Deploying Azure Active Directory Connect 1.1
Active Directory Synchronization for Office 365 and Azure has been a vital, but fairly straight...


Conditional Access is a premium feature of Azure Active Directory that allows administrators to specify conditions under which users can authenticate into other cloud services. With conditional access, you can specify that a certain set of users can only authenticate to specific applications from specific IPs for example.
The hard part about conditional access is that it takes a lot of work to configure and test the policies. Ensuring that you know how a policy is going to affect your users is critical. In this blog post I’m going to look at a new tool in the Conditional Access line that helps with this problem. "Azure-Active Directory-Conditional Access-What If" gives administrators a new way to test Conditional Access policies to see what the effect of applying those policies will be.
Before we get into the new What If tool, let’s take a quick look at Conditional Access and see what capabilities it gives us.
One of Microsoft’s major goals with Office 365 and Azure is to allow end-users the ability to access their data from any device at any time. While this is a great goal, sometimes administrators and organizations need the ability to control how end-users access the companies’ data. Conditional Access is a set of controls within Azure Active Directory that allows administrators to control end-user’s access to data with a policy-based tool. Conditional Access polices work on the concept of “when this happens, do this.” For example, you can build a Conditional Access policy that says, “When contractors try to access OWA from untrusted networks, block access.” The two parts of these policies are called conditions and controls. Conditional Access is a premium feature of Azure Active Directory, so it will not be available to you with your standard Office 365 subscription. You will need to signup for a EM+S E5 or Azure AD Premium P2 subscription to try out Conditional Access. There are trials available for both of these subscriptions.Conditions require you to define a sub-set of your users to whom this policy should apply. The best practice suggestion would be to define your Conditional Access policies based on group membership, not explicitly define users. If necessary, you can exclude users from a policy by exempting them, but it is still recommended to use a group for this action.
The next step in defining your Conditional Access policies is to define what cloud apps this policy applies to. The list of cloud apps that Conditional Access policies can apply to is extensive and includes many third party (non-Microsoft) apps.
Finally, the conditions section of your policy can include things like locations, sing-in risk, client apps, or device platforms that you want to allow or dis-allow.
The controls section of your Conditional Access policies. There are two types of controls: Grant and Session.
With Grant controls, you can either grant or block access completely, or you can allow access with additional requirements as shown below.
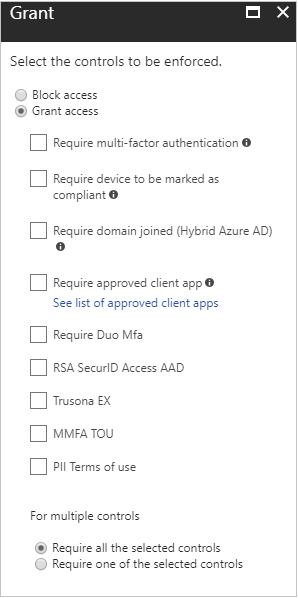
If you have an Azure AD Premium P2 license, you can also use custom controls from a third-party provider. Current providers that offer controls compatible with Azure AD are Duo, RSA, and Trusona.
Session controls enable a limited experience within the specific cloud app once the user is authenticated. Session controls are enforced by the cloud app itself once the user is granted access. Currently SharePoint Online is the only cloud app that supports session controls.
The above is just a brief overview of the control available within Conditional Access. As you can see, there is a lot to define in your policies, and in larger organizations with multiple policies it’s easy to create an overwhelming situation. The purpose of the What If tool is to give administrators a view into what will happen if they apply a specific policy.
Activating the What If tool is done on the tool bar at the top of the list of policies as shown below.
Once the tool is started, the administrator will need to specify the settings for the test as shown below.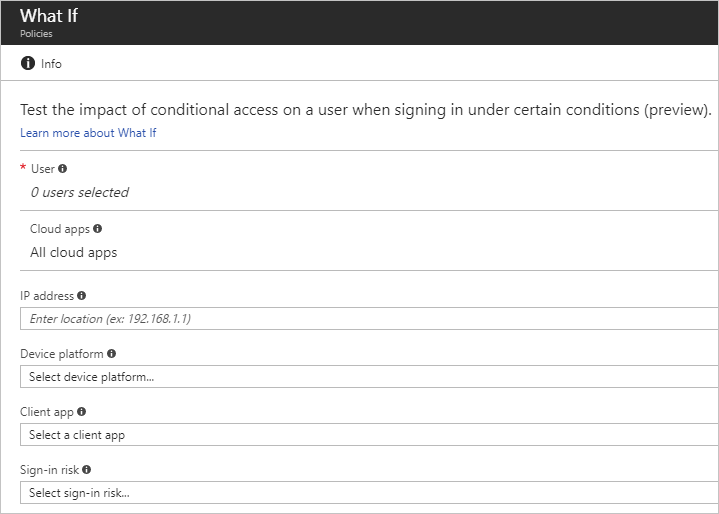
You can only select one user, and that is the only required field. The other settings fields are optional and are there to help refine the testing.
Once the What If tool is run, you will receive a report showing
Azure Active Directory Conditional Access is a rich tool that allow administrators a lot of control over the use of your organizations Microsoft and third-party cloud apps. Because Conditional Access is so complex and has so many controls, the What If tool has recently been added to give administrators a better way to figure out which policies apply to which users.
Conditional Access is a premium feature, so it does require additional licensing to use, but this is a security feature that many organizations will want to use.

Nathan is a five time former Microsoft MVP and he specializes in Exchange, Microsoft 365, Active Directory, and cloud identity and security.



By now, Azure AD Conditional Access should no longer be unfamiliar to anyone in IT. As...