Microsoft 365 Security Assessment Part 2
Last week I shared part one of my Microsoft 365 Security Assessment where we took a deep dive into...

Scenario 1: You are part of the IT team that is responsible for moving to the cloud. Your company/organization has chosen Microsoft’s cloud services as the provider of choice, for your new virtual datacenter. During the planning phase to migrate your current solutions to Azure and Microsoft 365, your risk department requests information about security and compliance, and how the shift from your current “private” datacenter to a public center will impact security. You end up Googling and stumble upon a Microsoft post that talks to Security defaults and what it is.
Scenario 2: You manage your companies cloud infrastructure and have been tasked with improving the security posture of your tenant. You stumble across the “Manage Security defaults” link in Azure Active Directory and wonder what it all does should you hit the “Enable” slider.
Naturally, since it's Microsoft, you trust the information, but does it really address all your needs as an organization? Let’s have a look at what “Security defaults” are and what they do.
Important note: Security Defaults apply to all users in your organization. ALL USERS.
Probably the biggest component of Security defaults is multi-factor authentication. Its is the single most impactful security enhancement you can add to your public cloud datacenter. Adding another layer of authentication over that of the traditional username and password mechanism. A 2019 survey conducted by Microsoft reported that two factor authentication can reduce the risk of identity compromises by as much as 99.9 percent, over passwords alone.
This goes hand in hand with MFA. Legacy or “Basic” Authentication is a term Microsoft uses to describe older authentication methods, in this case being the username and password method. Typically, it is used by an application that requires a logon token on behalf of the user. Think IMAP, POP3, SMTP. Phishing attacks are all the rage right now, and once an attacker has the users credentials, they can still bypass MFA if legacy authentication is enabled because 2FA (two-factor authentication) is not supported with legacy auth. Disabling/Blocking is slightly trickier due to organizations still using applications that use “Basic” authentication.
This feature forces the usage of MFA when accessing the Azure portal, PowerShell or CLI, including MFA on all administrative accounts. Security defaults will also only allow access to these actions/roles using the Microsoft Authenticator app.
There are a few caveats to all of this:

I would strongly encourage customers to make sure that security defaults are “enabled” when looking to bolster their security posture if they do not have an Azure Active Directory Premium Plan. It’s a huge step in the right direction. Right? But organizations are not that simple though.
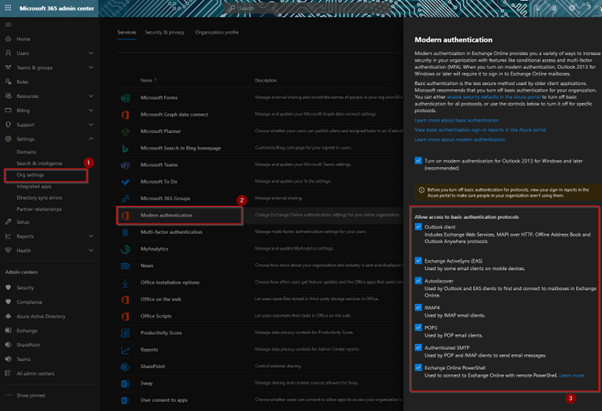
The figure below represents the settings of a tenant without security defaults enabled. Item 3 is available for administrators to configure should the organization still have applications that require it. You can enable Modern Authentication for Outlook clients but then decide what Legacy Authentication protocols you would still want to run for applications that require those services.
Ergo, applications that use those services will stop working if you switch on Security defaults. The option to granularly configure those settings are removed as well.
My favorite security feature from Microsoft; Conditional Access and its configurable policies allow organizations the granularity to decide who has access to what, from where and from what device. It’s based on the principles of Zero Trust and provides organizations with the freedom to extend security features to users far beyond that of the simple allow/deny rule of yesteryear.
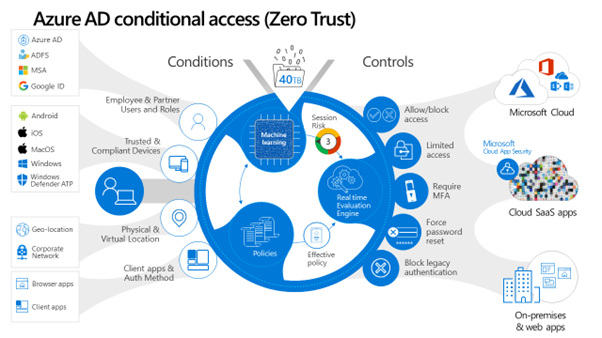
With Conditional Access policies, organizations can not only enforce rules based on risk profiling but also identify and remediate any identity and access management flaws in their tenant. You might want to only allow legacy authentication from applications that you define as safe, or you may decide to not enforce MFA from your offices. All this can be done with Conditional Access.
There are a few things you would want to check before you flip the switch:
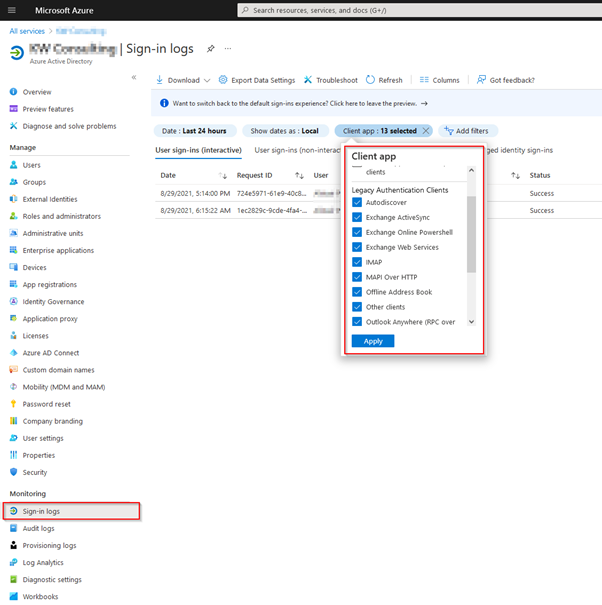
Microsoft makes it real easy to enable Security defaults. It's just a slider in the Azure Portal. The ramifications of flipping that switch could very well bring your organization to a grinding halt. Make sure that you are meticulous about identifying the items listed above, and make sure that you have a mitigation plan implemented before you flip that switch.
In closing, the impact of switching on Security defaults should not be taken lightly. My tips to rolling out Security defaults, are as follows:
By understanding the benefits of Security defaults, organizations will be better equipped with making sound decisions pertaining to their security posture. Make sure you know, before you go.
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

M365 + Security MVP | Blogger | Podcaster | Speaker | Founder, CEO - YModernize
Alistair has worked in various capacities in multiple verticals from retail-manufacturing to government, spanning 50 to 50000 users utilizing all aspects of pure Enterprise Information Management.
Specialties: 20+ years pure IT, 16 years ECM, Livelink, Zylab, SharePoint, FileNet, etc. IT Pro dabbling in Dev, ECM Consultant, Suffering from Technophilia. Technology Architect specializing in Business Productivity Enrichment.


Last week I shared part one of my Microsoft 365 Security Assessment where we took a deep dive into...


Microsoft introduced the feature Publisher Verification to help administrators to stay on top of...