Identity Management: Preventing Credential Creep
Identity Management . . . . a fancy term for keeping tabs on credentials with access to our...


Active Directory replication failures are like a leaking water pipe in your wall. You don’t notice anything at first, but by the time you do, there is significant damage. It’s probably not altogether difficult to “repair” AD at this point and stop the "leak", but the damage remains. Monitoring Active Directory replication is essential to catching the little problems before they become major. It all starts with AD object inconsistencies between domain controllers.
As the problem worsens, some users may lose access. Sporadic login failures and account lockouts are especially significant for remote users. Group membership can be affected. This could cause security issues if users are not removed from groups when/as expected. Even Group Policy behavior can be altered. Administrators may experience disjointed AD views, depending on which particular domain controller they are using.
If you have an adequate distribution of domain controllers, the Knowledge Consistency Checker (KCC) tries its best to maintain a functioning replication topology. Its job is to make sure there’s a path from each writable replica to every other name context replica. The KCC creates and deletes the intra-site and intra-site connections as needed. But it can’t function without reliable DNS services, proper time synchronization, and network connectivity. That’s why successful Active Directory monitoring - replication must regularly test the underlying connectivity foundation for AD replication.
A useful diagnostic tool is the REPADMIN command-line utility. REPADMIN /replsummary provides a great overview. The summary can pinpoint any domain controllers that are failing for either inbound or outbound replication. It can’t tell you why the failures occurred, but it’s a good starting point. The /showrepl switch can help diagnose replication failures by giving you information about replication timing and topology. When underlying issues are resolved, the /replicate switch can be used to trigger replication. You can test your repair effort without waiting until the next scheduled replication event. REPADMIN is included as part of Active Directory Domain Services Tools in the Remote Server Administration Tools set.
Another useful tool in the set is DCDIAG. DCDIAG offers almost thirty different tests that can assist in troubleshooting and monitoring AD replication. You can test a single remote server, or all your domain controllers if necessary. Running the DCDIAG command by itself will run all of the tests. Or you can choose selected tests via the /test switch. It’s interesting to note that the Connectivity tests are always run, no matter what specific tests you select. This underscores the importance of monitoring DNS as a key component of Active Directory replication monitoring. Another key player in AD replication is successful time synchronization. You can run w32tm /query /configuration at an admin command prompt to see your current time service settings.
For Powershell users, the AD module for Powershell offers a few options to monitor replication. Get-ADReplicationFailure can be used to list replication failures for a single domain controller, a site, or even the entire forest. Get-ADReplicationPartnerMetadata will pull the inbound replication partners for a server or group of servers. An advantage of using Powershell cmdlets instead of REPADMIN is that the Powershell cmdlets return objects with properties that you could pipe to other commands. You can also perform some DNS diagnostics while you’re at the Powershell prompt.
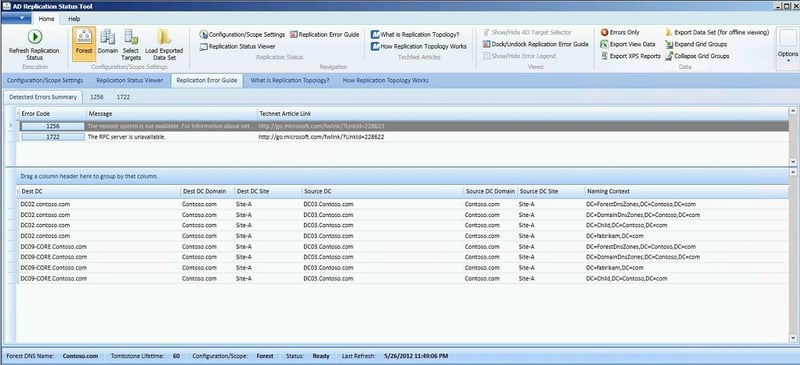
For a GUI-based experience, Microsoft has reinstated the downloadable Active Directory Replication Status tool. The interface includes much of the information from REPADMIN in a graphical dashboard. You can collect the replication status for a specific target, domain, or entire forest. The process begins with an environment discovery that detects all the nodes in your selected scope. Any errors during discovery are displayed. The data is stored in a local folder created just for this purpose. My favorite feature is that a link is offered to the matching Microsoft Docs (Technet) article for each error detected.
If you are an Azure Services Hub subscriber, you might take advantage of the Active Directory On-Demand Assessment. It’s just one of many assessments offered as part of the Services Hub. This “engineer-driven” assessment is a more complex insight into your entire AD environment. As such, it includes a look at DNS and replication across your AD topology.
These are all useful tools and can help you discover the cause of Active Directory replication failures. But this is usually after the damage is already done. It’s much more effective when you can take action at the first sign of trouble. The leaking pipe should have been fixed while it was just a drip. While you could manually run these tools on a consistent basis, it would be impractical and time consuming. Active Directory monitoring replication is best when it’s hands-free and automatic. Synthetic monitoring offers continuous, regular insight into AD replication.
Active Directory is the foundation of your network, and the structure that controls access to the most critical resources in your organization. The ENow Active Directory Monitoring and Reporting tool uncovers cracks in your Active Directory that can cause a security breach or poor end-user experience and enables you to quickly identify and remove users that have inappropriate access to privileged groups (Schema Admins, Domain Administrators). While ENow is not an auditing software, our reports reduce the amount of work required to cover HIPAA, SOX, and other compliance audits.
Access your FREE 14-day trial to accelerate your security awareness and simplify your compliance audits. Includes entire library of reports.



Identity Management . . . . a fancy term for keeping tabs on credentials with access to our...


The rising need for flexibility and ease of integration with other systems, either on-premises...