How Microsoft Improved Its Identity Products and Services - September 2022
Microsoft’s identity portfolio consists of many products, like Active Directory, AD FS, Azure AD...


Identity Management . . . . a fancy term for keeping tabs on credentials with access to our systems. All cyber security attacks share a common factor: the attacker gained access to a system. Commonly, this occurs using compromised user accounts.
IT Pros often find themselves with overwhelming task loads. When faced with 12 hours of work and only eight hours to get it done, we often overlook the standard administrative tasks. Tasks such as offboarding credentials, identifying unusual authentication activity, and removing dormant accounts. I’ve seen this happen so frequently, I’ve named the condition “credential creep.”
Strategies abound for preventing credential creep. My favorite approach relies on IT using automated systems and reports, exposing potential concerns before any credential compromise. Mailscape and Compass provide numerous tests and reports giving IT immediate visibility into identity management issues. Let’s focus the rest of this article on three recent additions to the suite of tools, including one test and two reports; specifically, the Azure AD Authentication Test, the Recently Logged On Users Detail report, and the Domain Controller Authentication Activity report.
The Azure AD Authentication Test for Microsoft 365 performs authentication against Azure AD, displaying either an all good or an error state in the dashboard in the Office 365 Remote category under the Directory & Authentication column.
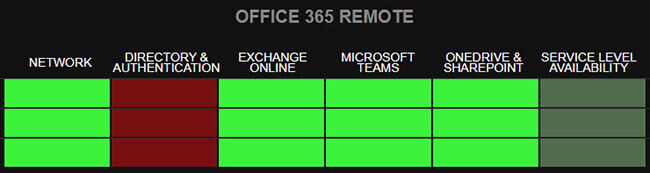
Clicking the block in the grid reveals detail about the test results. Drilling through these multiple layers exposes more information, helping you troubleshoot errors such as an expired password.
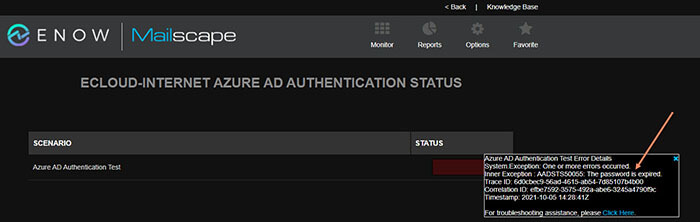
Monitoring the Azure AD Authentication Test results strengthens cyber security, helping IT quickly identify potential authentication issues with Azure AD. Coming up with scenarios where an attacker works to break Azure AD doesn’t take much imagination. Once inside a system, preventing others from accessing those systems is key to keeping the attacker’s foothold in place. The sooner IT Pros identify these attempts, the more likely they’ll successfully eject the attacker quickly.
Organizations with all cloud or hybrid cloud deployments utilizing Microsoft Azure really benefit from this test. Many critical functions depend on proper authentication through Azure AD. Everything from single sign-on applications to self-service password resets requires Azure AD. Identifying potential issues could make the difference between disgruntled users complaining to IT or fixing the problem before any user even notices. Proactive approaches always result in more robust customer service.
Each day, attackers breach countless systems because those systems rely on outdated authentication technologies. Unfortunately, post-mortem analysis frequently reveals organizations didn’t even realize they were using the compromised, outdated, insecure technology. Learning that an attack was preventable after the attack occurred is frustrating, not to mention expensive.
Active Directory remains the most commonly deployed identity management system. Organizations of every size and type, from small businesses to nation-states, rely on AD. Many of these deployments are as old as AD itself, dating to the early 2000s. These well-aged deployments create significant likelihood of systems still relying on outdated authentication technologies. The Domain Controller Authentication Activity report reveals not only if systems still use obsolete technologies NTLMv1 and NTLMv2, but how often they use them as opposed to the more modern Kerberos authentication technology.
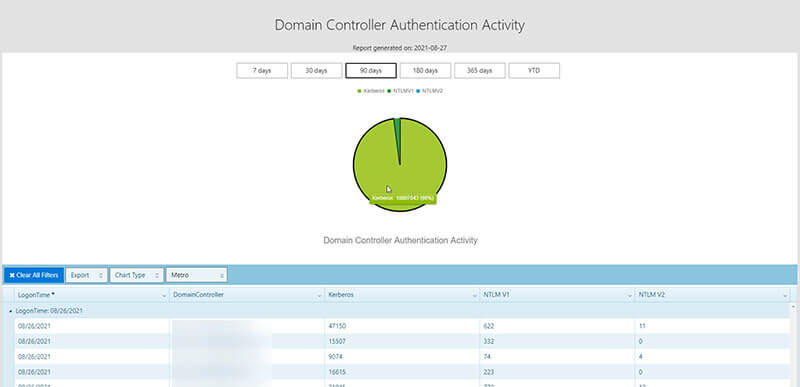
Why does it matter if NTLM remains used instead of Kerberos? How does Kerberos improve IT’s chances of fending off attackers? Answering these questions requires a quick look at the history and differences of the technologies.
NTLM pre-dates Active Directory. Microsoft replaced NTLM as the default Windows authentication protocol in Windows 2000. Current Windows versions keep Kerberos as their standard authentication protocol. Microsoft developed Kerberos to counter NTLM security vulnerabilities, including password hashing and salting attacks.
What is password hashing? Why is it a problem? How does salting help? Password hashing scrambles a password using an algorithm and input value producing a string of text, This string of text is the hashed password. As far as NTLM is concerned, the hashed password value is equivalent to the password. An attacker who steals the stored hash value from a system can authenticate without knowing the actual password. Salting adds to the password a unique, random string of characters known only to the identity management system. Systems usually add the salt to the beginning of a password before hashing. Using random salts produces unique hash values even when credentials use the same password. For example, even if user1 and user2 both have a password of “secret,” the salted hash value is different for each.
Both NTLMv1 and NTLMv2 send passwords over the network, whereas Kerberos does not. This improvement alone provides considerably enhanced protection.
NTLM relies solely on symmetric cryptography, while Kerberos supports both symmetric and asymmetric cryptography.
Kerberos supports authentication delegation, NTLM doesn’t. Authentication delegation enables logging into multiple applications using a single credential.
Kerberos supports Mutual Authentication, NTLM doesn’t.
