How Microsoft Improved Its Identity Products & Services - August 2022
Microsoft’s identity portfolio is huge and includes products and services like Active Directory, AD...


Microsoft is discontinuing support for Windows Server 2012 R2 on October 10, 2023. With less than six months of extended support left, administrators are finally feeling the pressure and taking action.
Domain Controllers are at the heart of every Microsoft-oriented networking infrastructure, yet many admins procrastinate migrating these servers in order to avoid major disruptions. However, over the last couple of months many organizations have contacted me for assistance migrating off Windows Server 2012 R2 as their Domain Controllers. With Microsoft discontinuing support for Windows Server 2012 R2 on October 10, 2023, and less than six months of extended support left, NOW is the time to act!
Regarding Active Directory, Microsoft has an ‘n + n-1’ policy, meaning that the latest release of Windows Server is actively supported, plus one previous release. At the time of writing, this includes:
Based on the number of inquiries I’ve received, it would appear that not many Active Directory admins are aware of this statement, but at least their Domain Controllers fall within Microsoft’s support after upgrading to Windows Server 2019 or Windows Server 2022. When Domain Controllers no longer receive support from Microsoft, this means that:
Furthermore, the October 10th 2023 timeframe indicates that your Windows Server 2012 R2-based Domain Controllers no longer receive security and/or time zone updates. This is a sure recipe for cyber disaster.
Believe it or not, there are still some valid reasons as to why an organization would choose to go with Windows Server 2019 instead of Windows Server 2022 for their new Domain Controllers. Yes, you read that correctly – sometimes, going with Microsoft’s latest and greatest doesn’t always make sense for an organization, although most reasons are typically monetary.
One possibility is that the Client Access Licenses (CALs) for the organization only cover Windows Server features up to Windows Server 2019, and since Domain Controllers are typically used to access pretty much everything, CALs would be required for every user account. Therefore, if it came down to acquiring CALs for an entire user population, this could be determined a wildly excessive cost, and an impetus to explore other options.
Another potential scenario is that the organization’s build environment may be completely based on Windows Server 2019. Therefore, introducing Windows Server 2022 on Domain Controllers while every other server runs on Windows Server 2019, usually isn’t the best choice. The new Windows Server installations tend to be one-offs, and with that comes very little knowledge and experience around the new Operating System (OS). This may lead to the OS version being first to blame, scapegoated when any problems arise, even though the newer OS may not be the culprit nor the best place to start with Active Directory troubleshooting.
Most often, I see the majority of organizations migrating Domain Controllers straight over to Windows Server 2022, which is the recommended course of action when comparing Windows Server 2019 and what it offers in terms of default security benefits and networking settings. Windows Server 2022 is supported until October 14th, 2031, whereas Windows Server 2019's support lasts until January 9th, 2029, meaning the Domain Controllers will enjoy support longer.
There are three main ways to upgrade Domain Controllers: The Fast; The Reliable; and The Hard Way. The SWOT analyses below breaks down the pros and cons for each method, both short-term and long-term, to help you better identify the best course of action for your organization.
While Windows Server 2012 and Windows Server 2012 R2 do not support an in-place upgrade directly to Windows Server 2022, you can insert the (virtual) disk containing Operating System files twice and perform an in-place upgrade of Domain Controllers, twice.
The result is Domain Controllers containing all the same software, drivers, and settings of the previous Domain Controllers, as-is. It’s important to note, and something many admins do not realize, is that ‘as-is’ means the controllers will retain temporary settings in addition to the older/previous settings:
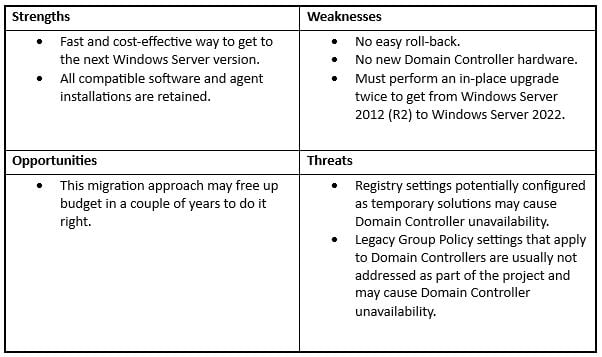
In the long run, these older registry and Group Policy settings could hurt the information security posture of the organization.
