing might not like that.
Seamless SSO is enabled by Azure Active Directory Connect, and works with either Pass-Through Authentication or Password Hash Synchronization. One the setup wizard screen where you choose PTA or PHS there is a check box at the bottom that say “Enable SSO.” That’s how you turn on Seamless SSO.
There are a few gotchas for Seamless SSO that you will need to know about before deploying it. The first one is that users will need to type in their user name when accessing web applications via Seamless SSO. Again, not a super “seamless” or even “SSO” experience. This limitation can be overcome if you set up Domain Hints, but that is an additional procedure that many organizations will not know about when they check that silly box to “enable SSO.”
The second gotcha is that the workstation being used need to be AD DS joined for Seamless SSO to work. That makes it a handy feature for computer inside the company network, but users will become frustrated if they expect it to work on personal laptops or off the company network.
But wait, there’s more! Seamless SSO does not work with the Edge browser! Seems like a terrible limitation since this feature is clearly meant to be used on Windows 10 workstations, and Microsoft pushes Edge so hard on Windows 10. Why do I say it’s meant to be used on Windows 10 workstations? It does work with Windows 7 or 8.1 workstations, but those machines will need to have the workplace join client installed. I guess that’s a fourth gotcha.
Once you get past those limitations, Seamless SSO is a pretty cool feature. It does allow you to achieve limited SSO for your end-users, it’s just that I think there are so many caveats that most organizations that try to deploy it will end up with more frustration that it’s worth.
Extranet Lockout updates, Seamless SSO, and some new ways to start moving your organization away from passwords. All good new tools from Microsoft.
Identity and Authentication management has always been much more intricate than most people imagine, but the move to the cloud is a huge influence on the complexity of this management task.

Nathan is a five time former Microsoft MVP and he specializes in Exchange, Microsoft 365, Active Directory, and cloud identity and security.


What a great time to be an IT pro. I mean really, who has it better than us? On any given day there...

I still remember the first password I ever had; it was for my GeoCities account in the late ‘90s...