Multi-Factor Authentication support is by far the most important and currently relevant difference between Kerberos and NTLM. Kerberos supports MFA, NTLM doesn’t. Why is MFA so important? For one thing, any organization with cyber security insurance they want to keep better have MFA in their plans. Many cyber insurance carriers already require MFA, those who don’t plan on implementing requirements soon.
Organizations with all cloud or hybrid cloud deployments utilizing Microsoft Azure really benefit from this test. Many critical functions depend on proper authentication through Azure AD. Everything from single sign-on applications to self-service password resets requires Azure AD. Identifying potential issues could make the difference between disgruntled users complaining to IT or fixing the problem before any user even notices. Proactive approaches always result in more robust customer service.
Another intangible benefit from the Domain Controller Authentication Activity report identifying the active logins to Domain Controllers and their associated protocols (Kerberos, NTLMv1, NTLMv2). This is extremely useful when going through an Active Directory upgrade project like moving to Microsoft’s new flagship operating system, Server 2022. One of the most significant issues we face when doing these projects is making the upgrade transparent to the end-users. I remember a large project where we had to ensure that there were no user interruptions during this AD upgrade process. This was a requirement because the Domain Controllers serviced Plant Operation Networks and Controllers (PLCs) on the plant floor that could not take interruptions.
Typically, what happens is IT pro’s will install a new Domain Controller then decommission the old one in a single change or outage window. This is a wrong approach because you cannot guarantee no active connections to the legacy domain controllers. Instead, we can tune the Service Records to adjust priority to the new domain controllers and slowly ween off the links to the old ones. The issue is in the past; we would have to use tools like Wireshark or Network Monitors to trace these connections. More importantly, we would also want to check the types of authentication protocols still in use.
We often find the highest volume of service desk tickets coming from Multi-Function Printers and devices that had hardcoded with LDAP Server entries either by IP Address or FQDN. Using this report and the Service Record Tuning process allows for seamless and transparent Active Directory migration projects.
As IT Pro’s we often are faced with choices, such as the choice between the right path or the easy path. Especially with the cyber security landscape today and the wave of Ransomware attacks plaguing organizations, taking the easy path is a hazardous one. What do I mean by the easy path? Well, let me tell you a little story. One day, there was an IT Administrator named John; John had a task to install a new monitoring application that would check the health of servers in the enterprise. This application required elevated permissions to install, run, and monitor these servers. In the installation User Interface, there was a prompt to input a service account. Instead of creating a Group Managed Service Account with delegated, low privileged rights and constrained authentication, John chose the easy path. His account that he used for elevated administrative rights had Domain Admin privileges. So his installer ran without any errors and John was able to go home at the end of the day enjoying time with his family.
John didn’t know that his Administrative account was being used and spawned by the application and created a massive security hole for the organization. This account sat inside of the monitoring tool for months and months.
Then one day, a threat actor attacked John’s organization and gained administrative access to one of the servers on which John’s monitoring tool was installed. The attack was able to do a credential dump and figure out John’s Administrative password. Now quickly, the threat actor (Bad Guy) elevated his access to full-on Domain Admin. This account was used soon to set up a C2C (Command and Control) services and spread admin-level ransomware throughout the organization. Why am I writing about this today? Because it is tough to find these accounts inside of your organization. I want to point out the screenshot below showing John’s Admin account logging in over 80,000 times over the past 30 days. This Recently Logged On Users Detail report Mailscape offers is precious to the Security Operations Team, empowering them to identify the incorrectly configured elevated service accounts.
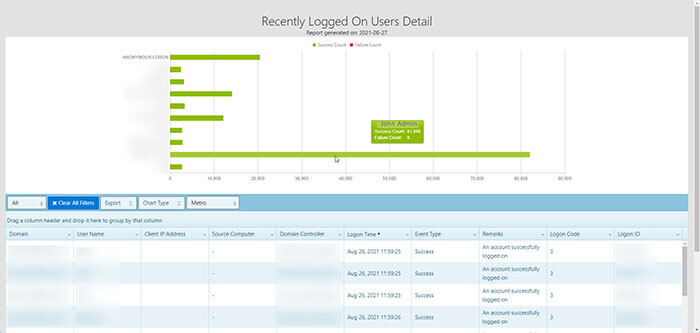
As you can see, these tests and reports offer invaluable information to the IT organization. These reports represent only a few included with the suite of default reports from ENow’s Mailscape and Compass tools. These tools prove you know what you know, but identify what you don’t know you don’t know. You can’t manage what you can’t measure. The unknown are holes in your cyber security. These reports quickly help you close those holes.
Attackers spend 40 hours a week, every week, devising methods to compromise your security. Their funding and support is 100% devoted to compromising any system with weak identity management. Rejecting their attacks successfully requires implementing a strategy using automated tools and reports. These systems empower IT Pros tasked with numerous responsibilities to counter evolving threats.
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Re-Connect Microsoft MVP


Microsoft’s identity portfolio consists of many products, like Active Directory, AD FS, Azure AD...


With organizations moving workloads to the cloud, they no longer have the...