Top 10 Best Security Practices for Azure
At Microsoft Ignite 2019 last year Mark Simos, Lead Architect for the Microsoft Cybersecurity...


Microsoft’s own integrated STS in Windows Server named AD FS (Active Directory Federation Service) is still a broadly used mechanism to federate identities with Azure Active Directory. At Ignite 2018, Anand Yadav’s session BRK3226 provided some numbers and 71+ million users actively use AD FS to sign-in to Azure.
As AD FS has been implemented in Azure AD Connect some while ago, the automatic configuration seems to be very easy for the Office 365 Relying Party Trust. However, many SMB’s want single sign-on for all their Office 365 and Azure applications and then the name AD FS often appears. But which sign-in options are available and when should I choose AD FS? The following diagram gives a short overview about the sign-in options:
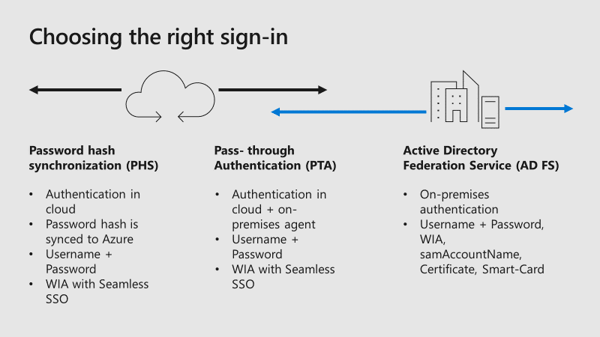
Azure Active Directory did a great step forward the last weeks and months to enable organizations to create (or migrate) custom SAML-based authentication settings for their on-premises applications. Azure AD has already thousands of applications integrated to enable single sign-on with other cloud applications like AWS, Google, Salesforce, and so on. Microsoft provided new tools and documentation to walk you through your app migration experience and show you which apps you can easily connect today.
The National Cyber Security Centre published a blog post last week and gives a new guidance to move to cloud-native authentication. The new recommendation in hybrid environments should prefer native authentication against Azure AD rather than AD FS. Cloud-native authentication in hybrid environments means that you should use seamless SSO with Password Hash Sync. As this recommendation is really great, especially for SMB’s that install and configure AD FS only for Office 365 without any additional security configurations, there are still some requirements for organizations to use AD FS instead of Password Hash Synchronization:
If you want to read more about how to secure your Office 365 environment with AD FS, read my latest blog post . It’s more than install and configure AD FS for your Office 365 environment. You should consider protecting your organization against password spray attacks, AD FS smart lockout, enable multi-factor authentication, and many more.
This blog will explain why passwords are weak and why you should use a password-less sign-in method to access your on-premises and cloud applications.
Also at Ignite 2018, Anand Yadav’s session BRK3226 provided numbers about global threats against Azure AD and common passwords attempted in password spray attacks:
After reading these alarming numbers, you should think about to adjust your organization’s password policy, or even better, deploy a second factor authentication like Azure MFA for all your users. Additional information, like Azure AD Password protection that allows admins to prevent users from securing accounts in Azure AD and Windows Server Active Directory with weak passwords can be found in my other blog post .
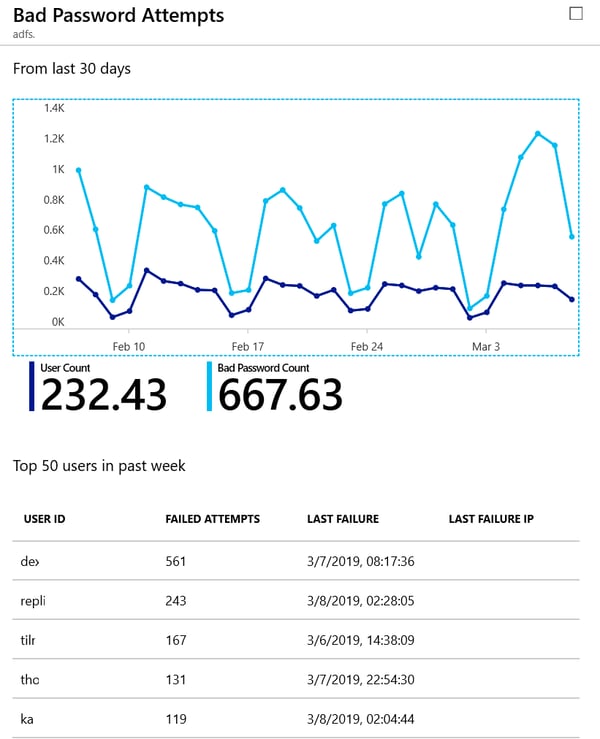
An easy and simple insights in your AD FS infrastructure can be found in the Azure portal under Azure AD Connect Health, implied you did configure it. The below diagram shows bad password attempts to my Office 365 tenant:
(User ID and last failure IP removed for privacy reasons).
AD FS 2016 introduced Azure MFA as primary authentication so that OTP (One Time Passcodes) from the Authenticator app could be used as the first factor. Building on this, with AD FS 2019 you can configure external authentication providers as primary authentication factors. There are two scenarios that can be used:
In AD FS 2019, the external authentication as primary capability means that every external authentication provider become available for primary authentication as well as additional authentication. Once an external provider is enabled for extranet, intranet, or both, it becomes available for users to use. If more than one method is enabled, users will see a choice page and be able to choose a primary method, just as they do for additional authentication. An example for a primary authentication with Windows Hello for Business on an external network, which requires an additional authentication method, you can choose between additional Azure MFA capabilities as shown in the following picture:
There are some prerequisites to your environment to enable external authentication providers as your primary authentication method in AD FS. More information on the prerequisites and how to configure the authentication methods can be found in this Microsoft documentation.
Microsoft did a great job and provided a lot of tools to secure your organization’s environment. Independently for which authentication solution you will decide, you have to protect your accounts for every sign-in method, no matter if it is native cloud-only authentication in Azure AD or on-premises authentication with AD FS.
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.

Dominik is a Microsoft MVP primarily specializing in Microsoft Exchange, Exchange Online and Office 365. Dominik currently works for a German consulting company, AtWork. At atwork, Dominik focuses on designing and building message infrastructures and cloud technologies. Dominik has worked in IT since 2004, primarily with Exchange Server but also has experience with Windows Server, Active Directory, Azure, Office 365, Unified Messaging and various third party products.


At Microsoft Ignite 2019 last year Mark Simos, Lead Architect for the Microsoft Cybersecurity...


Microsoft 365 offers a wide variety of services beyond the full stack of services like Exchange...