Alternatively, you can place new Windows Server 2022 installations alongside your Domain Controllers, and promote these to additional Domain Controllers. Then, after redirecting all the Active Directory traffic to the new Domain Controllers, you would decommission the old Domain Controllers:
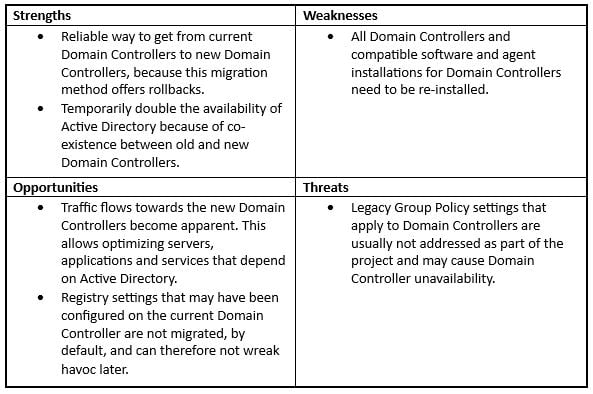
This method offers a reliable roll-back based on Active Directory site definitions, mainly while the end state is optimized. For Domain Controllers without the older settings, it will not eliminate temporary and old settings on the Active Directory level, because Group Policy settings applying to Domain Controllers are typically not addressed during the migration process.
Lastly, you could set up a new Active Directory Forest. This entails migrating over all user objects and groups while simultaneously switching over Active Directory-integrated functionality:
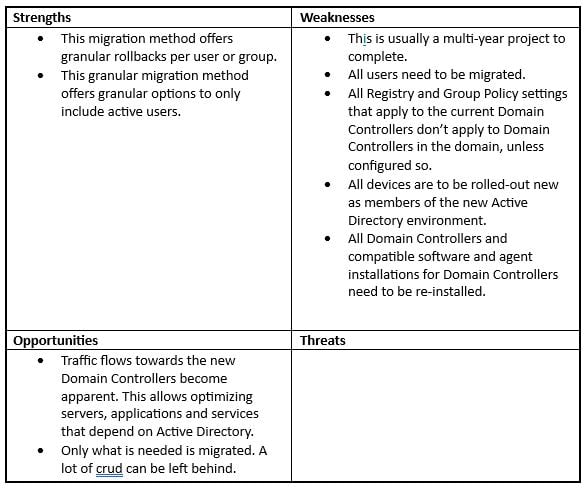
If your organization decides to take the new Active Directory Forest route, your future Active Directory environment will inherit less of a mess, and as you can see there is not the same level of threat potential like there is with in-place upgrading and transitioning. But if cross-forest migrating isn’t an option, you’ll obviously have to pick between in-place upgrading and transitioning.
Again, I typically see most organizations take the recommended route of migrating Domain Controllers directly to Windows Server 2022, because of these reasons.
When transitioning Domain Controllers and during cross-forest migrations, redirecting Active Directory traffic from the current Domain Controllers to the new Domain Controllers is typically the hard part. But it doesn't have to be, if you have a proper Active Directory Monitoring and Reporting solution in place that provides you with information on all the traffic flows between Domain Controllers, along with traffic from domain-joined servers and devices. Of course, most Active Directory-integrated functionality can be switched over using Active Directory sites.
However, by assigning the current Domain Controllers in sites without subnets, the Domain Controllers will no longer be advertised as 'closest' and typical traffic is then redirected to the new Domain Controllers that remain assigned. This approach will usually capture approximately 80% of all traffic flowing to Domain Controllers, but it's the remaining flows that may cause and wreak the most havoc. You’ll need visibility to the specific traffic flows outlined below.
