How Microsoft Improved Its Identity Products & Services - August 2022
Microsoft’s identity portfolio is huge and includes products and services like Active Directory, AD...

A new year has dawned . . . and there's smooth sailing with Active Directory updates.
In the January 2023 cumulative updates for all current versions of Windows Server, Microsoft addressed two LDAP vulnerabilities affecting Domain Controllers:
The combination of these two vulnerabilities felt uncomfortable on Patch Tuesday itself. There was a risk that this update was another rogue update that could affect the availability and/or integrity of Domain Controllers. On the other hand, not updating meant that Domain Controllers would go down during the next red team exercise, or whenever an attacker got their hands on an exploit and a way to abuse the second vulnerability…
After the rocky November 2022 updates and the subsequent fixes in an out-of-band update and the December 2022 cumulative updates, it’s a relief that the January 2023 cumulative updates for Windows Server can be evaluated as ‘safe’ updates.
Although support for Windows Server 2008 and Windows Server 2008 R2 has ended, Microsoft has made updates available for all Windows Server platforms through the Extended Security Update program. The January 10, 2023, updates are the last updates for these platforms. If you have any Domain Controllers running Windows Server 2008 R2, or earlier versions of Windows Server, migrating, in-place upgrading, or transitioning to a newer version of Windows Server should be your top priority.
There are many benefits to upgrading to newer versions of Windows Server on Domain Controllers and to newer forest functional levels. Starting with the Windows Server 2012 Active Directory Domain Functional Level (DFL) you get Kerberos support for claims and the Windows Server 2012 R2 level brings additional features to the Protected Users security group. Starting with Windows Server 2016, Domain Controllers offer all the greatness you need for Windows Hello for Business Hybrid Access. Windows Server 2019 and Windows Server 2022 (the current version of Windows Server, and the n-1 version) are the main focus of the Active Directory engineering team, so getting to these versions is a big plus, even if the Windows Server 2016 functional levels are the highest ones available.
With version 6.7.2 of the Microsoft Authenticator app for iOS, Microsoft has removed the Authenticator Companion app for Apple watches. It simply isn’t compatible with the Number Matching feature that Microsoft will be pushing from the end of February 2023 (planned).
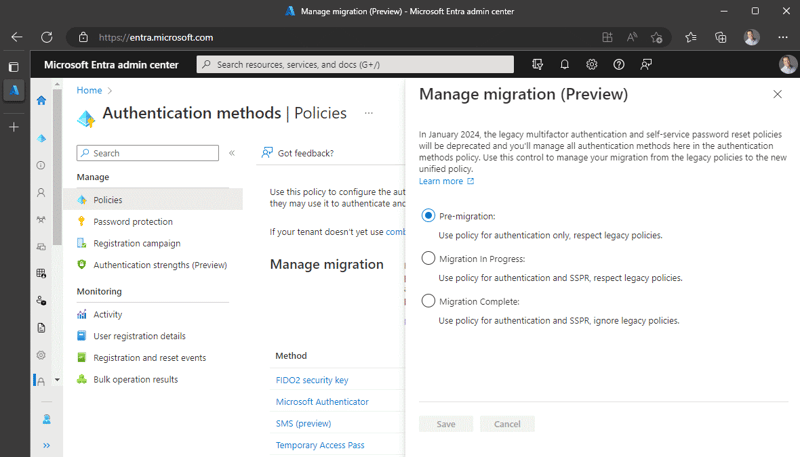
The Authenticator app is still one of the best and user-friendly methods to fulfill the requirement to perform multi-factor authentication, but many organizations are looking to decommission older and less-safe methods. Next to the Authentication Strengths feature (still in Public Preview), Microsoft is now actively promoting a method to manage all the authentication methods in one place. In the Azure AD portal and Entra portal, on the Authentication Methods blade, Microsoft announces that starting January 2024, the legacy multi-factor authentication policies (in the PhoneFactor portal) and self-service password reset policies (underneath Password Reset) will be deprecated. The Authentication Methods blade becomes the place to manage all authentication methods. Organizations can now pre-sort for this change by managing the migration (Preview):
Another feature in cross-organization collaboration, labeled Cross-tenant synchronization was also released as Public Preview for organizations using Azure AD. This new feature goes beyond the Azure AD B2B Direct Connect functionality by granting access to more than Teams Shared Channels and does away with the invitation redemption process that is still associated with ‘normal’ B2B and the self-signup functionality in both Azure AD and Azure AD B2C.
When working with Azure AD Connect Cloud Sync, admins were surprised by the new admin experience. With a guided experience for first-time configuration, and more intuitive controls, Microsoft aims to lower the threshold for admins to switch from Azure AD Connect Sync to Azure AD Connect Cloud Sync.
Admins who were on the fence about Azure AD Connect for its inability to synchronize attributes from custom Active Directory schema extensions, there is also good news. Azure AD Connect Cloud Sync now supports this functionality, bringing it closer to Azure AD Connect Sync. However, there are still a lot of features that don’t work with Azure AD Connect Cloud Sync. I can’t wait for the team to support Exchange Hybrid WriteBack, myself.
Wouldn’t it make you sad if something happened to Defender for Identity monitoring your Domain Controllers? That’s the question the team has asked itself. In version 2.196, released on January 10, 2023, Microsoft introduced new health alerts for its Defender for Identity sensors. You’ll receive alerts when auditing is (no longer) configured correctly in Active Directory and/or when Domain Controllers are (suddenly) configured with inappropriate Power settings.
If hunting is your game, then the team also got your back. They added MITRE ATT&CK information to the IdentityLogonEvents, IdentityDirectoryEvents and IdentityQueryEvents tables in Microsoft 365 Defender Advanced Hunting. In the AdditionalFields column, admins can find details about the Attack Techniques and the Tactic (Category) associated with some activities.
The Identity division at Microsoft has delivered great new value in January 2023. They didn’t even need to break anything to get the functionality to us. Let’s see if the February 2023 cumulative updates offer the same great experience…
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users who have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits.

Sander's qualities extend beyond the typical triple-A stories in the area of Identity and Access Management. Of course, authentication, authorization and auditing are necessities but my out of the box solutions get the most out of software, hardware and the cloud. Rapid technological advancements have resulted in cutting-edge solutions around Active Directory, Azure Active Directory and Identity Management. Keeping up with these is just a small challenge, compared to my true goal: helping people use the technology on a daily basis. In a way that ICT is not a mere hurdle, but an infinite enabler. His work as a consultant, blogger and trainer are all means to achieve this goal. His multiple Microsoft Most Valuable Professional (MVP) status, Veeam Vanguard status and extensive certification aids him. Through direct communications with the product teams in Redmond, he remains up to date, exchanges feedback and accelerates support. Sander is also a Virtual Product Owner for AppGov and ENow.


Microsoft’s identity portfolio is huge and includes products and services like Active Directory, AD...


Recap of ENow’s webinar discussing the importance of Active Directory Monitoring & Reporting, and...