AAD Roles for EXO Administrators
In one of my other articles “Accessing Exchange Online Objects” I outlined how you can interact with these objects. When you need to scope apps with application permissions to a subset of mailboxes, we can use ApplicationAccessPolicies as outlined here by Microsoft.
As of today, only the following permissions are supported by these policies:
- Read
- ReadBasic
- ReadBasic.All
- ReadWrite
- Send
- Read
- ReadWrite
- Read
- ReadWrite
- Read
- ReadWrite
Note: There is no support for Exchange Web Services (EWS), Exchange ActiveSync (EAS) or IMAP4!
Use case
Whenever you configure an app with application permissions, you will need a user with Global Admin role assigned to grant admin consent. Application Administrator or Cloud Application Administrator role is not sufficient as those roles cannot grant admin consent for Microsoft Graph and Azure AD Graph as outlined here.
Now think of larger companies, with several teams or that follow the security principals and perform segregation of duties.
You will most likely have a different account for a Global Admin than for the Exchange Administrator. Or the natural person with Global Admin role, has no knowledge on how to create an ApplicationAccessPolicy in Exchange Online (which is absolutely fine!).
Can you see the dilemma? Wouldn’t it be perfect to grant a subset of administrators with Exchange Administrator roles the permission to grant admin consent ONLY for certain permissions? This would disburden the Global Administrator from this task.
There is currently a preview available, which allows Custom administrator roles in Azure Active Directory. The details are explained here, but the interesting part for our scenario is described here:
You can create a PermissionGrantPolicy and add this as RolePermission to your custom role.
How to create a custom role?
To create a custom role with the specific settings, you need to use the AzureADPreview PowerShell module.
First, we need to sign-in with Global Admin privileges to create the necessary settings:
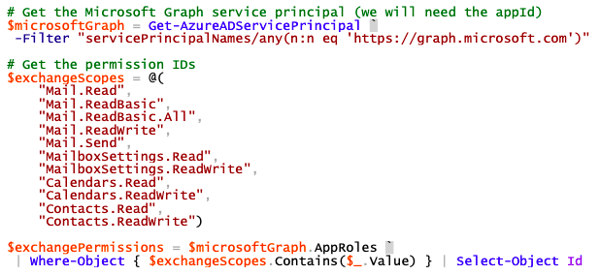
- Get the SPN for Microsoft Graph
- Retrieve the IDs of the supported permissions
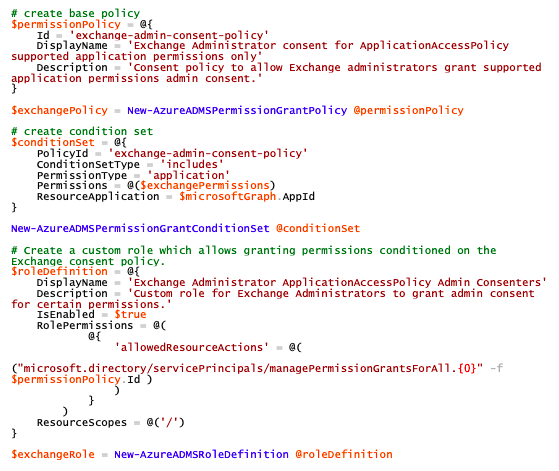
- Create a PermissionGrantPolicy (New-AzureADMSPermissionGrantPolicy)
- Create a PermissionGrantConditionSet, which combines previously retrieved permission and Microsoft Graph IDs (New-AzureADMSPermissionGrantConditionSet)
- Create a RoleDefinition, which contains the PermissionGrantPolicy (New-AzureADMSRoleDefinition)
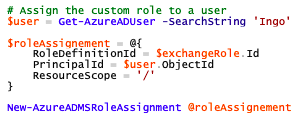
- Assign the role to a user (New-AzureADMSRoleAssignment)
This sounds like a lot of things you have to care about, but with PowerShell it’s not too difficult. Here’s the code for the steps above.
Get Microsoft Graph SPN and IDs for supported permissions:
Create policy, condition set and create the custom role, which contains all information:
In the final step assign the role to a user:
The assignment using New-AzureADMSRoleAssignment will result in a permanent role-assignment. If you are using Azure AD Privileged Identity Management (PIM) use the following code:
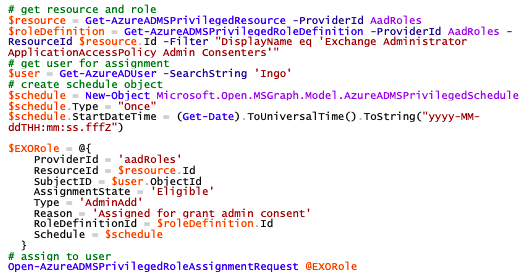
With this you should be good to go, but there are a few things to mention:
- As of now, you cannot assign a custom role to a group.
- The only ways for administrators, which have this role assigned, to grant admin consent are the following:
a. Using UI in Azure AD Portal as described here in Enterprise apps.
Note: Grant admin consent using App registration as described here won’t be available.
b. Using a constructed URL as described here (this is the same as described in point a, besides the fact that you have to construct the URL by yourself!).
- If there is any permission other than the supported ones configured (e.g.: User.Read), the administrator will not be able to grant admin consent.
- Microsoft Graph using oAuth2PermissionGrant resource type
Conclusion
I hope the scenario described above will help you. If this doesn't exactly match your needs, you might still want to have a look into these capabilities and modify the code as needed.
Monitor Your Hybrid - Office 365 Environment with ENow
ENow’s Office 365 Monitoring solution is like your own personal outage detector that pertains solely to you environment. ENow’s solution monitors all crucial components including your hybrid servers, the network, and Office 365 from a single pane of glass. Knowing immediately when a problem happens, where the fault lies, and why the issue has occurred, ensures that any outages are detected and solved as quickly as possible.
Learn more