Every Domain Controller acts as a Lightweight Directory Access Protocol (LDAP) server, offering directory access to many non-Microsoft applications, services, and servers. Many self-developed solutions also typically use LDAP. However, whenever I mention LDAP, I should mention LDAP as it relates to SSL. LDAP is often used instead of LDAP over SSL (LDAPS) as LDAPS is more difficult to configure, requiring name resolution and certificates.
That’s right - when an application, service, or server is correctly configured for LDAPS flows, it points to the Active Directory domain name, uses DNS, and follows the Active Directory site information. When configured for LDAP, these applications, services, or servers are typically configured with the IP address of a Domain Controllers.
If you are considering migrating your Domain Controllers, now would be a good time to reconfigure these applications, services, and servers to use LDAPS for the following reasons:
One of the main differences between Windows Server 2012 and Windows Server 2019 (and beyond) is the default availability of v1 of the Server Message Block (SMB) protocol. Every Active Directory Domain Controller is a file server, by default, to host the Netlogon and Sysvol shares. As such, they offer SMB.
By monitoring connections to the Domain Controllers for a period, SMBv1 traffic flows can also be monitored. If these still occur, you can reconfigure or upgrade the application, service or server to use at least SMBv2. If this is not possible, some Domain Controllers may need to be configured to offer SMBv1.
There are many other backward-compatible protocols and encryption algorithms that may no longer be in use, that could also be disabled. You’d be surprised how often a temporary Group Policy setting (not) configuring NTLMv1, NT4Crypto, SSL 3.0, TLS 1.0 and TLS 1.1, or any other of the vital security settings, ends up and remains in the ‘Default Domain Controllers policy.’ Sometimes, it feels like as the only thing permanent in IT are temporary fixes…
Because unfortunately, these settings won’t change themselves and Microsoft is hesitant to change these settings overnight as they may cause Domain Controller unavailability. We’ve seen Microsoft change some settings over the years, just so things don’t break. But if you make incremental adjustments, setting by setting, month by month, in a typical change management process - these changes are achievable.
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. While there are Domain Controller migration suites available that can provide the specific information you need at the moment, having an Active Directory monitoring solution already in place can play a huge role in ensuring your Active Directory transitioning project is a success. The ENow Active Directory Monitoring and Reporting tool helps you smoothly transition Domain Controllers, providing information on the LDAP and LDAPS traffic flowing to Domain Controllers and its Authentication Activity report splits out NTLMv1 from NTLMv2 and Kerberos traffic.
Additionally, the ENow Active Directory Monitoring and Reporting tool will help uncover any cracks in your Active Directory infrastructure that can cause a security breach or poor end-user experience, enabling you to quickly identify and remove users who have inappropriate access to privileged groups such as Schema Admins, Domain Administrators, etc. While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits. Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits.

Sander's qualities extend beyond the typical triple-A stories in the area of Identity and Access Management. Of course, authentication, authorization and auditing are necessities but my out of the box solutions get the most out of software, hardware and the cloud. Rapid technological advancements have resulted in cutting-edge solutions around Active Directory, Azure Active Directory and Identity Management. Keeping up with these is just a small challenge, compared to my true goal: helping people use the technology on a daily basis. In a way that ICT is not a mere hurdle, but an infinite enabler. His work as a consultant, blogger and trainer are all means to achieve this goal. His multiple Microsoft Most Valuable Professional (MVP) status, Veeam Vanguard status and extensive certification aids him. Through direct communications with the product teams in Redmond, he remains up to date, exchanges feedback and accelerates support. Sander is also a Virtual Product Owner for AppGov and ENow.


Microsoft’s identity portfolio is huge and includes products and services like Active Directory, AD...


Active Directory, AD CS, Azure AD Connect, and Azure MFA Server are all Microsoft on-premises...