On February 12, 2019, Microsoft released its quarterly updates for Exchange server, and in this case Microsoft has released Exchange 2019 CU1, Exchange 2016 CU12, Exchange 2013 CU22 and Exchange 2010 SP3 Update Rollup 26 (although the latter is not really a quarterly update).
Looking at the release date of Exchange 2019 it took more time before CU1 was released, this is caused to align the cadence with other versions and other applications.
The updates are not fancy and not sexy this time, but they do bring a very important security fix. You've likely heard about the recent elevation of privilege vulnerability in Exchange server. A Dutch researcher working for a security company called Fox IT in The Netherlands found that it is quite simple to gain administrative permissions using the NTLM relay option, and he did this using a straight forward EWS push subscription call. You can read more about this issue on his blog post. There were some mitigations available like LDAP signing, SMB signing or implementing an EWSMaxSubscriptions throttling policy, but these are all mitigation factors. The issue itself is now fixed in Exchange 2019 CU1, Exchange 2016 CU12 and Exchange 2013 CU22. To apply the changes in the Exchange permissions model, and thus apply the fixes for the vulnerability you must run the Setup /PrepareAD command. If you have multiple versions of Exchange server in your Active Directory forest, you must run this command from the highest version. For a mixed Exchange 2016 and Exchange 2019 environment this is shown in the following screenshot.
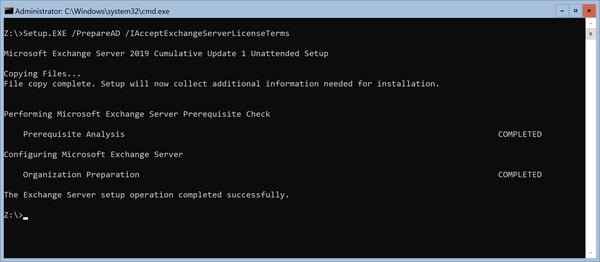
Running the /PrepareAD is sufficient to fix the vulnerability in your Exchange environment.
Note - If you are still running Exchange 2010, applying Update Rollup 26 is not sufficient to fix the vulnerability. You also need to apply the (directory) changes as outlined in the Microsoft KB article KB4490059.
Another change introduced in these quarterly updates in an architectural change in the Web Services Push notification mechanism. This is considered as a critical security patch, and customers are advised to implement this as soon as possible, after they’ve considered the impact of the changes (when it comes to clients using the push notifications). After applying the update to an Exchange server, Microsoft recommends to change the Computer password. This can be achieved using the Reset-ComputerMachinePassword PowerShell command, or using the reset option in the Active Directory Users and Computers MMC snap-in.
Installing the Cumulative Updates is straightforward. First you must update Active Directory using the following commands:
Setup.exe /PrepareSchema /IAcceptExchangeServerLicenseTerms
Setup.exe /PrepareAD /IAcceptExchangeServerLicenseTerms
Setup.exe /PrepareDomain /IAcceptExchangeServerLicenseTerms
When the changes are applied to Active Directory, the individual Exchange servers can be updated.
Before installing the updates mentioned in this article, make sure you install the Visual C++ 2012 runtime prerequisite software. If omitted, it will result in a setup failure.
To upgrade the Exchange server, I personally always use an unattended upgrade since it is the most efficient way of upgrading. You can do this using the following command:
Setup.exe /mode:upgrade /IAcceptExchangeServerLicenseTerms
Running this command in shown in the following screenshot:
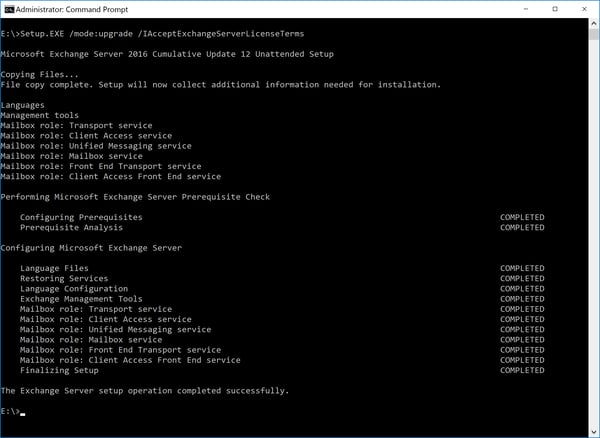
If you are running Exchange in a Database Availability Group, you have to suspend the DAG node you want to upgrade. Although the following blog post is written for upgrading an Exchange 2013 DAG, the process did not change and you can safely use the PowerShell commands mentioned in this article.
Important note - When you are running an Exchange hybrid configuration, you have to make sure you’re running a supported version on-premises for your hybrid configuration. Supported versions here are Exchange 2013 CU22, Exchange 2016 CU11 or CU12, Exchange 2019 RTM or CU1 or Exchange 2010 SP3 Update Rollup 26.
And as always, please test the new updates thoroughly in your test environment, and make sure you fully understand the (security) implication that come with these updates.
More information and all downloads are available on the following locations:
|
Exchange 2019 CU1
|
Exchange 2016 CU12
|
|
Exchange 2013 CU22
|
Exchange 2010 SP3 Update Rollup 26
|
Exchange 2010 SP3 Update Rollup 26 will also be available via Windows Update.
Monitor Exchange with Mailscape
Watch all aspects of your Exchange environment from a single pane of glass: client access, mailbox, and Edge servers; DAGs and databases; network, DNS, and Active Directory connectivity; Outlook, ActiveSync, and EWS client access.
Learn more