Recently I had to upgrade my Azure AD Connect server from version 1.x to version 2.x, and I blogged about in my December 2021 blog article "Upgrade Azure AD Connect from 1.x to 2.x". After the upgrade I had to upgrade my Azure Active Directory Password Protection services as well since I installed a new server and decommissioned the old one.
Looking at the number of compromised accounts, I don’t think a lot of customers are using the Password Protection service. That's a shame because it can help you create a safer environment.
Azure AD Password Protection is a service in Azure AD that prevents the use of easy to guess passwords, like Winter2022, Welcome01, Password01, some password with your favorite football team, a fancy car brand, whatever. Passwords that are easy to guess are not accepted in Azure AD. You cannot fool Azure AD Password Protection since it normalizes passwords. So "W!inter2O22" is normalized to "Winter2022", just as "P@ssw0rdO1" is normalized to "Password01".
There's also fuzzy logic built into the product. The password "qwerty" is blocked, but when users try "qwertu" or "werty" it is treated just like "qwerty" and thus it is not accepted.
Microsoft is maintaining a global banned password list for this. It is also possible to use your own custom banned password list. In this custom list you can list your own banned passwords, passwords that you don't want your users to use.
Note: For cloud users the Password Protection service is available as part of the Azure AD Free subscription (comes with Office 365). For synced users you always need an Azure AD P1 license. For the custom banned password lists, you always need an Azure AD P1 license.
The Password Protection service is also available for on-premises Domain Controllers. When implemented, password changes are checked against the banned password lists from Azure Active Directory. No worries, the password change is not sent to Azure Active Directory for verification, but the banned password list is retrieved from Azure Active Directory and checked locally.
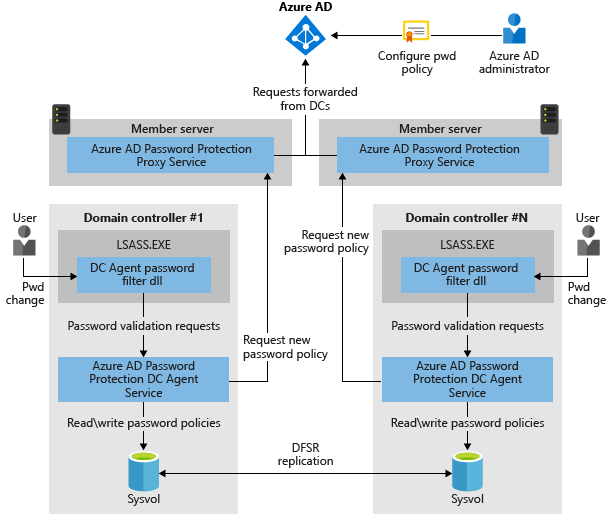
How does this work?
When implementing the Password Protection service in your on-premises environment you must install two services:
- Password Protection Agent – This agent is installed on the Domain Controllers and are used to communicate with (internal) Password Protection proxies.
- Password Protection Proxy – This proxy is installed on one or more member servers in your environment. The password protection agents communicate with the password protection proxies, there's no need for these agents to connect to the internet directly. The password protection proxies request the banned password lists from Azure Active Directory.
This is shown in the following diagram:
The password protection agent and proxy can be downloaded from the Microsoft Download Center.
After installation of the password protection proxy, you need to configure it in Active Directory using the following commands:
PS C:\> Import-Module AzureADPasswordProtectionPS C:\> Register-AzureADPasswordProtectionProxy -AccountUpn 'globaladmin@yourtenant.onmicrosoft.com'
This will create a Service Connection Point (SCP) in Active Directory so that the password protection agents know where to find the proxy. You can use PowerShell to retrieve this SCP from Active Directory by executing the following commands:
PS C:\> $SCP = "serviceConnectionPoint"PS C:\> $Keywords = "{ebefb703-6113-413d-9167-9f8dd4d24468}*"
PS C:\> Get-ADObject -SearchScope Subtree -Filter {objectClass -eq $SCP -and keywords -eq $Keywords}
Of course, you can also use ADSIEdit to view the SCP:
The Active Directory Forest also needs to be registered in Azure Active Directory. To do this, execute the following command:
[PS] C:\> Register-AzureADPasswordProtectionForest -AccountUpn 'globaladmin@yourtenant.onmicrosoft.com'Installing the password protection agent on the on-premises Domain Controllers is just a matter of starting the AzureADPasswordProtectionDCAgentSetup.msi. No further configuration of the protection agent is needed since it will find the password protection proxy from Active Directory. Don't forget to reboot after installing the agent on the Domain Controllers.
Note: The password protection agent and proxy support an in-place upgrade. So, when upgrading the software there is no need to uninstall the old version first.
Testing the Password Protection Service
Changing a password after implementing the password protection service is not different than before. Just use CRTL-ALT-DELETE and change the password. The new password will automatically be checked against the banned password list and if listed on this list an "unable to update the password" message is shown on the screen:
Summary
Weak passwords are a serious attack vector, both on-premises and in Office 365, especially when not using Multi-Factor Authentication. To avoid users using weak and easy to guess passwords, Microsoft has developed the Azure AD Password Protection service. Using a global banned password list and an optional custom banned password list, easy to guess passwords are no longer accepted when changing password. This service is available in Azure AD and using a password protection proxy and agent this functionality is also available in on-premises Active Directory.
I always recommend using this as it is an easy step in improving the security of your accounts.
Active Directory Monitoring and Reporting
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.