Cisco’s ACE appliances and modules are something that I see constantly at customers. Unfortunately, Cisco’s application specific documentation is rather lacking. There’s a rather simplistic sample config on Cisco's site.
The problem is that information does not provide you with everything you need. The folks at F5 on the other hand have extremely well documented application guides for their hardware and that’s one of the reasons I usually send customers to F5 first. The contents of this post are essentially the same for ACE appliances and ACE modules.
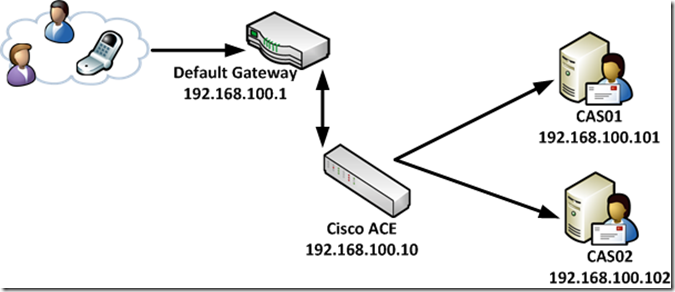
In any case, the rest of this post is a working sample configuration for the topology below. A thread on a discussion alias prompted me to clean this up and post it.

In our sample configuration, we’ll configure the load balancer in a one-armed configuration with Source NAT (SNAT). Clients will access services via the mail.contoso.com and autodiscover.contoso.com URLs. In addition, clients who go to a non SSL URL or go to the root instead of /owa will be redirected.
Before we get started, a few pre-requisites:
- You should have a working context on your ACE appliance/module with resources allocated.
- Your CAS servers should have static ports configured as described here.
- Your SSL certificate and the necessary intermediate and root certificates should be installed on the load balancer.
- A VIP will need to be allocated. We’ll use 192.168.100.200 in this sample
- If you’re expecting more than ~65K client connections, you’ll need to use more than one IP in the SNAT pool. This example assumes one is enough. We’ll use 192.168.100.199 in this sample.
The entire config is posted here: